drf的三大认证
</h1>
<div class="clear"></div>
<div class="postBody">
目录
三大认证任务分析
- 认证模块:校验用户是是否登陆
self.perform_authentication(request)
- 权限模块:校验用户是否拥有权限
self.check_permissionsn(request)
- 频率模块:访问接口的次数在设定的时间范围内是否过快(配置访问频率、缓存计次、超次后需要等待的时间)
self.check_throttles(request)
auth组件的认证权限六表
也就是基于角色的访问控制:基于角色的访问控制(RBAC)是实施面向企业安全策略的一种有效的访问控制方式。
Django框架采用的是RBAC认证规则,RBAC认证规则通常会分为 三表规则、五表规则,Django采用的是六表规则
- 三表:用户表、角色表、权限表
- 五表:用户表、角色表、权限表、用户角色关系表、角色权限关系表
- 六表:用户表、角色表、权限表、用户角色关系表、角色权限关系表、用户权限关系表
举个栗子:看图说话

所以我们需要建立关联表(python中是六张表)

我们在实际开发中可能要重写六表
在python中的数据库中会有这六张表eg:用户表中会有用户名、密码、是否是超级管理员、是否是活跃用户等
在auth_permission中的Content_type:给Django中的所有模块中的所有表进行编号存储到Content_type中
# 应用一:权限表的权限是操作表的,所有在权限表中有一个content_type表的外键,标识该权限具体操作的是哪张表
# 应用二:价格策略
"""
Course:
name、type、days、price、vip_type
基础 免费课 7 0
中级 学位课 180 69
究极 会员课 360 至尊会员
以上的这张课表有大量字段重复以及空值非常麻烦,所以我们需要拆表甚至用到content_type
Course:
name、type、days、content_type_id
基础 免费课 7 null
中级 学位课 180 1
究极 会员课 360 2
content_type表(Django提供)
id、app_label、model
1 app01 course_1
2 app01 course_2
app01_course_1 #价格策略一表(字段不一样)
id、price
app01_course_2 #价格策略二表(字段不一样)
id vip_type
"""
自定义User表分析
注意:
1)auth认证6表必须在第一次数据库迁移前确定,第一次数据库迁移完成
2)完成数据库迁移,出现了auth的用户迁移异常,需要删除的数据库迁移文件有User表所在的自定义应用下的、admin组件下的、auth组件下的表删除了
源码分析

认证与权限工作原理
源码分析
APIView下的dispatch方法中的initial方法中含有三大认证:
self.perform_authentication(request)
self.check_permissions(request)
self.check_throttles(request)
APIView下有配置视图类的三大认证

auth组件的校验规则有三点如下图:

session认证是从cookies中去拿
认证模块工作原理
- 继承BaseAuthentication类,重写authenticate方法
- 认证规则(authenticate方法实现体):
- 没有携带认证信息,直接返回None => 游客
- 有认证信息,校验失败,抛异常 => 非法用户
- 有认证信息,校验出User对象 => 合法用户
权限模块工作原理
- 继承BasePermission类,重写has_permission方法
- 权限规则(has_permission方法实现体):
- 返回True,代表有权限
- 返回False,代表无权限
admin关联自定义用户表
自定义认证、权限类
admin中的操作

用户群查接口权限分析
urls.py:
url(r'^users/$', views.UserListAPIView.as_view()) #群查接口
views.py:
from rest_framework.generics import ListAPIView
from . import models, serializers
# 查看所有用户信息,前提:必须是登录的超级管理员
#这里要分析Token源码
from utils.authentications import TokenAuthentication
from utils.permissions import SuperUserPermission
class UserListAPIView(ListAPIView):
# 同电商网站,多接口是不需要登录的,少接口需要登录,使用在需要登录的接口中完成局部配置,进行局部接口校验
authentication_classes = [TokenAuthentication]
permission_classes = [SuperUserPermission]
queryset = models.User.objects.filter(is_active=<span class="hljs-keyword">True</span>, is_superuser=<span class="hljs-keyword">False</span>).all()
serializer_class = serializers.UserModelSerializer
<span class="hljs-function"><span class="hljs-keyword">def</span> <span class="hljs-title">get</span><span class="hljs-params">(self, request, *args, **kwargs)</span>:</span> <span class="hljs-comment">#如果你想重写状态码</span>
response = self.list(request, *args, **kwargs)
<span class="hljs-keyword">return</span> APIResponse(data=response.data)</code></pre>
serializer.py中
from rest_framework import serializers
from rest_framework.serializers import ModelSerializer, ValidationError
from . import models
class UserModelSerializer(ModelSerializer):
class Meta:
model = models.User
fields = ('username', 'email', 'mobile') #还有一些信息你也可以提供
附:

自定义认证类
views.py中
class UserListAPIView(ListAPIView):
# 同电商网站,多接口是不需要登录的,少接口需要登录,使用在需要登录的接口中完成局部配置,进行局部接口校验
authentication_classes = [TokenAuthentication]
permission_classes = [SuperUserPermission]
pass
# 登录接口:如果是超级管理员登录,返回一个可以交易出超级管理员的token字符串
# 只要有用户登录,就可以返回一个与登录用户相关的token字符串 => 返回给前台 => 签发token => user_obj -> token_str
新建一个文件authentications.py
#自定义认证类
"""
认证模块工作原理
1)继承BaseAuthentication类,重写authenticate方法
2)认证规则(authenticate方法实现体):
没有携带认证信息,直接返回None => 游客
有认证信息,校验失败,抛异常 => 非法用户
有认证信息,校验出User对象 => 合法用户
"""
from rest_framework.authentication import BaseAuthentication
from rest_framework.exceptions import AuthenticationFailed
class TokenAuthentication(BaseAuthentication):
prefix = 'Token' #自定义一个反爬
<span class="hljs-function"><span class="hljs-keyword">def</span> <span class="hljs-title">authenticate</span><span class="hljs-params">(self, request)</span>:</span>
<span class="hljs-comment"># 拿到前台的token</span>
auth = request.META.get(<span class="hljs-string">'HTTP_AUTHORIZATION'</span>)
<span class="hljs-comment"># 没有返回None,有进行校验</span>
<span class="hljs-keyword">if</span> <span class="hljs-keyword">not</span> auth:
<span class="hljs-keyword">return</span> <span class="hljs-keyword">None</span>
auth_list = auth.split()
<span class="hljs-keyword">if</span> <span class="hljs-keyword">not</span> (len(auth_list) == <span class="hljs-number">2</span> <span class="hljs-keyword">and</span> auth_list[<span class="hljs-number">0</span>].lower() == self.prefix.lower()):
<span class="hljs-keyword">raise</span> AuthenticationFailed(<span class="hljs-string">'非法用户'</span>)
token = auth_list[<span class="hljs-number">1</span>]
<span class="hljs-comment"># 校验算法</span>
user = _get_obj(token)
<span class="hljs-comment"># 校验失败抛异常,成功返回(user, token)</span>
<span class="hljs-keyword">return</span> (user, token)
# 校验算法(认证类)与签发算法配套
"""
拆封token:一段 二段 三段
用户名A:b64decode(一段)
用户主键B:b64decode(二段)
碰撞解密:md5(用户名A+用户主键B+服务器秘钥) == 三段
服务器秘钥是一个固定的字符串在settings中
"""
import base64, json, hashlib
from django.conf import settings
from api.models import User
def _get_obj(token):
token_list = token.split('.')
if len(token_list) != 3:
raise AuthenticationFailed('token异常')
username = json.loads(base64.b64decode(token_list[0])).get('username')
pk = json.loads(base64.b64decode(token_list[1])).get('pk')
md5_dic = {
<span class="hljs-string">'username'</span>: username,
<span class="hljs-string">'pk'</span>: pk,
<span class="hljs-string">'key'</span>: settings.SECRET_KEY
}
<span class="hljs-keyword">if</span> token_list[<span class="hljs-number">2</span>] != hashlib.md5(json.dumps(md5_dic).encode()).hexdigest():
<span class="hljs-keyword">raise</span> AuthenticationFailed(<span class="hljs-string">'token内容异常'</span>)
user_obj = User.objects.get(pk=pk, username=username)
<span class="hljs-keyword">return</span> user_obj</code></pre>
认证类的认证核心规则
def authenticate(self, request):
token = get_token(request)
try:
user = get_user(token) # 校验算法
except:
raise AuthenticationFailed()
return (user, token)
自定义权限类
新建一个文件夹Permission.py
# 自定义权限类
"""
权限模块工作原理
1)继承BasePermission类,重写has_permission方法
2)权限规则(has_permission方法实现体):
返回True,代表有权限
返回False,代表无权限
"""
from rest_framework.permissions import BasePermission
class SuperUserPermission(BasePermission):
def has_permission(self, request, view):
return request.user and request.user.is_superuser
前后台分离登陆接口
views.py
# 登录接口:如果是超级管理员登录,返回一个可以交易出超级管理员的token字符串
# 只要有用户登录,就可以返回一个与登录用户相关的token字符串 => 返回给前台 => 签发token => user_obj -> token_str
from rest_framework.generics import GenericAPIView
class LoginAPIView(APIView):
# 登录接口一定要做:局部禁用 认证 与 权限 校验
authentication_classes = []
permission_classes = []
def post(self, request, *args, **kwargs):
serializer = serializers.LoginModelSerializer(data=request.data)
# 重点:校验成功后,就可以返回信息,一定不能调用save方法,因为该post方法只完成数据库查操作
# 所以校验会得到user对象,并且在校验过程中,会完成token签发(user_obj -> token_str)
serializer.is_valid(raise_exception=True)
return APIResponse(data={
'username': serializer.user.username,
'token': serializer.token
})
serializers.py
from django.contrib.auth import authenticate
class LoginModelSerializer(ModelSerializer):
# username和password字段默认会走系统校验,而系统的post请求校验,一定当做增方式校验,所以用户名会出现 重复 的异常
# 所以自定义两个字段接收前台的账号密码
usr = serializers.CharField(write_only=True)
pwd = serializers.CharField(write_only=True)
class Meta: #非标准接口下面的反序列化
model = models.User
fields = ('usr', 'pwd')
def validate(self, attrs): #全局钩子
usr = attrs.get('usr')
pwd = attrs.get('pwd')
try:
user_obj = authenticate(username=usr, password=pwd)
except:
raise ValidationError({'user': '提供的用户信息有误'})
# 拓展名称空间
self.user = user_obj
# 签发token
self.token = _get_token(user_obj)
return attrs
# 自定义签发token
# 分析:拿user得到token,后期还需要通过token得到user
# token:用户名(base64加密).用户主键(base64加密).用户名+用户主键+服务器秘钥(md5加密)
# eg: YWJj.Ao12bd.2c953ca5144a6c0a187a264ef08e1af1
频率认证源码分析
APIView ---》dispatch方法---》self.initial(request, *args, **kwargs)---》 self.check_throttles(request)
#重新访问这个接口的时候,都会重新调用这个方法,每次访问都会throtttle_durations=[]置空
def check_throttles(self, request):
"""
Check if request should be throttled.
Raises an appropriate exception if the request is throttled.
"""
#比如一分钟只能访问三次,第一,二,三次访问的时候都没有限制,第四次访问就会制
#限次的持续时间,还有多少秒才能接着访问这个接口
throtttle_durations=[]
# self.get_throttles()全局或局部配置的类
for throttle in self.get_throttles():
#allow_request允许请求返回True,不允许就返回False,为false时成立,
if not throttle.allow_request(request, self):
#throttle.wait()等待的限次持续时间
self.throttled(request, throttle.wait())
# 第四次限制,有限制持续时间才会走这部
if throttle_durations:
durations = [
duration for duration in throttle_durations
if duration is not None
]
duration = max(durations, default=None)
self.throttled(request, duration)
这说明我们自定义类要重写allow_request(request, self)和wait(),因为throttle调用了
点击 self.get_throttles()查看
def get_throttles(self):
"""
Instantiates and returns the list of throttles that this view uses.
"""
return [throttle() for throttle in self.throttle_classes]
点击 self.throttle_classes
throttle_classes = api_settings.DEFAULT_THROTTLE_CLASSES
throttle_classes跟之前一样可局部配置throttle_classes=[] ,可全局配置settings文件中配置
到drf资源文件settings.py文件中的APISettings类中查看默认配置:ctrl+f键查找DEFAULT_THROTTLE_CLASSES
'DEFAULT_THROTTLE_CLASSES': [],#所以说任何接口都可以无限次访问
回到def check_throttles(self, request):pass 中的allow_request方法进行思考,首先去获取下多长时间能够访问多少次,然后就是访问一次就计数一次,超次了就不能访问了,所以要去获取时间,在一定的时间内不能超次,如果在一定的时间内超次了就调用wait,倒计时多久才能再次访问,
allow_request其实就是先获取到多长时间访问多少次,每来一次请求把当前的时间和次数保存着,如果它两的间隔时间足够大,就重置次数为0,如果间隔时间较小就次数累加
找到drf资源文件throttling.py (有以下类)
AnonRateThrottle(SimpleRateThrottle)
BaseThrottle(object)
ScopedRateThrottle(SimpleRateThrottle)
SimpleRateThrottle(BaseThrottle)
UserRateThrottle(SimpleRateThrottle)
我们自定义的类有可能继承BaseThrottle,或SimpleRateThrottle
class BaseThrottle(object):
"""
Rate throttling of requests.
"""
#判断是否限次:没有限次可以请求True,限次就不可以请求False
def allow_request(self, request, view):
"""
Return `True` if the request should be allowed, `False` otherwise.
"""
#如果继承 BaseThrottle,必须重写allow_request
raise NotImplementedError('.allow_request() must be overridden')
def get_ident(self, request):
"""
Identify the machine making the request by parsing HTTP_X_FORWARDED_FOR
if present and number of proxies is > 0. If not use all of
HTTP_X_FORWARDED_FOR if it is available, if not use REMOTE_ADDR.
"""
xff = request.META.get('HTTP_X_FORWARDED_FOR')
remote_addr = request.META.get('REMOTE_ADDR')
num_proxies = api_settings.NUM_PROXIES
if num_proxies is not None:
if num_proxies == 0 or xff is None:
return remote_addr
addrs = xff.split(',')
client_addr = addrs[-min(num_proxies, len(addrs))]
return client_addr.strip()
return ''.join(xff.split()) if xff else remote_addr
#限次后调用,还需等待多长时间才能再访问
def wait(self):
"""
Optionally, return a recommended number of seconds to wait before
the next request.
"""
return None #返回的是等待的时间秒数
返回到 def check_throttles(self, request):
throtttle_durations=[]
for throttle in self.get_throttles():
if not throttle.allow_request(request, self):
#wait()的返回值就是要等待的多少秒,把秒数添加到数组里面
self.throttled(request, throttle.wait())
#数组就是要等待的秒时间
if throttle_durations:
#格式化,展示还需要等待多少秒
durations = [
duration for duration in throttle_durations
if duration is not None
]
duration = max(durations, default=None)
self.throttled(request, duration)
分析def get_ident(self, request):pass
查看:
num_proxies = api_settings.NUM_PROXIES
到APISettings中ctrl+F查找NUM_PROXIES
'NUM_PROXIES'=None
返回到def get_ident(self, request):pass函数方法
NUM_PROXIES如果为空走:
return ''.join(xff.split()) if xff else remote_addr
查看 SimpleRateThrottle类,继承BaseThrottle,并没有写get_ident方法
但是写了allow_request,和wait
class SimpleRateThrottle(BaseThrottle):
"""
A simple cache implementation, that only requires `.get_cache_key()`
to be overridden.
The rate (requests / seconds) is set by a `rate` attribute on the View
class. The attribute is a string of the form 'number_of_requests/period'.
Period should be one of: ('s', 'sec', 'm', 'min', 'h', 'hour', 'd', 'day')
Previous request information used for throttling is stored in the cache.
"""
cache = default_cache
timer = time.time
cache_format = 'throttle_%(scope)s_%(ident)s'
scope = None
THROTTLE_RATES = api_settings.DEFAULT_THROTTLE_RATES
def __init__(self):
if not getattr(self, 'rate', None):
self.rate = self.get_rate()
self.num_requests, self.duration = self.parse_rate(self.rate)
def get_cache_key(self, request, view):
"""
Should return a unique cache-key which can be used for throttling.
Must be overridden.
May return `None` if the request should not be throttled.
"""
raise NotImplementedError('.get_cache_key() must be overridden')
def get_rate(self):
"""
Determine the string representation of the allowed request rate.
"""
if not getattr(self, 'scope', None):
msg = ("You must set either `.scope` or `.rate` for '%s' throttle" %
self.__class__.__name__)
raise ImproperlyConfigured(msg)
try:
return self.THROTTLE_RATES[self.scope]
except KeyError:
msg = "No default throttle rate set for '%s' scope" % self.scope
raise ImproperlyConfigured(msg)
def parse_rate(self, rate):
"""
Given the request rate string, return a two tuple of:
<allowed number of requests>, <period of time in seconds>
"""
if rate is None:
return (None, None)
num, period = rate.split('/')
num_requests = int(num)
duration = {'s': 1, 'm': 60, 'h': 3600, 'd': 86400}[period[0]]
return (num_requests, duration)
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
if self.rate is None:
return True
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
self.history = self.cache.get(self.key, [])
self.now = self.timer()
# Drop any requests from the history which have now passed the
# throttle duration
while self.history and self.history[-1] <= self.now - self.duration:
self.history.pop()
if len(self.history) >= self.num_requests:
return self.throttle_failure()
return self.throttle_success()
def throttle_success(self):
"""
Inserts the current request's timestamp along with the key
into the cache.
"""
self.history.insert(0, self.now)
self.cache.set(self.key, self.history, self.duration)
return True
def throttle_failure(self):
"""
Called when a request to the API has failed due to throttling.
"""
return False
def wait(self):
"""
Returns the recommended next request time in seconds.
"""
if self.history:
remaining_duration = self.duration - (self.now - self.history[-1])
else:
remaining_duration = self.duration
available_requests = self.num_requests - len(self.history) + 1
if available_requests <= 0:
return None
return remaining_duration / float(available_requests)
分析SimpleRateThrottle中的__init__方法
因为返回到get_throttles(self): return[throttle() for throttle in self.throttle_classes]
throttle()对象加括号调用触发__init__方法
#初始化没有传入参数,所以没有'rate'参数
def __init__(self):
# 如果没有rate就调用get_rate()进行赋值
if not getattr(self, 'rate', None):
self.rate = self.get_rate()
#解析rate,用两个变量存起来
self.num_requests, self.duration = self.parse_rate(self.rate)
所有继承SimpleRateThrottle都会走__init__
返回到
def check_throttles(self, request):
throtttle_durations=[]
#throttle初始化成功之后
for throttle in self.get_throttles():
#初始化成功之后调用allow_request方法,也就是SimpleRateThrottle中的allow_request
if not throttle.allow_request(request, self):
self.throttled(request, throttle.wait())
分析SimpleRateThrottle中的allow_request方法
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
#rate没有值,就永远也不会限制访问
if self.rate is None:
return True
#如果有值往下走
#获取缓存的key赋值给self.key
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
self.history = self.cache.get(self.key, [])
self.now = self.timer()
# Drop any requests from the history which have now passed the
# throttle duration
while self.history and self.history[-1] <= self.now - self.duration:
self.history.pop()
if len(self.history) >= self.num_requests:
#频率失败
return self.throttle_failure()
#频率成功
return self.throttle_success()
#频率失败,返回false,没有请求次数
def throttle_failure(self):
"""
Called when a request to the API has failed due to throttling.
"""
return False
#频率成功
def throttle_success(self):
"""
Inserts the current request's timestamp along with the key
into the cache.
"""
# history中加时间,再成功再加,而且是加在insert列表的第一个,history长度就会越来越大,所以history的长度就是访问了几次
self.history.insert(0, self.now)
self.cache.set(self.key, self.history, self.duration)
return True
#一直成功一直成功,然后就超次了,所以就会返回False,所以就调用wait()
返回到
def check_throttles(self, request):
throtttle_durations=[]
#throttle初始化成功之后
for throttle in self.get_throttles():
#初始化成功之后调用allow_request方法,也就是SimpleRateThrottle中的allow_request
if not throttle.allow_request(request, self):
self.throttled(request, throttle.wait())
找到drf资源文件throttling.py (有以下类)
以下是系统提供的三大频率认证类,可以局部或者全局配置
ScopedRateThrottle(SimpleRateThrottle)
SimpleRateThrottle(BaseThrottle)
UserRateThrottle(SimpleRateThrottle)
分析UserRateThrottle(SimpleRateThrottle)
class UserRateThrottle(SimpleRateThrottle):
"""
Limits the rate of API calls that may be made by a given user.
The user id will be used as a unique cache key if the user is
authenticated. For anonymous requests, the IP address of the request will
be used.
"""
scope = 'user'
#返回一个字符串
def get_cache_key(self, request, view):
#有用户并且是认证用户
if request.user.is_authenticated:
#获取到用户的id
ident = request.user.pk
else:
ident = self.get_ident(request)
#'throttle_%(user)s_%(request.user.pk)s'
return self.cache_format % {
'scope': self.scope,
'ident': ident
}
点击self.cache_format
cache_format = 'throttle_%(scope)s_%(ident)s'

假设我的认证类采用了UserRateThrottle(SimpleRetaThrottle),
for throttle in self.get_throttles():pass 产生的throttle的就是UserRateThrottle产生的对象,然后UserRateThrottle中没有__init__,所以走SimpleRetaThrottle的__init__方法
<span class="hljs-function"><span class="hljs-keyword"><span class="hljs-function"><span class="hljs-keyword">def</span></span></span><span class="hljs-function"> </span><span class="hljs-title"><span class="hljs-function"><span class="hljs-title">__init__</span></span></span><span class="hljs-params"><span class="hljs-function"><span class="hljs-params">(self)</span></span></span><span class="hljs-function">:</span></span>
<span class="hljs-keyword"><span class="hljs-keyword">if</span></span> <span class="hljs-keyword"><span class="hljs-keyword">not</span></span> getattr(self, <span class="hljs-string"><span class="hljs-string">'rate'</span></span>, <span class="hljs-keyword"><span class="hljs-keyword">None</span></span>):
self.rate = self.get_rate()
self.num_requests, self.duration = self.parse_rate(self.rate)
点击self.get_rate(),
def get_rate(self):
"""
Determine the string representation of the allowed request rate.
"""
#如果没有scope直接抛异常,
#这里的self就是UserRateThrottle产生的对象,返回到UserRateThrottle获取到 scope = 'user'
if not getattr(self, 'scope', None):
msg = ("You must set either .scope or .rate for '%s' throttle" %
self.class.name)
raise ImproperlyConfigured(msg)
<span class="hljs-keyword"><span class="hljs-keyword">try</span></span>:
<span class="hljs-comment"><span class="hljs-comment">#self.THROTTLE_RATES['user'] ,这种格式就可以判断THROTTLE_RATES是一个字典,点击进入THROTTLE_RATES = api_settings.DEFAULT_THROTTLE_RATES ,,跟之前一样资源settings.py中ctrl+F查找DEFAULT_THROTTLE_RATES,</span></span>
# 'DEFAULT_THROTTLE_RATES': {
# 'user': None,
# 'anon': None,
# },
#然后在自己的settings.py中进行配置,就先走自己的配置,
#所以在这里的返回值是None
return self.THROTTLE_RATES[self.scope]
except KeyError:
# 当key没有对应的value的时候就会报错,而这里的user对应None所以是有value的
msg = "No default throttle rate set for '%s' scope" % self.scope
raise ImproperlyConfigured(msg)
返回到SimpleRetaThrottle
def __init__(self):
if not getattr(self, 'rate', None):
#self.rate=None
self.rate = self.get_rate()
self.num_requests, self.duration = self.parse_rate(self.rate)
点击 self.parse_rate(self.rate)
def parse_rate(self, rate):
"""
Given the request rate string, return a two tuple of:
<allowed number of requests>, <period of time in seconds>
"""
#如果rate是None,返回None,None
if rate is None:
return (None, None)
#如果rate不是None,就得到的是字符串并且包含有一个‘/’,因为拆分后得到得是两个结果,然后有int强转,所以num一定是一个数字
num, period = rate.split('/')
num_requests = int(num)
#period[0]取第一位,然后作为key到字典duration中查找,所以字母开头一定要是s /m / h / d,发现value都是以秒来计算,所以得到rate得格式是'3/min' 也就是'3/60'
duration = {'s': 1, 'm': 60, 'h': 3600, 'd': 86400}[period[0]]
return (num_requests, duration)
返回到SimpleRetaThrottle
def __init__(self):
if not getattr(self, 'rate', None):
#self.rate=None
self.rate = self.get_rate()
#self.num_requests, self.duration =None,None
self.num_requests, self.duration = self.parse_rate(self.rate)
为了能rate拿到值,就可以到自己得settings.py中配置
# drf配置
REST_FRAMEWORK = {
# 频率限制条件配置
'DEFAULT_THROTTLE_RATES': {
'user': '3/min',
'anon': None,
},
}
返回
def get_rate(self):
if not getattr(self, 'scope', None):
msg = ("You must set either `.scope` or `.rate` for '%s' throttle" %
self.__class__.__name__)
raise ImproperlyConfigured(msg)
try:
#return '3/min'
return self.THROTTLE_RATES[self.scope]
except KeyError:
msg = "No default throttle rate set for '%s' scope" % self.scope
raise ImproperlyConfigured(msg)
返回到SimpleRetaThrottle
def __init__(self):
if not getattr(self, 'rate', None):
self.rate = self.get_rate()
#self.num_requests:3, self.duration:60
self.num_requests, self.duration = self.parse_rate(self.rate)

返回到
def check_throttles(self, request):
throtttle_durations=[]
<span class="hljs-keyword"><span class="hljs-keyword">for</span></span> throttle <span class="hljs-keyword"><span class="hljs-keyword">in</span></span> self.get_throttles():
<span class="hljs-comment"><span class="hljs-comment"># 然后调用allow_request,到UserRateThrottle找,没有走UserRateThrottle得父类SimpleRetaThrottle</span></span>
<span class="hljs-keyword"><span class="hljs-keyword">if</span></span> <span class="hljs-keyword"><span class="hljs-keyword">not</span></span> throttle.allow_request(request, self):
self.throttled(request, throttle.wait())
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
if self.rate is None:
return True
#rate有值rate = '3/60'
# self.get_cache_key父级有这个方法,是抛异常,自己去实现这个方法
#然后子级UserRateThrottle实现了这个方法
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
self.history = self.cache.get(self.key, [])
self.now = self.timer()
# Drop any requests from the history which have now passed the
# throttle duration
while self.history and self.history[-1] <= self.now - self.duration:
self.history.pop()
if len(self.history) >= self.num_requests:
return self.throttle_failure()
return self.throttle_success()
UserRateThrottle中得get_cache_key方法
class UserRateThrottle(SimpleRateThrottle):
"""
Limits the rate of API calls that may be made by a given user.
The user id will be used as a unique cache key if the user is
authenticated. For anonymous requests, the IP address of the request will
be used.
"""
scope = 'user'
def get_cache_key(self, request, view):
if request.user.is_authenticated:
ident = request.user.pk
else:
ident = self.get_ident(request)
#'throttle_%(scope)s_%(ident)s' =》'throttle_user_1'
return self.cache_format % {
'scope': self.scope,
'ident': ident
}
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
if self.rate is None:
return True
#self.key = 'throttle_user_1'
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
#django缓存
#导包cache:from django.core.cache import cache as default_cache
#缓存有过期时间,key,value,,,default是默认值
#添加缓存:cache.set(key,defalut)
#获取缓存:cache.get(key,default) 没有获取到key采用默认值
#获取缓存key:'throttle_user_1'
#初次访问缓存为空列表,self.history=[],
self.history = self.cache.get(self.key, [])
#获取当前时间存入到self.now
self.now = self.timer()
while self.history and self.history[-1] <= self.now - self.duration:
self.history.pop()
#history的长度与限制次数3进行比较
if len(self.history) >= self.num_requests:
return self.throttle_failure()
#history的长度未达到限制次数3,代表可以访问
return self.throttle_success()
点击self.throttle_success()
#将当前时间插入到history列表的开头,将history列表作为数据存到缓存中,key是'throttle_user_1' ,过期时间60s
def throttle_success(self):
"""
Inserts the current request's timestamp along with the key
into the cache.
"""
#将当前的时间插到第一位
self.history.insert(0, self.now)
#设置缓存,key:'throttle_user_1' history:[self.now, self.now...]
# duration过期时间60s:'60'
self.cache.set(self.key, self.history, self.duration)
return True
第二次访问走到这个函数的时候
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
if self.rate is None:
return True
#self.key = 'throttle_user_1'
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
#第二次访问self.history已经有值,就是第一次访问存放的时间
self.history = self.cache.get(self.key, [])
#获取当前时间存入到self.now
self.now = self.timer()
#也就是当前的时间减去history缓存的时间(永远都取第一次访问的时间,所以是-1)是否大于过期时间
#self.now - self.history[-1] >= self.duration
#当超出的过期时间时,也就是第四次访问
while self.history and self.history[-1] <= self.now - self.duration:
#pop是将最后的时间拿出来
self.history.pop()
#history的长度与限制次数3进行比较
#history长度 第一次访问为0, 第二次访问为1,第三次访问的时间长度为2,第四次访问失败
if len(self.history) >= self.num_requests:
#直接返回False,代表频率限制了
return self.throttle_failure()
#history的长度未达到限制次数3,代表可以访问
return self.throttle_success()
def throttle_failure(self):
return False
返回到
def check_throttles(self, request):
throtttle_durations=[]
for throttle in self.get_throttles():
#只要频率限制了,allow_request 返回False,才会调用wait
if not throttle.allow_request(request, self):
self.throttled(request, throttle.wait())
调用的是SimpleRateThrottle的wait,因为UserRateThrouttle中没有wait这个方法
def wait(self):
"""
Returns the recommended next request time in seconds.
"""
#如果缓存中还有history等30s
if self.history:
#self.duration=60, self.now当前时间-self.history[-1]第一次访问时间
remaining_duration = self.duration - (self.now - self.history[-1])
else:
#如果缓存中没有,直接等60s
remaining_duration = self.duration
#self.num_requests=3,len(self.history)=3 结果3-3+1=1
available_requests = self.num_requests - len(self.history) + 1
if available_requests <= 0:
return None
# 30/1=30 返回的就是30s
#如果意外第二次访问就被限制了就是30/2=15s
return remaining_duration / float(available_requests)
自定义频率类
# 1) 自定义一个继承 SimpleRateThrottle 类 的频率类
# 2) 设置一个 scope 类属性,属性值为任意见名知意的字符串
# 3) 在settings配置文件中,配置drf的DEFAULT_THROTTLE_RATES,格式为 {scope字符串: '次数/时间'}
# 4) 在自定义频率类中重写 get_cache_key 方法
# 限制的对象返回 与限制信息有关的字符串
# 不限制的对象返回 None (只能放回None,不能是False或是''等)
短信接口 1/min 频率限制
频率:api/throttles.py
from rest_framework.throttling import SimpleRateThrottle
class SMSRateThrottle(SimpleRateThrottle):
scope = 'sms'
<span class="hljs-comment"><span class="hljs-comment"># 只对提交手机号的get方法进行限制,因为get请求发送数据就是在params中传送数据的,如果想要禁用post请发送过来的数据就要mobile = request.query_params.get('mobile') or request.data.get('mobile')</span></span>
<span class="hljs-function"><span class="hljs-keyword"><span class="hljs-function"><span class="hljs-keyword">def</span></span></span><span class="hljs-function"> </span><span class="hljs-title"><span class="hljs-function"><span class="hljs-title">get_cache_key</span></span></span><span class="hljs-params"><span class="hljs-function"><span class="hljs-params">(self, request, view)</span></span></span><span class="hljs-function">:</span></span>
mobile = request.query_params.get(<span class="hljs-string"><span class="hljs-string">'mobile'</span></span>)
<span class="hljs-comment"><span class="hljs-comment"># 没有手机号,就不做频率限制</span></span>
<span class="hljs-keyword"><span class="hljs-keyword">if</span></span> <span class="hljs-keyword"><span class="hljs-keyword">not</span></span> mobile:
<span class="hljs-keyword"><span class="hljs-keyword">return</span></span> <span class="hljs-keyword"><span class="hljs-keyword">None</span></span>
<span class="hljs-comment"><span class="hljs-comment"># 返回可以根据手机号动态变化,且不易重复的字符串,作为操作缓存的key</span></span>
<span class="hljs-keyword"><span class="hljs-keyword">return</span></span> <span class="hljs-string"><span class="hljs-string">'throttle_%(scope)s_%(ident)s'</span></span> % {<span class="hljs-string"><span class="hljs-string">'scope'</span></span>: self.scope, <span class="hljs-string"><span class="hljs-string">'ident'</span></span>: mobile}</code></pre>
配置:settings.py
# drf配置
REST_FRAMEWORK = {
# 频率限制条件配置
'DEFAULT_THROTTLE_RATES': {
'sms': '3/min' #60s内可以访问三次请求
},
}
视图:views.py
from .throttles import SMSRateThrottle
class TestSMSAPIView(APIView):
# 局部配置频率认证
throttle_classes = [SMSRateThrottle]
def get(self, request, *args, **kwargs):
return APIResponse(0, 'get 获取验证码 OK')
def post(self, request, *args, **kwargs):
return APIResponse(0, 'post 获取验证码 OK')
路由:api/url.py
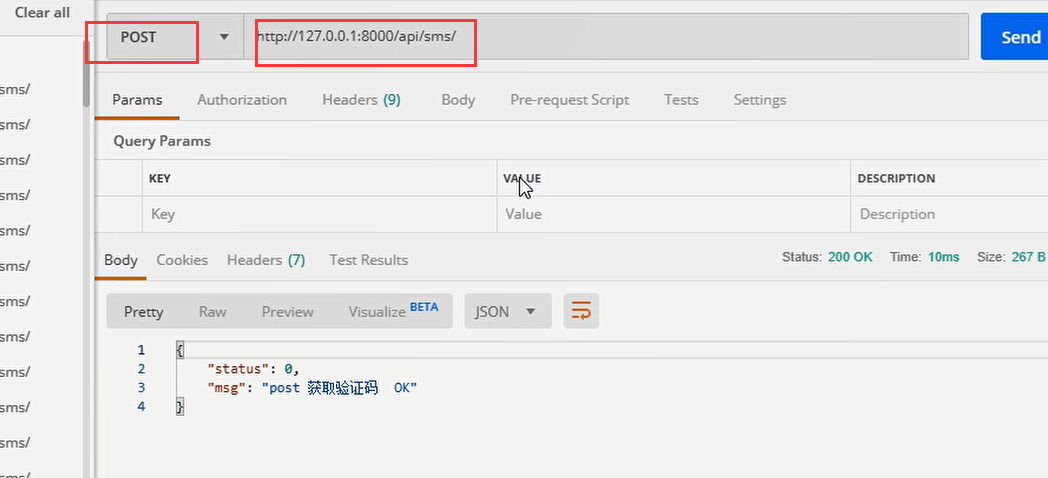
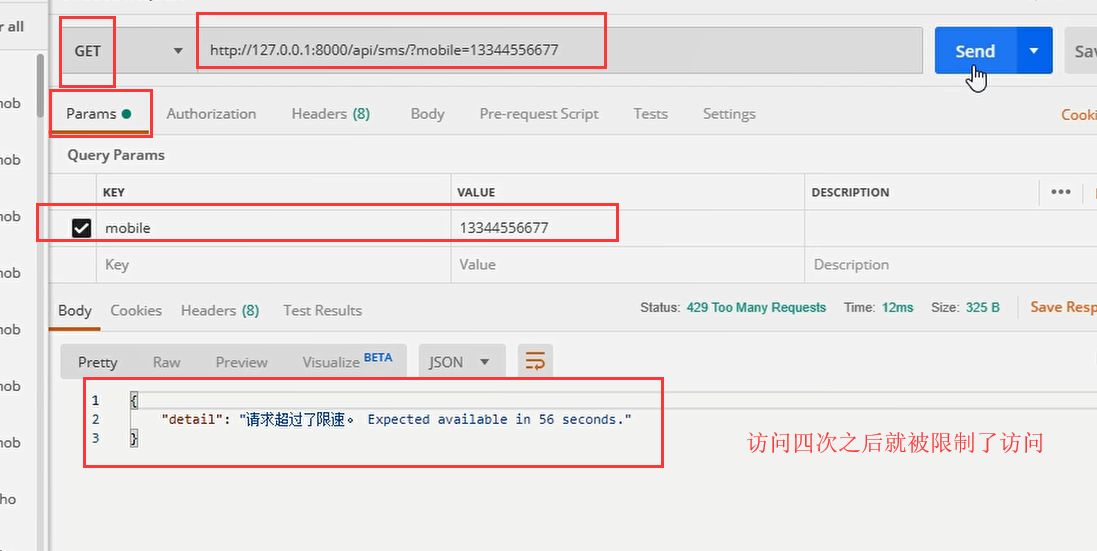
url(r'^sms/$', views.TestSMSAPIView.as_view()),
限制的接口
# 只会对 /api/sms/?mobile=具体手机号 接口才会有频率限制
# 1)对 /api/sms/ 或其他接口发送无限制
# 2)对数据包提交mobile的/api/sms/接口无限制
# 3)对不是mobile(如phone)字段提交的电话接口无限制
测试






<div class="clear"></div>
<div id="post_next_prev">
<a href="https://www.cnblogs.com/yanjiayi098-001/p/11908845.html" class="p_n_p_prefix">« </a> 上一篇: <a href="https://www.cnblogs.com/yanjiayi098-001/p/11908845.html" title="发布于 2019-11-21 22:25">drf序列化及反序列化</a>
<br>
<a href="https://www.cnblogs.com/yanjiayi098-001/p/11947023.html" class="p_n_p_prefix">» </a> 下一篇: <a href="https://www.cnblogs.com/yanjiayi098-001/p/11947023.html" title="发布于 2019-11-28 09:44">jwt认证规则</a>
目录
三大认证任务分析
- 认证模块:校验用户是是否登陆
self.perform_authentication(request)
- 权限模块:校验用户是否拥有权限
self.check_permissionsn(request)
- 频率模块:访问接口的次数在设定的时间范围内是否过快(配置访问频率、缓存计次、超次后需要等待的时间)
self.check_throttles(request)
auth组件的认证权限六表
也就是基于角色的访问控制:基于角色的访问控制(RBAC)是实施面向企业安全策略的一种有效的访问控制方式。
Django框架采用的是RBAC认证规则,RBAC认证规则通常会分为 三表规则、五表规则,Django采用的是六表规则
- 三表:用户表、角色表、权限表
- 五表:用户表、角色表、权限表、用户角色关系表、角色权限关系表
- 六表:用户表、角色表、权限表、用户角色关系表、角色权限关系表、用户权限关系表
举个栗子:看图说话

所以我们需要建立关联表(python中是六张表)

我们在实际开发中可能要重写六表
在python中的数据库中会有这六张表eg:用户表中会有用户名、密码、是否是超级管理员、是否是活跃用户等
在auth_permission中的Content_type:给Django中的所有模块中的所有表进行编号存储到Content_type中
# 应用一:权限表的权限是操作表的,所有在权限表中有一个content_type表的外键,标识该权限具体操作的是哪张表 # 应用二:价格策略 """ Course: name、type、days、price、vip_type 基础 免费课 7 0 中级 学位课 180 69 究极 会员课 360 至尊会员 以上的这张课表有大量字段重复以及空值非常麻烦,所以我们需要拆表甚至用到content_type Course: name、type、days、content_type_id 基础 免费课 7 null 中级 学位课 180 1 究极 会员课 360 2 content_type表(Django提供) id、app_label、model 1 app01 course_1 2 app01 course_2 app01_course_1 #价格策略一表(字段不一样) id、price app01_course_2 #价格策略二表(字段不一样) id vip_type """
自定义User表分析
注意:
1)auth认证6表必须在第一次数据库迁移前确定,第一次数据库迁移完成
2)完成数据库迁移,出现了auth的用户迁移异常,需要删除的数据库迁移文件有User表所在的自定义应用下的、admin组件下的、auth组件下的表删除了
源码分析

认证与权限工作原理
源码分析
APIView下的dispatch方法中的initial方法中含有三大认证:
self.perform_authentication(request) self.check_permissions(request) self.check_throttles(request)
APIView下有配置视图类的三大认证

auth组件的校验规则有三点如下图:

session认证是从cookies中去拿
认证模块工作原理
- 继承BaseAuthentication类,重写authenticate方法
- 认证规则(authenticate方法实现体):
- 没有携带认证信息,直接返回None => 游客
- 有认证信息,校验失败,抛异常 => 非法用户
- 有认证信息,校验出User对象 => 合法用户
- 没有携带认证信息,直接返回None => 游客
权限模块工作原理
- 继承BasePermission类,重写has_permission方法
- 权限规则(has_permission方法实现体):
- 返回True,代表有权限
- 返回False,代表无权限
- 返回True,代表有权限
admin关联自定义用户表
自定义认证、权限类
admin中的操作

用户群查接口权限分析
urls.py:
url(r'^users/$', views.UserListAPIView.as_view()) #群查接口
views.py:
from rest_framework.generics import ListAPIView
from . import models, serializers
# 查看所有用户信息,前提:必须是登录的超级管理员
#这里要分析Token源码
from utils.authentications import TokenAuthentication
from utils.permissions import SuperUserPermission
class UserListAPIView(ListAPIView):
# 同电商网站,多接口是不需要登录的,少接口需要登录,使用在需要登录的接口中完成局部配置,进行局部接口校验
authentication_classes = [TokenAuthentication]
permission_classes = [SuperUserPermission]
queryset = models.User.objects.filter(is_active=<span class="hljs-keyword">True</span>, is_superuser=<span class="hljs-keyword">False</span>).all()
serializer_class = serializers.UserModelSerializer
<span class="hljs-function"><span class="hljs-keyword">def</span> <span class="hljs-title">get</span><span class="hljs-params">(self, request, *args, **kwargs)</span>:</span> <span class="hljs-comment">#如果你想重写状态码</span>
response = self.list(request, *args, **kwargs)
<span class="hljs-keyword">return</span> APIResponse(data=response.data)</code></pre>
serializer.py中
from rest_framework import serializers
from rest_framework.serializers import ModelSerializer, ValidationError
from . import models
class UserModelSerializer(ModelSerializer):
class Meta:
model = models.User
fields = ('username', 'email', 'mobile') #还有一些信息你也可以提供
附:

自定义认证类
views.py中
class UserListAPIView(ListAPIView):
# 同电商网站,多接口是不需要登录的,少接口需要登录,使用在需要登录的接口中完成局部配置,进行局部接口校验
authentication_classes = [TokenAuthentication]
permission_classes = [SuperUserPermission]
pass
# 登录接口:如果是超级管理员登录,返回一个可以交易出超级管理员的token字符串
# 只要有用户登录,就可以返回一个与登录用户相关的token字符串 => 返回给前台 => 签发token => user_obj -> token_str
新建一个文件authentications.py
#自定义认证类
"""
认证模块工作原理
1)继承BaseAuthentication类,重写authenticate方法
2)认证规则(authenticate方法实现体):
没有携带认证信息,直接返回None => 游客
有认证信息,校验失败,抛异常 => 非法用户
有认证信息,校验出User对象 => 合法用户
"""
from rest_framework.authentication import BaseAuthentication
from rest_framework.exceptions import AuthenticationFailed
class TokenAuthentication(BaseAuthentication):
prefix = 'Token' #自定义一个反爬
<span class="hljs-function"><span class="hljs-keyword">def</span> <span class="hljs-title">authenticate</span><span class="hljs-params">(self, request)</span>:</span>
<span class="hljs-comment"># 拿到前台的token</span>
auth = request.META.get(<span class="hljs-string">'HTTP_AUTHORIZATION'</span>)
<span class="hljs-comment"># 没有返回None,有进行校验</span>
<span class="hljs-keyword">if</span> <span class="hljs-keyword">not</span> auth:
<span class="hljs-keyword">return</span> <span class="hljs-keyword">None</span>
auth_list = auth.split()
<span class="hljs-keyword">if</span> <span class="hljs-keyword">not</span> (len(auth_list) == <span class="hljs-number">2</span> <span class="hljs-keyword">and</span> auth_list[<span class="hljs-number">0</span>].lower() == self.prefix.lower()):
<span class="hljs-keyword">raise</span> AuthenticationFailed(<span class="hljs-string">'非法用户'</span>)
token = auth_list[<span class="hljs-number">1</span>]
<span class="hljs-comment"># 校验算法</span>
user = _get_obj(token)
<span class="hljs-comment"># 校验失败抛异常,成功返回(user, token)</span>
<span class="hljs-keyword">return</span> (user, token)
# 校验算法(认证类)与签发算法配套 """ 拆封token:一段 二段 三段 用户名A:b64decode(一段) 用户主键B:b64decode(二段) 碰撞解密:md5(用户名A+用户主键B+服务器秘钥) == 三段 服务器秘钥是一个固定的字符串在settings中 """ import base64, json, hashlib from django.conf import settings from api.models import User
def _get_obj(token): token_list = token.split('.') if len(token_list) != 3: raise AuthenticationFailed('token异常') username = json.loads(base64.b64decode(token_list[0])).get('username') pk = json.loads(base64.b64decode(token_list[1])).get('pk')
md5_dic = {
<span class="hljs-string">'username'</span>: username,
<span class="hljs-string">'pk'</span>: pk,
<span class="hljs-string">'key'</span>: settings.SECRET_KEY
}
<span class="hljs-keyword">if</span> token_list[<span class="hljs-number">2</span>] != hashlib.md5(json.dumps(md5_dic).encode()).hexdigest():
<span class="hljs-keyword">raise</span> AuthenticationFailed(<span class="hljs-string">'token内容异常'</span>)
user_obj = User.objects.get(pk=pk, username=username)
<span class="hljs-keyword">return</span> user_obj</code></pre>
认证类的认证核心规则
def authenticate(self, request):
token = get_token(request)
try:
user = get_user(token) # 校验算法
except:
raise AuthenticationFailed()
return (user, token)
自定义权限类
新建一个文件夹Permission.py
# 自定义权限类
"""
权限模块工作原理
1)继承BasePermission类,重写has_permission方法
2)权限规则(has_permission方法实现体):
返回True,代表有权限
返回False,代表无权限
"""
from rest_framework.permissions import BasePermission
class SuperUserPermission(BasePermission):
def has_permission(self, request, view):
return request.user and request.user.is_superuser
前后台分离登陆接口
views.py
# 登录接口:如果是超级管理员登录,返回一个可以交易出超级管理员的token字符串
# 只要有用户登录,就可以返回一个与登录用户相关的token字符串 => 返回给前台 => 签发token => user_obj -> token_str
from rest_framework.generics import GenericAPIView
class LoginAPIView(APIView):
# 登录接口一定要做:局部禁用 认证 与 权限 校验
authentication_classes = []
permission_classes = []
def post(self, request, *args, **kwargs):
serializer = serializers.LoginModelSerializer(data=request.data)
# 重点:校验成功后,就可以返回信息,一定不能调用save方法,因为该post方法只完成数据库查操作
# 所以校验会得到user对象,并且在校验过程中,会完成token签发(user_obj -> token_str)
serializer.is_valid(raise_exception=True)
return APIResponse(data={
'username': serializer.user.username,
'token': serializer.token
})
serializers.py
from django.contrib.auth import authenticate
class LoginModelSerializer(ModelSerializer):
# username和password字段默认会走系统校验,而系统的post请求校验,一定当做增方式校验,所以用户名会出现 重复 的异常
# 所以自定义两个字段接收前台的账号密码
usr = serializers.CharField(write_only=True)
pwd = serializers.CharField(write_only=True)
class Meta: #非标准接口下面的反序列化
model = models.User
fields = ('usr', 'pwd')
def validate(self, attrs): #全局钩子
usr = attrs.get('usr')
pwd = attrs.get('pwd')
try:
user_obj = authenticate(username=usr, password=pwd)
except:
raise ValidationError({'user': '提供的用户信息有误'})
# 拓展名称空间
self.user = user_obj
# 签发token
self.token = _get_token(user_obj)
return attrs
# 自定义签发token
# 分析:拿user得到token,后期还需要通过token得到user
# token:用户名(base64加密).用户主键(base64加密).用户名+用户主键+服务器秘钥(md5加密)
# eg: YWJj.Ao12bd.2c953ca5144a6c0a187a264ef08e1af1
频率认证源码分析
APIView ---》dispatch方法---》self.initial(request, *args, **kwargs)---》 self.check_throttles(request)
#重新访问这个接口的时候,都会重新调用这个方法,每次访问都会throtttle_durations=[]置空
def check_throttles(self, request):
"""
Check if request should be throttled.
Raises an appropriate exception if the request is throttled.
"""
#比如一分钟只能访问三次,第一,二,三次访问的时候都没有限制,第四次访问就会制
#限次的持续时间,还有多少秒才能接着访问这个接口
throtttle_durations=[]
# self.get_throttles()全局或局部配置的类
for throttle in self.get_throttles():
#allow_request允许请求返回True,不允许就返回False,为false时成立,
if not throttle.allow_request(request, self):
#throttle.wait()等待的限次持续时间
self.throttled(request, throttle.wait())
# 第四次限制,有限制持续时间才会走这部
if throttle_durations:
durations = [
duration for duration in throttle_durations
if duration is not None
]
duration = max(durations, default=None)
self.throttled(request, duration)
这说明我们自定义类要重写allow_request(request, self)和wait(),因为throttle调用了
点击 self.get_throttles()查看
def get_throttles(self):
"""
Instantiates and returns the list of throttles that this view uses.
"""
return [throttle() for throttle in self.throttle_classes]
点击 self.throttle_classes
throttle_classes = api_settings.DEFAULT_THROTTLE_CLASSES
throttle_classes跟之前一样可局部配置throttle_classes=[] ,可全局配置settings文件中配置
到drf资源文件settings.py文件中的APISettings类中查看默认配置:ctrl+f键查找DEFAULT_THROTTLE_CLASSES
'DEFAULT_THROTTLE_CLASSES': [],#所以说任何接口都可以无限次访问
回到def check_throttles(self, request):pass 中的allow_request方法进行思考,首先去获取下多长时间能够访问多少次,然后就是访问一次就计数一次,超次了就不能访问了,所以要去获取时间,在一定的时间内不能超次,如果在一定的时间内超次了就调用wait,倒计时多久才能再次访问,
allow_request其实就是先获取到多长时间访问多少次,每来一次请求把当前的时间和次数保存着,如果它两的间隔时间足够大,就重置次数为0,如果间隔时间较小就次数累加
找到drf资源文件throttling.py (有以下类) AnonRateThrottle(SimpleRateThrottle) BaseThrottle(object) ScopedRateThrottle(SimpleRateThrottle) SimpleRateThrottle(BaseThrottle) UserRateThrottle(SimpleRateThrottle) 我们自定义的类有可能继承BaseThrottle,或SimpleRateThrottle
class BaseThrottle(object):
"""
Rate throttling of requests.
"""
#判断是否限次:没有限次可以请求True,限次就不可以请求False
def allow_request(self, request, view):
"""
Return `True` if the request should be allowed, `False` otherwise.
"""
#如果继承 BaseThrottle,必须重写allow_request
raise NotImplementedError('.allow_request() must be overridden')
def get_ident(self, request):
"""
Identify the machine making the request by parsing HTTP_X_FORWARDED_FOR
if present and number of proxies is > 0. If not use all of
HTTP_X_FORWARDED_FOR if it is available, if not use REMOTE_ADDR.
"""
xff = request.META.get('HTTP_X_FORWARDED_FOR')
remote_addr = request.META.get('REMOTE_ADDR')
num_proxies = api_settings.NUM_PROXIES
if num_proxies is not None:
if num_proxies == 0 or xff is None:
return remote_addr
addrs = xff.split(',')
client_addr = addrs[-min(num_proxies, len(addrs))]
return client_addr.strip()
return ''.join(xff.split()) if xff else remote_addr
#限次后调用,还需等待多长时间才能再访问
def wait(self):
"""
Optionally, return a recommended number of seconds to wait before
the next request.
"""
return None #返回的是等待的时间秒数
返回到 def check_throttles(self, request):
throtttle_durations=[]
for throttle in self.get_throttles():
if not throttle.allow_request(request, self):
#wait()的返回值就是要等待的多少秒,把秒数添加到数组里面
self.throttled(request, throttle.wait())
#数组就是要等待的秒时间
if throttle_durations:
#格式化,展示还需要等待多少秒
durations = [
duration for duration in throttle_durations
if duration is not None
]
duration = max(durations, default=None)
self.throttled(request, duration)
分析def get_ident(self, request):pass 查看: num_proxies = api_settings.NUM_PROXIES 到APISettings中ctrl+F查找NUM_PROXIES 'NUM_PROXIES'=None 返回到def get_ident(self, request):pass函数方法 NUM_PROXIES如果为空走: return ''.join(xff.split()) if xff else remote_addr
查看 SimpleRateThrottle类,继承BaseThrottle,并没有写get_ident方法
但是写了allow_request,和wait
class SimpleRateThrottle(BaseThrottle):
"""
A simple cache implementation, that only requires `.get_cache_key()`
to be overridden.
The rate (requests / seconds) is set by a `rate` attribute on the View
class. The attribute is a string of the form 'number_of_requests/period'.
Period should be one of: ('s', 'sec', 'm', 'min', 'h', 'hour', 'd', 'day')
Previous request information used for throttling is stored in the cache.
"""
cache = default_cache
timer = time.time
cache_format = 'throttle_%(scope)s_%(ident)s'
scope = None
THROTTLE_RATES = api_settings.DEFAULT_THROTTLE_RATES
def __init__(self):
if not getattr(self, 'rate', None):
self.rate = self.get_rate()
self.num_requests, self.duration = self.parse_rate(self.rate)
def get_cache_key(self, request, view):
"""
Should return a unique cache-key which can be used for throttling.
Must be overridden.
May return `None` if the request should not be throttled.
"""
raise NotImplementedError('.get_cache_key() must be overridden')
def get_rate(self):
"""
Determine the string representation of the allowed request rate.
"""
if not getattr(self, 'scope', None):
msg = ("You must set either `.scope` or `.rate` for '%s' throttle" %
self.__class__.__name__)
raise ImproperlyConfigured(msg)
try:
return self.THROTTLE_RATES[self.scope]
except KeyError:
msg = "No default throttle rate set for '%s' scope" % self.scope
raise ImproperlyConfigured(msg)
def parse_rate(self, rate):
"""
Given the request rate string, return a two tuple of:
<allowed number of requests>, <period of time in seconds>
"""
if rate is None:
return (None, None)
num, period = rate.split('/')
num_requests = int(num)
duration = {'s': 1, 'm': 60, 'h': 3600, 'd': 86400}[period[0]]
return (num_requests, duration)
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
if self.rate is None:
return True
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
self.history = self.cache.get(self.key, [])
self.now = self.timer()
# Drop any requests from the history which have now passed the
# throttle duration
while self.history and self.history[-1] <= self.now - self.duration:
self.history.pop()
if len(self.history) >= self.num_requests:
return self.throttle_failure()
return self.throttle_success()
def throttle_success(self):
"""
Inserts the current request's timestamp along with the key
into the cache.
"""
self.history.insert(0, self.now)
self.cache.set(self.key, self.history, self.duration)
return True
def throttle_failure(self):
"""
Called when a request to the API has failed due to throttling.
"""
return False
def wait(self):
"""
Returns the recommended next request time in seconds.
"""
if self.history:
remaining_duration = self.duration - (self.now - self.history[-1])
else:
remaining_duration = self.duration
available_requests = self.num_requests - len(self.history) + 1
if available_requests <= 0:
return None
return remaining_duration / float(available_requests)
分析SimpleRateThrottle中的__init__方法
因为返回到get_throttles(self): return[throttle() for throttle in self.throttle_classes]
throttle()对象加括号调用触发__init__方法
#初始化没有传入参数,所以没有'rate'参数
def __init__(self):
# 如果没有rate就调用get_rate()进行赋值
if not getattr(self, 'rate', None):
self.rate = self.get_rate()
#解析rate,用两个变量存起来
self.num_requests, self.duration = self.parse_rate(self.rate)
所有继承SimpleRateThrottle都会走__init__
返回到
def check_throttles(self, request):
throtttle_durations=[]
#throttle初始化成功之后
for throttle in self.get_throttles():
#初始化成功之后调用allow_request方法,也就是SimpleRateThrottle中的allow_request
if not throttle.allow_request(request, self):
self.throttled(request, throttle.wait())
分析SimpleRateThrottle中的allow_request方法
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
#rate没有值,就永远也不会限制访问
if self.rate is None:
return True
#如果有值往下走
#获取缓存的key赋值给self.key
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
self.history = self.cache.get(self.key, [])
self.now = self.timer()
# Drop any requests from the history which have now passed the
# throttle duration
while self.history and self.history[-1] <= self.now - self.duration:
self.history.pop()
if len(self.history) >= self.num_requests:
#频率失败
return self.throttle_failure()
#频率成功
return self.throttle_success()
#频率失败,返回false,没有请求次数
def throttle_failure(self):
"""
Called when a request to the API has failed due to throttling.
"""
return False
#频率成功
def throttle_success(self):
"""
Inserts the current request's timestamp along with the key
into the cache.
"""
# history中加时间,再成功再加,而且是加在insert列表的第一个,history长度就会越来越大,所以history的长度就是访问了几次
self.history.insert(0, self.now)
self.cache.set(self.key, self.history, self.duration)
return True
#一直成功一直成功,然后就超次了,所以就会返回False,所以就调用wait()
返回到
def check_throttles(self, request):
throtttle_durations=[]
#throttle初始化成功之后
for throttle in self.get_throttles():
#初始化成功之后调用allow_request方法,也就是SimpleRateThrottle中的allow_request
if not throttle.allow_request(request, self):
self.throttled(request, throttle.wait())
找到drf资源文件throttling.py (有以下类) 以下是系统提供的三大频率认证类,可以局部或者全局配置 ScopedRateThrottle(SimpleRateThrottle) SimpleRateThrottle(BaseThrottle) UserRateThrottle(SimpleRateThrottle)
分析UserRateThrottle(SimpleRateThrottle)
class UserRateThrottle(SimpleRateThrottle):
"""
Limits the rate of API calls that may be made by a given user.
The user id will be used as a unique cache key if the user is
authenticated. For anonymous requests, the IP address of the request will
be used.
"""
scope = 'user'
#返回一个字符串
def get_cache_key(self, request, view):
#有用户并且是认证用户
if request.user.is_authenticated:
#获取到用户的id
ident = request.user.pk
else:
ident = self.get_ident(request)
#'throttle_%(user)s_%(request.user.pk)s'
return self.cache_format % {
'scope': self.scope,
'ident': ident
}
点击self.cache_format
cache_format = 'throttle_%(scope)s_%(ident)s'
假设我的认证类采用了UserRateThrottle(SimpleRetaThrottle),
for throttle in self.get_throttles():pass 产生的throttle的就是UserRateThrottle产生的对象,然后UserRateThrottle中没有__init__,所以走SimpleRetaThrottle的__init__方法
<span class="hljs-function"><span class="hljs-keyword"><span class="hljs-function"><span class="hljs-keyword">def</span></span></span><span class="hljs-function"> </span><span class="hljs-title"><span class="hljs-function"><span class="hljs-title">__init__</span></span></span><span class="hljs-params"><span class="hljs-function"><span class="hljs-params">(self)</span></span></span><span class="hljs-function">:</span></span>
<span class="hljs-keyword"><span class="hljs-keyword">if</span></span> <span class="hljs-keyword"><span class="hljs-keyword">not</span></span> getattr(self, <span class="hljs-string"><span class="hljs-string">'rate'</span></span>, <span class="hljs-keyword"><span class="hljs-keyword">None</span></span>):
self.rate = self.get_rate()
self.num_requests, self.duration = self.parse_rate(self.rate)
点击self.get_rate(),
def get_rate(self):
"""
Determine the string representation of the allowed request rate.
"""
#如果没有scope直接抛异常,
#这里的self就是UserRateThrottle产生的对象,返回到UserRateThrottle获取到 scope = 'user'
if not getattr(self, 'scope', None):
msg = ("You must set either .scope or .rate for '%s' throttle" %
self.class.name)
raise ImproperlyConfigured(msg)
<span class="hljs-keyword"><span class="hljs-keyword">try</span></span>:
<span class="hljs-comment"><span class="hljs-comment">#self.THROTTLE_RATES['user'] ,这种格式就可以判断THROTTLE_RATES是一个字典,点击进入THROTTLE_RATES = api_settings.DEFAULT_THROTTLE_RATES ,,跟之前一样资源settings.py中ctrl+F查找DEFAULT_THROTTLE_RATES,</span></span>
# 'DEFAULT_THROTTLE_RATES': { # 'user': None, # 'anon': None, # }, #然后在自己的settings.py中进行配置,就先走自己的配置, #所以在这里的返回值是None return self.THROTTLE_RATES[self.scope] except KeyError: # 当key没有对应的value的时候就会报错,而这里的user对应None所以是有value的 msg = "No default throttle rate set for '%s' scope" % self.scope raise ImproperlyConfigured(msg)
返回到SimpleRetaThrottle
def __init__(self):
if not getattr(self, 'rate', None):
#self.rate=None
self.rate = self.get_rate()
self.num_requests, self.duration = self.parse_rate(self.rate)
点击 self.parse_rate(self.rate)
def parse_rate(self, rate):
"""
Given the request rate string, return a two tuple of:
<allowed number of requests>, <period of time in seconds>
"""
#如果rate是None,返回None,None
if rate is None:
return (None, None)
#如果rate不是None,就得到的是字符串并且包含有一个‘/’,因为拆分后得到得是两个结果,然后有int强转,所以num一定是一个数字
num, period = rate.split('/')
num_requests = int(num)
#period[0]取第一位,然后作为key到字典duration中查找,所以字母开头一定要是s /m / h / d,发现value都是以秒来计算,所以得到rate得格式是'3/min' 也就是'3/60'
duration = {'s': 1, 'm': 60, 'h': 3600, 'd': 86400}[period[0]]
return (num_requests, duration)
返回到SimpleRetaThrottle
def __init__(self):
if not getattr(self, 'rate', None):
#self.rate=None
self.rate = self.get_rate()
#self.num_requests, self.duration =None,None
self.num_requests, self.duration = self.parse_rate(self.rate)
为了能rate拿到值,就可以到自己得settings.py中配置
# drf配置
REST_FRAMEWORK = {
# 频率限制条件配置
'DEFAULT_THROTTLE_RATES': {
'user': '3/min',
'anon': None,
},
}
返回
def get_rate(self):
if not getattr(self, 'scope', None):
msg = ("You must set either `.scope` or `.rate` for '%s' throttle" %
self.__class__.__name__)
raise ImproperlyConfigured(msg)
try:
#return '3/min'
return self.THROTTLE_RATES[self.scope]
except KeyError:
msg = "No default throttle rate set for '%s' scope" % self.scope
raise ImproperlyConfigured(msg)
返回到SimpleRetaThrottle
def __init__(self):
if not getattr(self, 'rate', None):
self.rate = self.get_rate()
#self.num_requests:3, self.duration:60
self.num_requests, self.duration = self.parse_rate(self.rate)
返回到
def check_throttles(self, request):
throtttle_durations=[]
<span class="hljs-keyword"><span class="hljs-keyword">for</span></span> throttle <span class="hljs-keyword"><span class="hljs-keyword">in</span></span> self.get_throttles():
<span class="hljs-comment"><span class="hljs-comment"># 然后调用allow_request,到UserRateThrottle找,没有走UserRateThrottle得父类SimpleRetaThrottle</span></span>
<span class="hljs-keyword"><span class="hljs-keyword">if</span></span> <span class="hljs-keyword"><span class="hljs-keyword">not</span></span> throttle.allow_request(request, self):
self.throttled(request, throttle.wait())
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
if self.rate is None:
return True
#rate有值rate = '3/60'
# self.get_cache_key父级有这个方法,是抛异常,自己去实现这个方法
#然后子级UserRateThrottle实现了这个方法
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
self.history = self.cache.get(self.key, [])
self.now = self.timer()
# Drop any requests from the history which have now passed the
# throttle duration
while self.history and self.history[-1] <= self.now - self.duration:
self.history.pop()
if len(self.history) >= self.num_requests:
return self.throttle_failure()
return self.throttle_success()
UserRateThrottle中得get_cache_key方法
class UserRateThrottle(SimpleRateThrottle):
"""
Limits the rate of API calls that may be made by a given user.
The user id will be used as a unique cache key if the user is
authenticated. For anonymous requests, the IP address of the request will
be used.
"""
scope = 'user'
def get_cache_key(self, request, view):
if request.user.is_authenticated:
ident = request.user.pk
else:
ident = self.get_ident(request)
#'throttle_%(scope)s_%(ident)s' =》'throttle_user_1'
return self.cache_format % {
'scope': self.scope,
'ident': ident
}
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
if self.rate is None:
return True
#self.key = 'throttle_user_1'
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
#django缓存
#导包cache:from django.core.cache import cache as default_cache
#缓存有过期时间,key,value,,,default是默认值
#添加缓存:cache.set(key,defalut)
#获取缓存:cache.get(key,default) 没有获取到key采用默认值
#获取缓存key:'throttle_user_1'
#初次访问缓存为空列表,self.history=[],
self.history = self.cache.get(self.key, [])
#获取当前时间存入到self.now
self.now = self.timer()
while self.history and self.history[-1] <= self.now - self.duration:
self.history.pop()
#history的长度与限制次数3进行比较
if len(self.history) >= self.num_requests:
return self.throttle_failure()
#history的长度未达到限制次数3,代表可以访问
return self.throttle_success()
点击self.throttle_success()
#将当前时间插入到history列表的开头,将history列表作为数据存到缓存中,key是'throttle_user_1' ,过期时间60s
def throttle_success(self):
"""
Inserts the current request's timestamp along with the key
into the cache.
"""
#将当前的时间插到第一位
self.history.insert(0, self.now)
#设置缓存,key:'throttle_user_1' history:[self.now, self.now...]
# duration过期时间60s:'60'
self.cache.set(self.key, self.history, self.duration)
return True
第二次访问走到这个函数的时候
def allow_request(self, request, view):
"""
Implement the check to see if the request should be throttled.
On success calls `throttle_success`.
On failure calls `throttle_failure`.
"""
if self.rate is None:
return True
#self.key = 'throttle_user_1'
self.key = self.get_cache_key(request, view)
if self.key is None:
return True
#第二次访问self.history已经有值,就是第一次访问存放的时间
self.history = self.cache.get(self.key, [])
#获取当前时间存入到self.now
self.now = self.timer()
#也就是当前的时间减去history缓存的时间(永远都取第一次访问的时间,所以是-1)是否大于过期时间
#self.now - self.history[-1] >= self.duration
#当超出的过期时间时,也就是第四次访问
while self.history and self.history[-1] <= self.now - self.duration:
#pop是将最后的时间拿出来
self.history.pop()
#history的长度与限制次数3进行比较
#history长度 第一次访问为0, 第二次访问为1,第三次访问的时间长度为2,第四次访问失败
if len(self.history) >= self.num_requests:
#直接返回False,代表频率限制了
return self.throttle_failure()
#history的长度未达到限制次数3,代表可以访问
return self.throttle_success()
def throttle_failure(self):
return False
返回到
def check_throttles(self, request):
throtttle_durations=[]
for throttle in self.get_throttles():
#只要频率限制了,allow_request 返回False,才会调用wait
if not throttle.allow_request(request, self):
self.throttled(request, throttle.wait())
调用的是SimpleRateThrottle的wait,因为UserRateThrouttle中没有wait这个方法
def wait(self):
"""
Returns the recommended next request time in seconds.
"""
#如果缓存中还有history等30s
if self.history:
#self.duration=60, self.now当前时间-self.history[-1]第一次访问时间
remaining_duration = self.duration - (self.now - self.history[-1])
else:
#如果缓存中没有,直接等60s
remaining_duration = self.duration
#self.num_requests=3,len(self.history)=3 结果3-3+1=1
available_requests = self.num_requests - len(self.history) + 1
if available_requests <= 0:
return None
# 30/1=30 返回的就是30s
#如果意外第二次访问就被限制了就是30/2=15s
return remaining_duration / float(available_requests)
自定义频率类
# 1) 自定义一个继承 SimpleRateThrottle 类 的频率类
# 2) 设置一个 scope 类属性,属性值为任意见名知意的字符串
# 3) 在settings配置文件中,配置drf的DEFAULT_THROTTLE_RATES,格式为 {scope字符串: '次数/时间'}
# 4) 在自定义频率类中重写 get_cache_key 方法
# 限制的对象返回 与限制信息有关的字符串
# 不限制的对象返回 None (只能放回None,不能是False或是''等)
短信接口 1/min 频率限制
频率:api/throttles.py
from rest_framework.throttling import SimpleRateThrottle
class SMSRateThrottle(SimpleRateThrottle):
scope = 'sms'
<span class="hljs-comment"><span class="hljs-comment"># 只对提交手机号的get方法进行限制,因为get请求发送数据就是在params中传送数据的,如果想要禁用post请发送过来的数据就要mobile = request.query_params.get('mobile') or request.data.get('mobile')</span></span>
<span class="hljs-function"><span class="hljs-keyword"><span class="hljs-function"><span class="hljs-keyword">def</span></span></span><span class="hljs-function"> </span><span class="hljs-title"><span class="hljs-function"><span class="hljs-title">get_cache_key</span></span></span><span class="hljs-params"><span class="hljs-function"><span class="hljs-params">(self, request, view)</span></span></span><span class="hljs-function">:</span></span>
mobile = request.query_params.get(<span class="hljs-string"><span class="hljs-string">'mobile'</span></span>)
<span class="hljs-comment"><span class="hljs-comment"># 没有手机号,就不做频率限制</span></span>
<span class="hljs-keyword"><span class="hljs-keyword">if</span></span> <span class="hljs-keyword"><span class="hljs-keyword">not</span></span> mobile:
<span class="hljs-keyword"><span class="hljs-keyword">return</span></span> <span class="hljs-keyword"><span class="hljs-keyword">None</span></span>
<span class="hljs-comment"><span class="hljs-comment"># 返回可以根据手机号动态变化,且不易重复的字符串,作为操作缓存的key</span></span>
<span class="hljs-keyword"><span class="hljs-keyword">return</span></span> <span class="hljs-string"><span class="hljs-string">'throttle_%(scope)s_%(ident)s'</span></span> % {<span class="hljs-string"><span class="hljs-string">'scope'</span></span>: self.scope, <span class="hljs-string"><span class="hljs-string">'ident'</span></span>: mobile}</code></pre>
配置:settings.py
# drf配置
REST_FRAMEWORK = {
# 频率限制条件配置
'DEFAULT_THROTTLE_RATES': {
'sms': '3/min' #60s内可以访问三次请求
},
}
视图:views.py
from .throttles import SMSRateThrottle
class TestSMSAPIView(APIView):
# 局部配置频率认证
throttle_classes = [SMSRateThrottle]
def get(self, request, *args, **kwargs):
return APIResponse(0, 'get 获取验证码 OK')
def post(self, request, *args, **kwargs):
return APIResponse(0, 'post 获取验证码 OK')
路由:api/url.py
url(r'^sms/$', views.TestSMSAPIView.as_view()),
限制的接口
# 只会对 /api/sms/?mobile=具体手机号 接口才会有频率限制 # 1)对 /api/sms/ 或其他接口发送无限制 # 2)对数据包提交mobile的/api/sms/接口无限制 # 3)对不是mobile(如phone)字段提交的电话接口无限制
测试