Kiwi Syslog Server是一款应用于Windows系统的系统日志守护进程,能够接收并记录系统日志,各种设备的SYSLOG消息,内置丰富的日志记录选项,能详细记录各种防火墙日志,并进行筛选分析。
本文主要介绍Kiwi Syslog Server配置Active Directory集成身份认证。
安装教程:
【逗老师带你学IT】Kiwi Syslog Server安装教程
https://blog.csdn.net/ytlzq0228/article/details/104827014
在多用户环境中使用Kiwi Syslog时,使用Active Directory集成认证有助于用户账号授权的管理。这样,您可以控制谁可以通过AD认证访问Kiwi Syslog Web Access界面,避免管理非常多个本地帐户带来的麻烦。
设置非常简单。
@[TOC]
一、Kiwi Syslog Web Active Directory集成的前提条件:
1、Kiwi中的AD集成使用TCP端口389上的LDAP连接到域控制器,提前确认Kiwi Sylog Server跟域控之间的TCP 389端口正常通信。
2、Kiwi Syslog的服务器必须加入用于认证的AD域。
二、Active Directory准备工作
1、在Active Directory中创建一个用户组或安全组,以用于控制对Kiwi Syslog的身份验证,或者选择已有的用户组或安全组,例如IT部门群组。
2、将授权访问Kiwi的用户帐户添加到上面创建的安全组中,您希望它们能够登录到Kiwi Syslog Web Client。
三、Kiwi Syslog Web Access中设置Active Director的步骤
1、登录Kiwi Syslog Web Access
使用管理员帐户登录Kiwi Syslog Web Access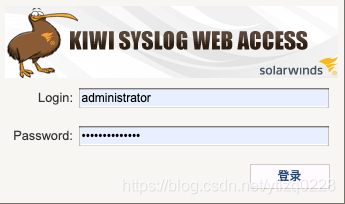
2、Active Directory集成配置
打开“ Admin”->“ Active Directory Setting”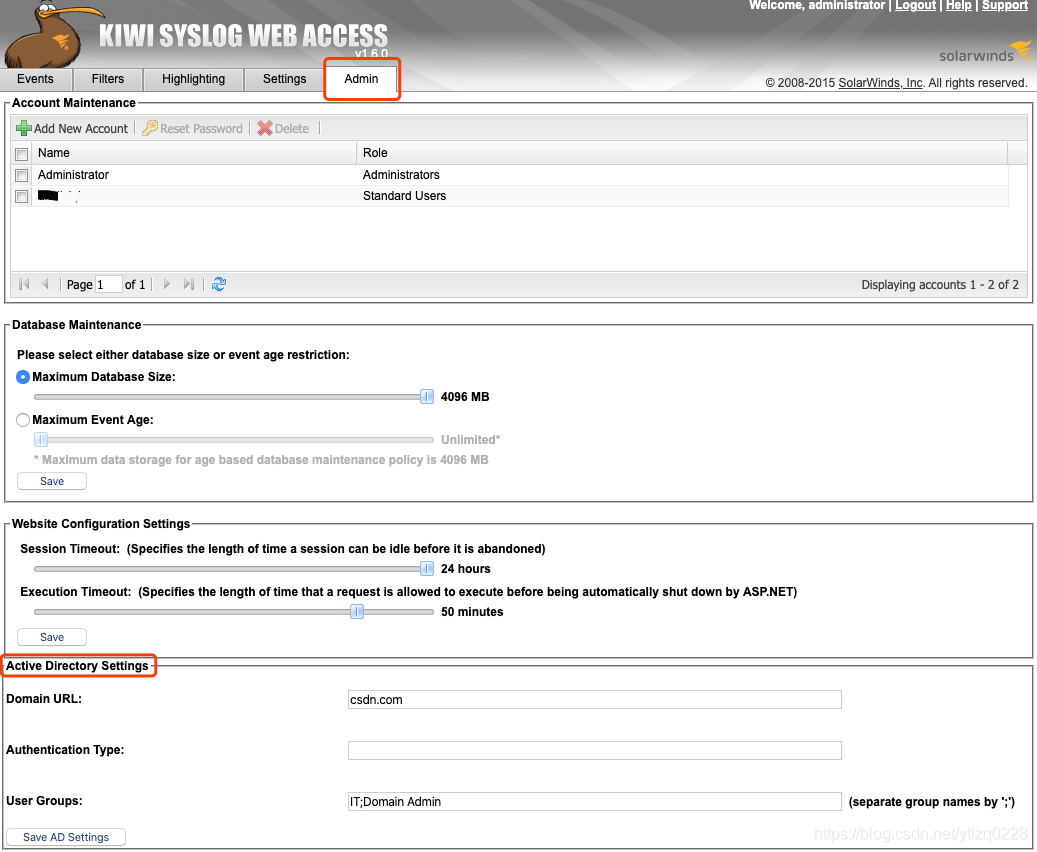
3、Active Directory认证配置参数
3.1、输入您的Active Directory环境的域URL
如果是AD域控制器,输入AD域控服务器DNS域名
如:csdn.com
如果是其他LDAP服务器,需要输入完整的LDAP URL
如ldap:// DomainController1:389 / ou = Groups,dc = npgdom,dc = com
3.2、将身份验证类型留为空白,默认为Secure。如果对LDAP使用其他身份验证类型,请进行更改。如果不知道这项什么意思,请将其留空。
3.3、在“用户组”字段中输入您在AD中创建的用户组的名称。可以使用多个用户组并用分号分隔。
3.4、点击保存设置。
查看AD域控制器的Windows防火墙,和沿途所有防火墙,确认运行Kiwi Syslog Server可以访问AD域控的TCP 389端口。
四、测试使用域帐户登录Kiwi Syslog Web访问
1、注销登录当前管理员账号,或新开一个浏览器小号窗口。
2、使用Domain\username的格式进行登录,比如CSDN\doulaoshi。注意如果使用域账号登录,必须添加域名前缀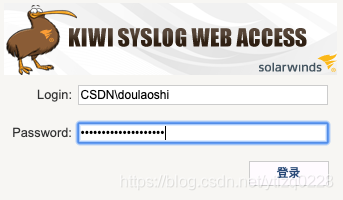
3、新用户第一次登录会出现一条提示,不要慌,这不是报错!
第一次登录系统需要在Kiwi Syslog中创建一个同名的本地帐户,再次登录即可以正常登录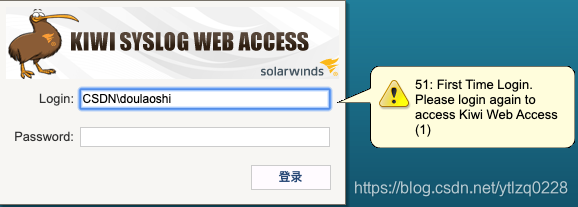
管理员可以看到用户管理中,新添加了一个域账户。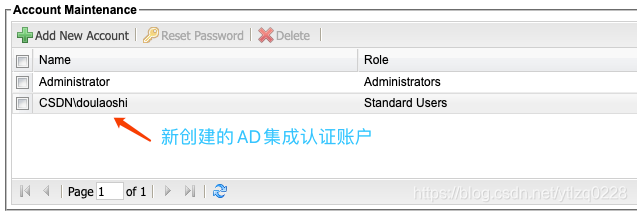
五、域帐户登录Kiwi Syslog Web权限
域账户登录之后的权限是标准用户权限,可以查询所有的日志,编辑过滤器,但是无权限访问Admin选项卡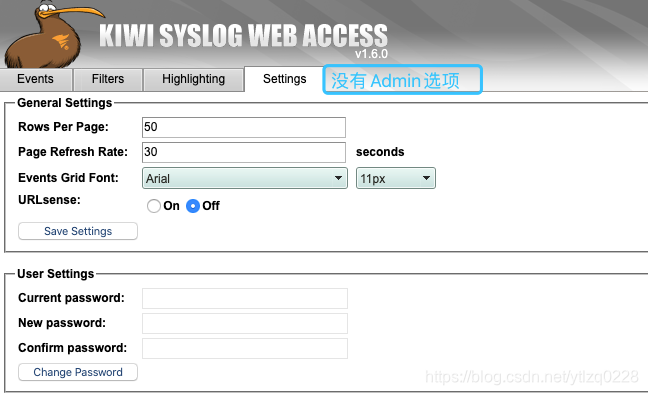
六、参考资料
参考资料
1.如何集成Kiwi与活动目录:Network Pro Guide | How to Integrate Kiwi Syslog Web Access with Active Directory
官方手册
2.Kiwi web server AD认证设置:Solarwinds | Active Directory Authentication setting for Kiwi Syslog Server Web Access
3.Kiwi web Access AD认证:Solarwinds | Kiwi SyslogTM Web Access - AD Authentication
| 所有支持的LDAP认证类型: Auth types |
description |
|---|---|
| Anonymous | No authentication is performed. |
| Delegation | Enables Active Directory Services Interface (ADSI) to delegate the user's security context, which is necessary for moving objects across domains. |
| Encryption | Attaches a cryptographic signature to the message that both identifies the sender and ensures that the message has not been modified in transit. |
| FastBind | Specifies that ADSI will not attempt to query the Active Directory Domain Services objectClass property. Therefore, only the base interfaces that are supported by all ADSI objects will be exposed. Other interfaces that the object supports will not be available. A user can use this option to boost the performance in a series of object manipulations that involve only methods of the base interfaces. However, ADSI does not verify if any of the request objects actually exist on the server. |
| None | Equates to zero, which means to use basic authentication (simple bind) in the LDAP provider. |
| ReadonlyServer | For a WinNT provider, ADSI tries to connect to a domain controller. For Active Directory Domain Services, this flag indicates that a writable server is not required for a serverless binding. |
| Sealing | Encrypts data using Kerberos. The Secure flag must also be set to use sealing. |
| Secure | Requests secure authentication. When this flag is set, the WinNT provider uses NTLM to authenticate the client. Active Directory Domain Services uses Kerberos, and possibly NTLM, to authenticate the client. When the user name and password are a null reference (Nothing in Visual Basic), ADSI binds to the object using the security context of the calling thread, which is either the security context of the user account under which the application is running or of the client user account that the calling thread is impersonating. |
| SecureSocketsLayer | Attaches a cryptographic signature to the message that both identifies the sender and ensures that the message has not been modified in transit. Active Directory Domain Services requires the Certificate Server be installed to support Secure Sockets Layer (SSL) encryption. |
| ServerBind | If your ADsPath includes a server name, specify this flag when using the LDAP provider. Do not use this flag for paths that include a domain name or for server less paths. Specifying a server name without also specifying this flag results in unnecessary network traffic. |
| Signing | Verifies data integrity to ensure that the data received is the same as the data sent. The Secure flag must also be set to use signing. |
往期回顾:
【逗老师带你学IT】Kiwi Syslog Server安装和配置教程
【逗老师带你学IT】Kiwi Syslog Web Access与Active Directory集成认证
【逗老师带你学IT】vMware ESXi 6.7合并第三方硬件驱动
【逗老师带你学IT】Windows Server Network Policy Service(NPS)记账与审计
【逗老师带你学IT】Windows Server NPS服务构建基于AD域控的radius认证
【逗老师带你学IT】AD域控和freeradius集成认证环境,PAP,MSCHAPV2
【逗老师带你学IT】PRTG监控系统配合树莓派采集企业内部无线网络质量
【逗老师带你学IT】深信服SSL远程接入与深信服行为审计同步登陆用户信息
【逗老师带你学IT】PRTG监控系统合并多个传感器通道数据
【逗老师带你学IT】PRTG监控系统通过企业微信推送告警消息
来源:oschina
链接:https://my.oschina.net/u/4286012/blog/4714343