组网需求
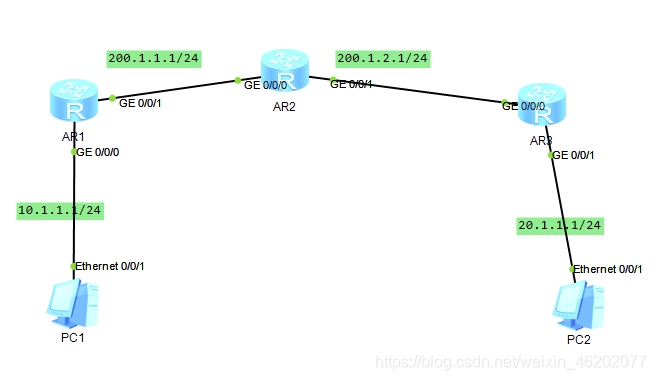
如图1所示,在Router1和Router3之间建立一个安全隧道,对PC 1代表的子网(10.1.1.x)与PC2代表的子网(20.1.1.x)之间的数据流进行安全保护。安全协议采用ESP协议,加密算法采用DES,认证算法采用SHA2-258
拓扑图设计
关键配置r1和r3
ike local-name huawei1 **–本地命名
acl number 3000
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 20.1.1.0 0.0.0.255 **–acl的控制让内网的网段能够去另一个内网的网段
#ipsec proposal a**–ipsec的安全提议命名为a
esp authentication-algorithm sha1 **–选择sha1算法
ike proposal 1**–ike 的提议为默认1
encryption-algorithm **–aes-cbc-128 选择aes-cbc-128
ike peer supb v1**–配置ike的对端supb 版本v1
exchange-mode aggressive
pre-shared-key cipher %lGY\M:XUH;9*F(P/^!f:,.2n%
ike-proposal 1
local-id-type name
remote-name huawei2
local-address 200.1.1.1 --本地地址都是公网口地址
remote-address 200.1.2.2–对端地址
ipsec policy map1 10 isakmp*–ipsec的调用在map1 优先级为10
security acl 3000
ike-peer supb
proposal a
interface GigabitEthernet0/0/0
ip address 10.1.1.2 255.255.255.0
interface GigabitEthernet0/0/1
ip address 200.1.1.1 255.255.255.0
ipsec policy map1
ip route-static 20.1.1.0 255.255.255.0 200.1.1.2 *–让内网能去公网的静态路由
ip route-static 200.1.2.0 255.255.255.0 200.1.1.2–让两端公网的网络能互通
r3配置与r1相似,就不解释了。
ip route-static 10.1.1.0 255.255.255.0 200.1.2.1
ip route-static 200.1.1.0 255.255.255.0 200.1.2.1
interface GigabitEthernet0/0/0
ip address 200.1.2.2 255.255.255.0
ipsec policy map1
interface GigabitEthernet0/0/1
ip address 20.1.1.2 255.255.255.0
ike local-name huawei2
set cpu-usage threshold 80 restore 75
acl number 3000
rule 5 permit ip source 20.1.1.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
ipsec proposal a
esp authentication-algorithm sha1
ike proposal 1
encryption-algorithm aes-cbc-128
ike peer supa v1
exchange-mode aggressive
pre-shared-key cipher %lGY\M:XUH;9*F(P/^!f:,.2n%
ike-proposal 1
local-id-type name
remote-name huawei1
local-address 200.1.2.2
remote-address 200.1.1.1
ipsec policy map1 10 isakmp
security acl 3000
ike-peer supa
proposal a
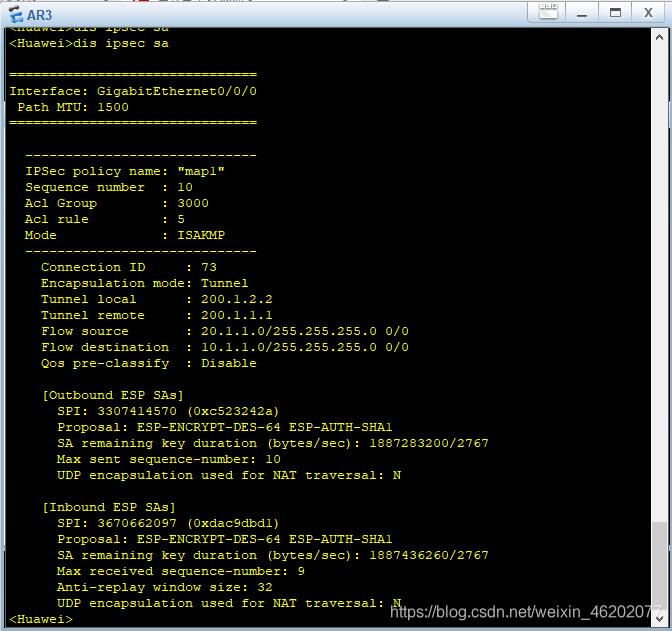
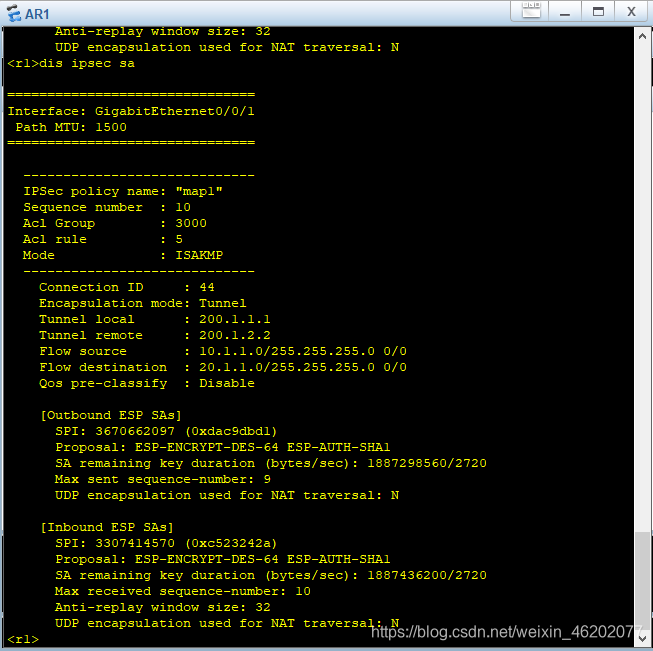
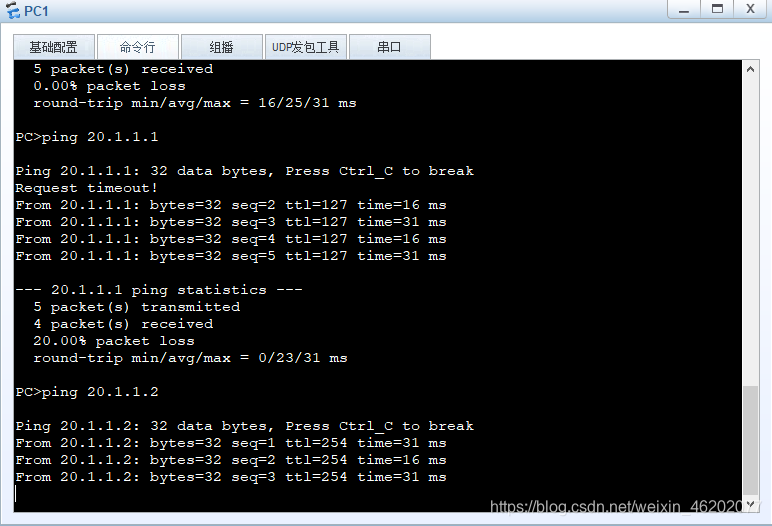
验证结果
来源:CSDN
作者:joker_菜玩
链接:https://blog.csdn.net/weixin_46202077/article/details/104017890