环境:XP sp2 中文版
老规矩,上代码
(代码来自0day2电子资料->02栈溢出原理与实践->2_4_overflow_code_exec.c)
/*****************************************************************************
To be the apostrophe which changed "Impossible" into "I'm possible"!
POC code of chapter 2.4 in book "Vulnerability Exploit and Analysis Technique"
file name : stack_overflow_exec.c
author : failwest
date : 2006.10.1
description : demo show how to redirect EIP to executed extra binary code in buffer
Noticed : should be complied with VC6.0 and build into debug version
the address of MessageboxA and the start of machine code in buffer
have to be make sure in file "password.txt" via runtime debugging
version : 1.0
E-mail : failwest@gmail.com
Only for educational purposes enjoy the fun from exploiting :)
******************************************************************************/
#include <stdio.h>
#include <windows.h>
#define PASSWORD "1234567"
int verify_password (char *password)
{
int authenticated;
char buffer[44];
authenticated=strcmp(password,PASSWORD);
strcpy(buffer,password);//over flowed here!
return authenticated;
}
main()
{
int valid_flag=0;
char password[1024];
FILE * fp;
LoadLibrary("user32.dll");//prepare for messagebox
if(!(fp=fopen("password.txt","rw+")))
{
exit(0);
}
// fscanf(fp,"%s",password);//遇到0B就断了
fread(password,1,sizeof(password),fp);
valid_flag = verify_password(password);
if(valid_flag)
{
printf("incorrect password!\n");
}
else
{
printf("Congratulation! You have passed the verification!\n");
}
fclose(fp);
}---------------------------------------------------------------------------------------------------
这里说明下,原版作者读入password用的fscanf,但因为我的环境里有0的bad chars(0B 05 05),所以读到一部分就读不了了。于是我换成了fread 
---------------------------------------------------------------------------------------------------
当函数执行到verify_password 的retn时
OD里如下
1.

2.由于返回地址被覆盖成了jmp esp 指令地址,单步返回到达了jmp esp,我这里用的对Windows 2000、XP、2003中文通杀地址0x7ffa4512

3.由于esp指向到shellcode,所以接着shellcode被执行

-----------------------------------------------昏割线----------------------------------------------
整个原理可用下图说明: (自己用wps的excel功能画的。。。丑陋的图。。。)
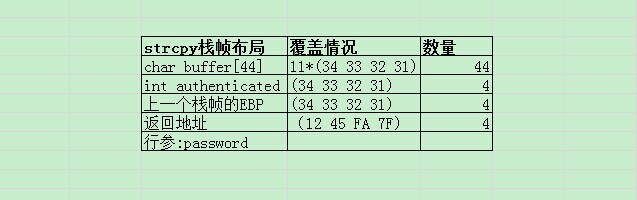
简单总结:跳板技术不限于jmp esp, mov eax/esp, jmp eax 均可。如何构造缓冲区是这门技术的重点.
ps:今天太累了,所以本文写得很粗糙,可能讲得不清楚,后面再把一些细节和原理补上。
再ps:开源中国的编辑器编辑图片的功能用得不爽啊!
来源:oschina
链接:https://my.oschina.net/u/1044317/blog/269289