10.6 监控io性能
iostat命令
>iostat命令被用于监视系统输入输出设备和CPU的使用情况。它的特点是汇报磁盘活动统计情况,同时也会汇报出CPU使用情况。同vmstat一样,iostat也有一个弱点,就是它不能对某个进程进行深入分析,仅对系统的整体情况进行分析。
iostat -x
[root@cham2 ~]# iostat -x 1
Linux 3.10.0-514.el7.x86_64 (cham2) 2017年11月28日 _x86_64_ (2 CPU)
avg-cpu: %user %nice %system %iowait %steal %idle
0.01 0.00 0.03 0.01 0.00 99.95
Device: rrqm/s wrqm/s r/s w/s rkB/s wkB/s avgrq-sz avgqu-sz await r_await w_await svctm %util
sdb 0.00 0.00 0.00 0.00 0.02 0.00 12.56 0.00 2.96 2.96 0.00 2.43 0.00
sda 0.00 0.01 0.07 0.08 2.28 1.22 46.19 0.00 11.82 11.10 12.51 3.11 0.05
dm-0 0.00 0.00 0.00 0.00 0.01 0.00 15.20 0.00 5.90 5.90 0.00 5.72 0.00
avg-cpu: %user %nice %system %iowait %steal %idle
0.00 0.00 0.00 0.00 0.00 100.00
Device: rrqm/s wrqm/s r/s w/s rkB/s wkB/s avgrq-sz avgqu-sz await r_await w_await svctm %util
sdb 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
sda 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
dm-0 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
avg-cpu: %user %nice %system %iowait %steal %idle
0.00 0.00 0.50 0.00 0.00 99.50
Device: rrqm/s wrqm/s r/s w/s rkB/s wkB/s avgrq-sz avgqu-sz await r_await w_await svctm %util
sdb 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
sda 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
dm-0 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
avg-cpu: %user %nice %system %iowait %steal %idle
0.00 0.00 0.00 0.00 0.00 100.00
Device: rrqm/s wrqm/s r/s w/s rkB/s wkB/s avgrq-sz avgqu-sz await r_await w_await svctm %util
sdb 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
sda 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
dm-0 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
avg-cpu: %user %nice %system %iowait %steal %idle
0.00 0.00 0.00 0.00 0.00 100.00
Device: rrqm/s wrqm/s r/s w/s rkB/s wkB/s avgrq-sz avgqu-sz await r_await w_await svctm %util
sdb 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
sda 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
dm-0 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00
说明: util%:表示io等待占比,正常情况下该值和磁盘读写(r/w)成正比,如果该值很大,读写数值很小则说明磁盘存在问题,系统性能会受影响!
iotop命令
>iotop命令是一个用来监视磁盘I/O使用状况的top类工具(动态)。iotop具有与top相似的UI,其中包括PID、用户、I/O、进程等相关信息。Linux下的IO统计工具如iostat,nmon等大多数是只能统计到per设备的读写情况,如果你想知道每个进程是如何使用IO的就比较麻烦,使用iotop命令可以很方便的查看。
如果没有安装要安装
[root@cham2 ~]# yum install -y iotop
已加载插件:fastestmirror
iotop
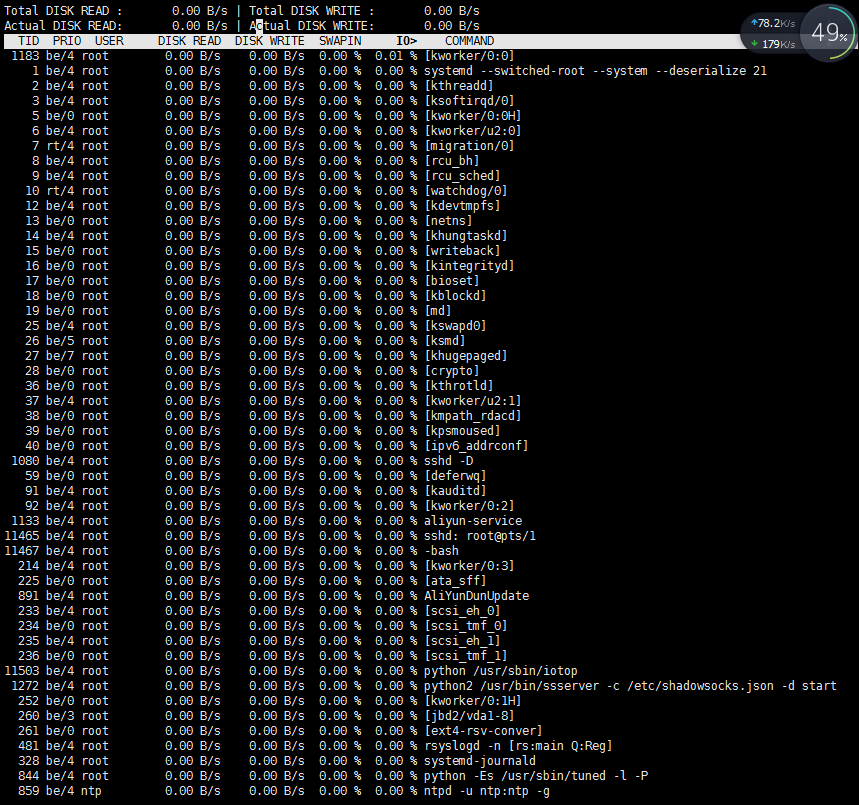
注: 在此关注‘IO>’这一列!
-
iotop常用快捷键
- 左右箭头:改变排序方式,默认是按IO排序
- r:改变排序顺序。
- o:只显示有IO输出的进程。
- p:进程/线程的显示方式的切换。
- a:显示累积使用量。
- q:退出。
10.7 free命令
>free命令可以显示当前系统未使用的和已使用的内存数目,还可以显示被内核使用的内存缓冲区。
语法: free [options]
Options:
-b/k/m/g:分别以byte、KB、M、G为单位显示(默认以KB为单位)
-h:已适当的单位显示
-t:显示内存总和'
[root@cham2 ~]# free
total used free shared buff/cache available
Mem: 1008416 119780 588156 6888 300480 716668
Swap: 3905532 0 3905532
[root@cham2 ~]# free -m
total used free shared buff/cache available
Mem: 984 116 574 6 293 700
Swap: 3813 0 3813
[root@cham2 ~]# free -h
total used free shared buff/cache available
Mem: 984M 116M 574M 6.7M 293M 699M
Swap: 3.7G 0B 3.7G
说明:
“total=used+free+buff/cache”
“available=free+buff/cache(空闲部分)”
available包含free和buff/cached的剩余部分
buff(缓冲):当CPU向磁盘写入数据时,由于磁盘存储速率低于CPU,所以CPU工作时先将写好的数据存放在内存中,该部分内存即为缓冲内存。
cache(缓存):当CPU从磁盘读取数据时,由于磁盘输出速率低于CPU的读取速度,所以磁盘的数据会预先存放在内存中,该部分内存即为缓存内存。![]()
10.8 ps命令
>ps命令用于报告当前系统的进程状态。可以搭配kill(PID)指令随时中断、删除不必要的程序。ps命令是最基本同时也是非常强大的进程查看命令,使用该命令可以确定有哪些进程正在运行和运行的状态、进程是否结束、进程有没有僵死、哪些进程占用了过多的资源等等,总之大部分信息都是可以通过执行该命令得到的。
用法
语法: ps [options]
Options:
a:显示现行终端机下的所有程序,包括其他用户的程序。
u:以用户为主的格式来显示系统状况。
x:显示所有程序,包括历史进程。
-e:显示所有进程(同a)
-f:显示UID、PPIP、C与STIME栏
-l:显示进程详细信息
ps aux
[root@chamhk ~]# ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.3 43284 3660 ? Ss Nov27 0:00 /usr/lib/systemd/systemd --switched-root --system --deser
root 2 0.0 0.0 0 0 ? S Nov27 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S Nov27 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< Nov27 0:00 [kworker/0:0H]
root 6 0.0 0.0 0 0 ? S Nov27 0:00 [kworker/u2:0]
root 7 0.0 0.0 0 0 ? S Nov27 0:00 [migration/0]
root 8 0.0 0.0 0 0 ? S Nov27 0:00 [rcu_bh]
root 9 0.0 0.0 0 0 ? R Nov27 0:01 [rcu_sched]
root 10 0.0 0.0 0 0 ? S Nov27 0:00 [watchdog/0]
root 12 0.0 0.0 0 0 ? S Nov27 0:00 [kdevtmpfs]
root 13 0.0 0.0 0 0 ? S< Nov27 0:00 [netns]
root 14 0.0 0.0 0 0 ? S Nov27 0:00 [khungtaskd]
root 15 0.0 0.0 0 0 ? S< Nov27 0:00 [writeback]
root 16 0.0 0.0 0 0 ? S< Nov27 0:00 [kintegrityd]
root 17 0.0 0.0 0 0 ? S< Nov27 0:00 [bioset]
root 18 0.0 0.0 0 0 ? S< Nov27 0:00 [kblockd]
root 19 0.0 0.0 0 0 ? S< Nov27 0:00 [md]
root 25 0.0 0.0 0 0 ? S Nov27 0:00 [kswapd0]
root 26 0.0 0.0 0 0 ? SN Nov27 0:00 [ksmd]
root 27 0.0 0.0 0 0 ? SN Nov27 0:00 [khugepaged]
root 28 0.0 0.0 0 0 ? S< Nov27 0:00 [crypto]
root 36 0.0 0.0 0 0 ? S< Nov27 0:00 [kthrotld]
root 37 0.0 0.0 0 0 ? S Nov27 0:00 [kworker/u2:1]
root 38 0.0 0.0 0 0 ? S< Nov27 0:00 [kmpath_rdacd]
root 39 0.0 0.0 0 0 ? S< Nov27 0:00 [kpsmoused]
root 40 0.0 0.0 0 0 ? S< Nov27 0:00 [ipv6_addrconf]
root 59 0.0 0.0 0 0 ? S< Nov27 0:00 [deferwq]
root 91 0.0 0.0 0 0 ? S Nov27 0:00 [kauditd]
root 92 0.0 0.0 0 0 ? S Nov27 0:00 [kworker/0:2]
root 214 0.0 0.0 0 0 ? S Nov27 0:03 [kworker/0:3]
root 225 0.0 0.0 0 0 ? S< Nov27 0:00 [ata_sff]
root 233 0.0 0.0 0 0 ? S Nov27 0:00 [scsi_eh_0]
root 234 0.0 0.0 0 0 ? S< Nov27 0:00 [scsi_tmf_0]
root 235 0.0 0.0 0 0 ? S Nov27 0:00 [scsi_eh_1]
root 236 0.0 0.0 0 0 ? S< Nov27 0:00 [scsi_tmf_1]
root 239 0.0 0.0 0 0 ? S< Nov27 0:00 [ttm_swap]
root 252 0.0 0.0 0 0 ? S< Nov27 0:00 [kworker/0:1H]
root 260 0.0 0.0 0 0 ? S Nov27 0:00 [jbd2/vda1-8]
root 261 0.0 0.0 0 0 ? S< Nov27 0:00 [ext4-rsv-conver]
root 328 0.0 0.7 36828 7592 ? Ss Nov27 0:00 /usr/lib/systemd/systemd-journald
root 348 0.0 0.2 44040 2052 ? Ss Nov27 0:00 /usr/lib/systemd/systemd-udevd
root 413 0.0 0.0 0 0 ? S< Nov27 0:00 [edac-poller]
root 442 0.0 0.0 55452 888 ? S<sl Nov27 0:00 /sbin/auditd
polkitd 465 0.0 1.0 534132 11004 ? Ssl Nov27 0:00 /usr/lib/polkit-1/polkitd --no-debug
root 467 0.0 0.4 214248 4952 ? Ssl Nov27 0:01 /usr/sbin/rsyslogd -n
root 469 0.0 0.1 24204 1664 ? Ss Nov27 0:00 /usr/lib/systemd/systemd-logind
dbus 470 0.0 0.1 24424 1480 ? Ss Nov27 0:00 /bin/dbus-daemon --system --address=systemd: --nofork --n
root 483 0.0 0.0 25856 940 ? Ss Nov27 0:00 /usr/sbin/atd -f
root 486 0.0 0.1 126236 1592 ? Ss Nov27 0:00 /usr/sbin/crond -n
root 493 0.0 0.0 110044 832 tty1 Ss+ Nov27 0:00 /sbin/agetty --noclear tty1 linux
root 844 0.0 1.6 562388 16608 ? Ssl Nov27 0:05 /usr/bin/python -Es /usr/sbin/tuned -l -P
ntp 859 0.0 0.2 29904 2100 ? Ss Nov27 0:00 /usr/sbin/ntpd -u ntp:ntp -g
root 885 0.0 0.2 31412 2564 ? Ssl Nov27 0:24 /usr/local/aegis/aegis_update/AliYunDunUpdate
root 952 0.1 1.2 129228 12596 ? Ssl Nov27 1:17 /usr/local/aegis/aegis_client/aegis_10_33/AliYunDun
root 1080 0.0 0.4 105996 4112 ? Ss Nov27 0:00 /usr/sbin/sshd -D
root 1133 0.0 0.0 1540 580 ? Ss Nov27 0:21 /usr/sbin/aliyun-service
root 1183 0.0 0.0 0 0 ? R Nov27 0:05 [kworker/0:0]
root 1272 0.0 1.3 214648 13944 ? Ss Nov27 0:05 /usr/bin/python2 /usr/bin/ssserver -c /etc/shadowsocks.js
root 11465 0.0 0.5 145700 5152 ? Ss 14:24 0:00 sshd: root@pts/1
root 11467 0.0 0.1 115392 2012 pts/1 Ss 14:24 0:00 -bash
root 11541 0.0 0.1 151064 1812 pts/1 R+ 14:58 0:00 ps aux
说明: STAT表示进程状态。
- D:不能中断的进程
- R:run状态的进程
- S:sleep状态的进程
- s:主进程
- T:暂停的进程
- Z:僵尸进程
- <:高优先级进程
- N:低优先级进程
- L:内存中被锁定了内存分页
- l:多线程进程
- +:前台进程
ps -elf
[root@chamhk ~]# ps -elf
F S UID PID PPID C PRI NI ADDR SZ WCHAN STIME TTY TIME CMD
4 S root 1 0 0 80 0 - 10821 ep_pol Nov27 ? 00:00:00 /usr/lib/systemd/systemd --switched-root --syst
1 S root 2 0 0 80 0 - 0 kthrea Nov27 ? 00:00:00 [kthreadd]
1 S root 3 2 0 80 0 - 0 smpboo Nov27 ? 00:00:00 [ksoftirqd/0]
1 S root 5 2 0 60 -20 - 0 worker Nov27 ? 00:00:00 [kworker/0:0H]
1 S root 6 2 0 80 0 - 0 worker Nov27 ? 00:00:00 [kworker/u2:0]
1 S root 7 2 0 -40 - - 0 smpboo Nov27 ? 00:00:00 [migration/0]
1 S root 8 2 0 80 0 - 0 rcu_gp Nov27 ? 00:00:00 [rcu_bh]
1 R root 9 2 0 80 0 - 0 - Nov27 ? 00:00:01 [rcu_sched]
5 S root 10 2 0 -40 - - 0 smpboo Nov27 ? 00:00:00 [watchdog/0]
5 S root 12 2 0 80 0 - 0 devtmp Nov27 ? 00:00:00 [kdevtmpfs]
1 S root 13 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [netns]
1 S root 14 2 0 80 0 - 0 watchd Nov27 ? 00:00:00 [khungtaskd]
1 S root 15 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [writeback]
1 S root 16 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [kintegrityd]
1 S root 17 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [bioset]
1 S root 18 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [kblockd]
1 S root 19 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [md]
1 S root 25 2 0 80 0 - 0 kswapd Nov27 ? 00:00:00 [kswapd0]
1 S root 26 2 0 85 5 - 0 ksm_sc Nov27 ? 00:00:00 [ksmd]
1 S root 27 2 0 99 19 - 0 khugep Nov27 ? 00:00:00 [khugepaged]
1 S root 28 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [crypto]
1 S root 36 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [kthrotld]
1 S root 37 2 0 80 0 - 0 worker Nov27 ? 00:00:00 [kworker/u2:1]
1 S root 38 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [kmpath_rdacd]
1 S root 39 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [kpsmoused]
1 S root 40 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [ipv6_addrconf]
1 S root 59 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [deferwq]
1 S root 91 2 0 80 0 - 0 kaudit Nov27 ? 00:00:00 [kauditd]
1 S root 92 2 0 80 0 - 0 worker Nov27 ? 00:00:00 [kworker/0:2]
1 S root 214 2 0 80 0 - 0 worker Nov27 ? 00:00:03 [kworker/0:3]
1 S root 225 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [ata_sff]
1 S root 233 2 0 80 0 - 0 scsi_e Nov27 ? 00:00:00 [scsi_eh_0]
1 S root 234 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [scsi_tmf_0]
1 S root 235 2 0 80 0 - 0 scsi_e Nov27 ? 00:00:00 [scsi_eh_1]
1 S root 236 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [scsi_tmf_1]
1 S root 239 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [ttm_swap]
1 S root 252 2 0 60 -20 - 0 worker Nov27 ? 00:00:00 [kworker/0:1H]
1 S root 260 2 0 80 0 - 0 kjourn Nov27 ? 00:00:00 [jbd2/vda1-8]
1 S root 261 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [ext4-rsv-conver]
4 S root 328 1 0 80 0 - 9207 ep_pol Nov27 ? 00:00:00 /usr/lib/systemd/systemd-journald
4 S root 348 1 0 80 0 - 11010 ep_pol Nov27 ? 00:00:00 /usr/lib/systemd/systemd-udevd
1 S root 413 2 0 60 -20 - 0 rescue Nov27 ? 00:00:00 [edac-poller]
5 S root 442 1 0 76 -4 - 13863 ep_pol Nov27 ? 00:00:00 /sbin/auditd
4 S polkitd 465 1 0 80 0 - 133533 poll_s Nov27 ? 00:00:00 /usr/lib/polkit-1/polkitd --no-debug
4 S root 467 1 0 80 0 - 53562 poll_s Nov27 ? 00:00:01 /usr/sbin/rsyslogd -n
4 S root 469 1 0 80 0 - 6051 ep_pol Nov27 ? 00:00:00 /usr/lib/systemd/systemd-logind
4 S dbus 470 1 0 80 0 - 6106 ep_pol Nov27 ? 00:00:00 /bin/dbus-daemon --system --address=systemd: --
4 S root 483 1 0 80 0 - 6464 hrtime Nov27 ? 00:00:00 /usr/sbin/atd -f
4 S root 486 1 0 80 0 - 31559 hrtime Nov27 ? 00:00:00 /usr/sbin/crond -n
4 S root 493 1 0 80 0 - 27511 n_tty_ Nov27 tty1 00:00:00 /sbin/agetty --noclear tty1 linux
4 S root 844 1 0 80 0 - 140597 poll_s Nov27 ? 00:00:05 /usr/bin/python -Es /usr/sbin/tuned -l -P
5 S ntp 859 1 0 80 0 - 7476 poll_s Nov27 ? 00:00:00 /usr/sbin/ntpd -u ntp:ntp -g
1 S root 885 1 0 80 0 - 7853 hrtime Nov27 ? 00:00:24 /usr/local/aegis/aegis_update/AliYunDunUpdate
5 S root 952 1 0 80 0 - 32307 hrtime Nov27 ? 00:01:18 /usr/local/aegis/aegis_client/aegis_10_33/AliYu
4 S root 1080 1 0 80 0 - 26499 poll_s Nov27 ? 00:00:00 /usr/sbin/sshd -D
4 S root 1133 1 0 80 0 - 385 hrtime Nov27 ? 00:00:22 /usr/sbin/aliyun-service
1 R root 1183 2 0 80 0 - 0 - Nov27 ? 00:00:05 [kworker/0:0]
5 S root 1272 1 0 80 0 - 53662 ep_pol Nov27 ? 00:00:05 /usr/bin/python2 /usr/bin/ssserver -c /etc/shad
4 S root 11465 1080 0 80 0 - 36425 poll_s 14:24 ? 00:00:00 sshd: root@pts/1
4 S root 11467 11465 0 80 0 - 28848 do_wai 14:24 pts/1 00:00:00 -bash
0 R root 11566 11467 0 80 0 - 37766 - 15:11 pts/1 00:00:00 ps -elf
转:
进程/线程
进程
>进程(Process)是计算机中的程序关于某数据集合上的一次运行活动,是系统进行资源分配和调度的基本单位,是操作系统结构的基础。在早期面向进程设计的计算机结构中,进程是程序的基本执行实体;在当代面向线程设计的计算机结构中,进程是线程的容器。程序是指令、数据及其组织形式的描述,进程是程序的实体。
状态分类
进程执行时的间断性,决定了进程可能具有多种状态。事实上,运行中的进程可能具有以下三种基本状态:
- 就绪状态(Ready):进程已获得除处理器外的所需资源,等待分配处理器资源;只要分配了处理器进程就可执行。就绪进程可以按多个优先级来划分队列。例如,当一个进程由于时间片用完而进入就绪状态时,排入低优先级队列;当进程由I/O操作完成而进入就绪状态时,排入高优先级队列。
- 运行状态(Running):进程占用处理器资源;处于此状态的进程的数目小于等于处理器的数目。在没有其他进程可以执行时(如所有进程都在阻塞状态),通常会自动执行系统的空闲进程。
- 阻塞状态(Blocked):由于进程等待某种条件(如I/O操作或进程同步),在条件满足之前无法继续执行。该事件发生前即使把处理机分配给该进程,也无法运行。
线程
>线程,有时被称为轻量级进程(Lightweight Process,LWP),是程序执行流的最小单元。一个标准的线程由线程ID,当前指令指针(PC),寄存器集合和堆栈组成。另外,线程是进程中的一个实体,是被系统独立调度和分派的基本单位,线程自己不拥有系统资源,只拥有一点儿在运行中必不可少的资源,但它可与同属一个进程的其它线程共享进程所拥有的全部资源。一个线程可以创建和撤消另一个线程,同一进程中的多个线程之间可以并发执行。由于线程之间的相互制约,致使线程在运行中呈现出间断性。线程也有就绪、阻塞和运行三种基本状态。每一个程序都至少有一个线程,若程序只有一个线程,那就是程序本身。
在单个程序中同时运行多个线程完成不同的工作,称为多线程。
分类
- 用户级线程:管理过程全部由用户程序完成,操作系统内核心只对进程进行管理。
- 系统级线程(核心级线程):由操作系统内核进行管理。操作系统内核给应用程序提供相应的系统调用和应用程序接口API,以使用户程序可以创建、执行、撤消线程。
进程和线程关系:
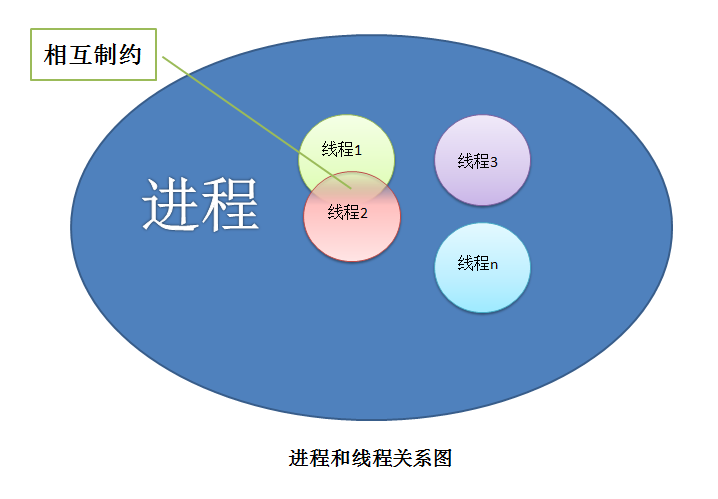 转:
转:
10.9 查看网络状态
netstat命令
>netstat命令用来打印Linux中网络系统的状态信息,可让你得知整个Linux系统的网络情况。
语法: netstat [options]
Options:
-a:=all 显示所有连线中的socket
-l:=listening 显示监控中的服务器的socket
-n:=numeric 直接使用IP地址
-p:=programs 显示正在使用socket的程序识别码和程序名称
-t:=tcp 显示tcp传输协议的连接状况
netstat -lnp 查看监听端口
[root@cham2 ~]# netstat -lnp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1132/sshd
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 2004/master
tcp6 0 0 :::22 :::* LISTEN 1132/sshd
tcp6 0 0 ::1:25 :::* LISTEN 2004/master
udp 0 0 127.0.0.1:323 0.0.0.0:* 530/chronyd
udp6 0 0 ::1:323 :::* 530/chronyd
raw6 0 0 :::58 :::* 7 568/NetworkManager
Active UNIX domain sockets (only servers)
Proto RefCnt Flags Type State I-Node PID/Program name Path
unix 2 [ ACC ] STREAM LISTENING 12385 1/systemd /run/systemd/private
unix 2 [ ACC ] STREAM LISTENING 18782 2004/master private/tlsmgr
unix 2 [ ACC ] STREAM LISTENING 18800 2004/master public/flush
unix 2 [ ACC ] STREAM LISTENING 18295 2004/master public/showq
unix 2 [ ACC ] STREAM LISTENING 12401 1/systemd /run/lvm/lvmetad.socket
unix 2 [ ACC ] STREAM LISTENING 8074 1/systemd /run/systemd/journal/stdout
unix 2 [ ACC ] STREAM LISTENING 12461 1/systemd /run/lvm/lvmpolld.socket
unix 2 [ ACC ] SEQPACKET LISTENING 12473 1/systemd /run/udev/control
unix 2 [ ACC ] STREAM LISTENING 18304 2004/master private/discard
unix 2 [ ACC ] STREAM LISTENING 18307 2004/master private/local
unix 2 [ ACC ] STREAM LISTENING 18310 2004/master private/virtual
unix 2 [ ACC ] STREAM LISTENING 18313 2004/master private/lmtp
unix 2 [ ACC ] STREAM LISTENING 18316 2004/master private/anvil
unix 2 [ ACC ] STREAM LISTENING 18319 2004/master private/scache
unix 2 [ ACC ] STREAM LISTENING 18785 2004/master private/rewrite
unix 2 [ ACC ] STREAM LISTENING 18788 2004/master private/bounce
unix 2 [ ACC ] STREAM LISTENING 18791 2004/master private/defer
unix 2 [ ACC ] STREAM LISTENING 18794 2004/master private/trace
unix 2 [ ACC ] STREAM LISTENING 18797 2004/master private/verify
unix 2 [ ACC ] STREAM LISTENING 18283 2004/master private/proxymap
unix 2 [ ACC ] STREAM LISTENING 18286 2004/master private/proxywrite
unix 2 [ ACC ] STREAM LISTENING 18771 2004/master public/pickup
unix 2 [ ACC ] STREAM LISTENING 18289 2004/master private/smtp
unix 2 [ ACC ] STREAM LISTENING 18292 2004/master private/relay
unix 2 [ ACC ] STREAM LISTENING 18775 2004/master public/cleanup
unix 2 [ ACC ] STREAM LISTENING 18298 2004/master private/error
unix 2 [ ACC ] STREAM LISTENING 18301 2004/master private/retry
unix 2 [ ACC ] STREAM LISTENING 18778 2004/master public/qmgr
unix 2 [ ACC ] STREAM LISTENING 14584 1/systemd /var/run/dbus/system_bus_socket
netstat -an 查看系统网络连接状况
[root@cham2 ~]# netstat -an
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN
tcp 0 52 192.168.230.135:22 192.168.230.1:62110 ESTABLISHED
tcp6 0 0 :::22 :::* LISTEN
tcp6 0 0 ::1:25 :::* LISTEN
udp 0 0 127.0.0.1:323 0.0.0.0:*
udp6 0 0 ::1:323 :::*
raw6 0 0 :::58 :::* 7
Active UNIX domain sockets (servers and established)
Proto RefCnt Flags Type State I-Node Path
unix 2 [ ACC ] STREAM LISTENING 12385 /run/systemd/private
unix 2 [ ACC ] STREAM LISTENING 18782 private/tlsmgr
unix 2 [ ] DGRAM 12393 /run/systemd/shutdownd
unix 2 [ ACC ] STREAM LISTENING 18800 public/flush
unix 2 [ ACC ] STREAM LISTENING 18295 public/showq
unix 2 [ ACC ] STREAM LISTENING 12401 /run/lvm/lvmetad.socket
unix 2 [ ] DGRAM 8057 /run/systemd/notify
unix 2 [ ] DGRAM 8059 /run/systemd/cgroups-agent
unix 2 [ ACC ] STREAM LISTENING 8074 /run/systemd/journal/stdout
unix 5 [ ] DGRAM 8077 /run/systemd/journal/socket
unix 12 [ ] DGRAM 8079 /dev/log
unix 2 [ ACC ] STREAM LISTENING 12461 /run/lvm/lvmpolld.socket
unix 2 [ ACC ] SEQPACKET LISTENING 12473 /run/udev/control
unix 2 [ ACC ] STREAM LISTENING 18304 private/discard
unix 2 [ ACC ] STREAM LISTENING 18307 private/local
unix 2 [ ACC ] STREAM LISTENING 18310 private/virtual
unix 2 [ ACC ] STREAM LISTENING 18313 private/lmtp
unix 2 [ ACC ] STREAM LISTENING 18316 private/anvil
unix 2 [ ACC ] STREAM LISTENING 18319 private/scache
unix 2 [ ACC ] STREAM LISTENING 18785 private/rewrite
unix 2 [ ACC ] STREAM LISTENING 18788 private/bounce
unix 2 [ ACC ] STREAM LISTENING 18791 private/defer
unix 2 [ ACC ] STREAM LISTENING 18794 private/trace
unix 2 [ ACC ] STREAM LISTENING 18797 private/verify
unix 2 [ ACC ] STREAM LISTENING 18283 private/proxymap
unix 2 [ ACC ] STREAM LISTENING 18286 private/proxywrite
unix 2 [ ACC ] STREAM LISTENING 18771 public/pickup
unix 2 [ ACC ] STREAM LISTENING 18289 private/smtp
unix 2 [ ACC ] STREAM LISTENING 18292 private/relay
unix 2 [ ACC ] STREAM LISTENING 18775 public/cleanup
unix 2 [ ACC ] STREAM LISTENING 18298 private/error
unix 2 [ ACC ] STREAM LISTENING 18301 private/retry
unix 2 [ ACC ] STREAM LISTENING 18778 public/qmgr
unix 2 [ ACC ] STREAM LISTENING 14584 /var/run/dbus/system_bus_socket
unix 3 [ ] STREAM CONNECTED 13990 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 14711
unix 2 [ ] DGRAM 18413
unix 3 [ ] STREAM CONNECTED 18780
unix 3 [ ] STREAM CONNECTED 13873
unix 3 [ ] STREAM CONNECTED 18282
unix 3 [ ] STREAM CONNECTED 18288
unix 2 [ ] DGRAM 123956
unix 2 [ ] DGRAM 13871
unix 2 [ ] DGRAM 18269
unix 2 [ ] DGRAM 14312
unix 3 [ ] STREAM CONNECTED 18787
unix 3 [ ] STREAM CONNECTED 18783
unix 3 [ ] STREAM CONNECTED 13872
unix 3 [ ] STREAM CONNECTED 18779
unix 3 [ ] STREAM CONNECTED 18287
unix 3 [ ] STREAM CONNECTED 14994
unix 3 [ ] STREAM CONNECTED 15517 /var/run/dbus/system_bus_socket
unix 3 [ ] STREAM CONNECTED 18281
unix 3 [ ] STREAM CONNECTED 18776
unix 3 [ ] STREAM CONNECTED 15516
unix 2 [ ] DGRAM 14278
unix 2 [ ] DGRAM 77401
unix 3 [ ] STREAM CONNECTED 18284
unix 3 [ ] STREAM CONNECTED 18769
unix 3 [ ] STREAM CONNECTED 14310 /var/run/dbus/system_bus_socket
unix 3 [ ] STREAM CONNECTED 18285
unix 3 [ ] STREAM CONNECTED 14217 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 18290
unix 3 [ ] STREAM CONNECTED 18795
unix 3 [ ] STREAM CONNECTED 15036
unix 3 [ ] STREAM CONNECTED 18305
unix 2 [ ] DGRAM 122722
unix 3 [ ] STREAM CONNECTED 18306
unix 3 [ ] STREAM CONNECTED 17146
unix 3 [ ] STREAM CONNECTED 14774 /var/run/dbus/system_bus_socket
unix 3 [ ] STREAM CONNECTED 12849
unix 3 [ ] STREAM CONNECTED 18300
unix 3 [ ] STREAM CONNECTED 14127
unix 3 [ ] STREAM CONNECTED 18302
unix 3 [ ] STREAM CONNECTED 15392 /var/run/dbus/system_bus_socket
unix 3 [ ] STREAM CONNECTED 18572
unix 3 [ ] STREAM CONNECTED 18303
unix 3 [ ] STREAM CONNECTED 14772
unix 3 [ ] STREAM CONNECTED 18297
unix 3 [ ] STREAM CONNECTED 18784
unix 3 [ ] STREAM CONNECTED 15178
unix 3 [ ] STREAM CONNECTED 14128 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 18790
unix 3 [ ] STREAM CONNECTED 18299
unix 3 [ ] DGRAM 12132
unix 3 [ ] STREAM CONNECTED 18293
unix 3 [ ] DGRAM 12133
unix 3 [ ] STREAM CONNECTED 18294
unix 2 [ ] DGRAM 14756
unix 3 [ ] STREAM CONNECTED 18291
unix 3 [ ] STREAM CONNECTED 14762
unix 3 [ ] STREAM CONNECTED 15179 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 18296
unix 3 [ ] STREAM CONNECTED 18786
unix 3 [ ] STREAM CONNECTED 18320
unix 2 [ ] DGRAM 13994
unix 3 [ ] STREAM CONNECTED 18321
unix 3 [ ] STREAM CONNECTED 15221 /var/run/dbus/system_bus_socket
unix 3 [ ] STREAM CONNECTED 14754
unix 3 [ ] STREAM CONNECTED 15220
unix 3 [ ] STREAM CONNECTED 18792
unix 3 [ ] STREAM CONNECTED 12895
unix 3 [ ] STREAM CONNECTED 13991 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 13970
unix 3 [ ] STREAM CONNECTED 18317
unix 3 [ ] STREAM CONNECTED 18789
unix 3 [ ] STREAM CONNECTED 18318
unix 2 [ ] DGRAM 15441
unix 3 [ ] STREAM CONNECTED 18793
unix 3 [ ] STREAM CONNECTED 12896 /run/systemd/journal/stdout
unix 2 [ ] DGRAM 14777
unix 3 [ ] STREAM CONNECTED 13988
unix 3 [ ] STREAM CONNECTED 18773
unix 3 [ ] STREAM CONNECTED 18798
unix 3 [ ] STREAM CONNECTED 18312
unix 3 [ ] STREAM CONNECTED 18772
unix 3 [ ] STREAM CONNECTED 18799
unix 3 [ ] STREAM CONNECTED 18777
unix 3 [ ] STREAM CONNECTED 18796
unix 3 [ ] STREAM CONNECTED 17476 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 12850 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 18314
unix 3 [ ] STREAM CONNECTED 14775 /var/run/dbus/system_bus_socket
unix 3 [ ] STREAM CONNECTED 18770
unix 3 [ ] STREAM CONNECTED 13971 /run/systemd/journal/stdout
unix 3 [ ] STREAM CONNECTED 18315
unix 3 [ ] STREAM CONNECTED 18573 /var/run/dbus/system_bus_socket
unix 2 [ ] DGRAM 12901
unix 3 [ ] STREAM CONNECTED 18308
unix 3 [ ] STREAM CONNECTED 15138
unix 3 [ ] STREAM CONNECTED 18309
unix 3 [ ] STREAM CONNECTED 14773
unix 3 [ ] STREAM CONNECTED 18311
netstat -lntp 只看tcp协议连接,不看socket
[root@cham2 ~]# netstat -lntp
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1132/sshd
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 2004/master
tcp6 0 0 :::22 :::* LISTEN 1132/sshd
tcp6 0 0 ::1:25 :::* LISTEN 2004/master 补充: 查看tcp协议状态的命令:
[root@cham2 ~]# netstat -an | awk '/^tcp/ {++sta[$NF]} END {for(key in sta) print key,"\t",sta[key]}'
LISTEN 4
ESTABLISHED 1
ss命令
>ss命令用来显示处于活动状态的套接字信息。ss命令可以用来获取socket统计信息,它可以显示和netstat类似的内容。但ss的优势在于它能够显示更多更详细的有关TCP和连接状态的信息,而且比netstat更快速更高效,缺点是不会显示进程的名称。
语法: ss [options]
Options:
-a:显示所有套接字(socket)
-n:不解析服务器名称,以数字方式显示
[root@cham2 ~]# ss -an
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
nl UNCONN 0 0 0:-2139094472 *
nl UNCONN 0 0 0:0 *
nl UNCONN 0 0 0:-2139094472 *
nl UNCONN 4352 0 4:4193 *
nl UNCONN 768 0 4:0 *
nl UNCONN 0 0 6:0 *
nl UNCONN 0 0 7:0 *
nl UNCONN 0 0 9:0 *
nl UNCONN 0 0 9:1 *
nl UNCONN 0 0 9:502 *
nl UNCONN 0 0 10:0 *
nl UNCONN 0 0 11:0 *
nl UNCONN 0 0 12:0 *
nl UNCONN 0 0 15:867 *
nl UNCONN 768 0 15:-4109 *
nl UNCONN 0 0 15:-4126 *
nl UNCONN 0 0 15:568 *
nl UNCONN 0 0 15:523 *
nl UNCONN 0 0 15:0 *
nl UNCONN 0 0 15:-4122 *
nl UNCONN 0 0 15:-4121 *
nl UNCONN 0 0 15:1 *
nl UNCONN 0 0 15:-4123 *
nl UNCONN 0 0 15:867 *
nl UNCONN 0 0 15:-4126 *
nl UNCONN 0 0 15:568 *
nl UNCONN 0 0 15:-4123 *
nl UNCONN 0 0 15:-4122 *
nl UNCONN 0 0 15:-4121 *
nl UNCONN 0 0 15:523 *
nl UNCONN 768 0 15:-4109 *
nl UNCONN 0 0 15:1 *
nl UNCONN 0 0 16:0 *
nl UNCONN 0 0 18:0 *
u_str LISTEN 0 128 /run/systemd/private 12385 * 0
u_str LISTEN 0 100 private/tlsmgr 18782 * 0
u_dgr UNCONN 0 0 /run/systemd/shutdownd 12393 * 0
u_str LISTEN 0 100 public/flush 18800 * 0
u_str LISTEN 0 100 public/showq 18295 * 0
u_str LISTEN 0 128 /run/lvm/lvmetad.socket 12401 * 0
u_dgr UNCONN 0 0 /run/systemd/notify 8057 * 0
u_dgr UNCONN 0 0 /run/systemd/cgroups-agent 8059 * 0
u_str LISTEN 0 128 /run/systemd/journal/stdout 8074 * 0
u_dgr UNCONN 0 0 /run/systemd/journal/socket 8077 * 0
u_dgr UNCONN 0 0 /dev/log 8079 * 0
u_str LISTEN 0 128 /run/lvm/lvmpolld.socket 12461 * 0
u_seq LISTEN 0 128 /run/udev/control 12473 * 0
u_str LISTEN 0 100 private/discard 18304 * 0
u_str LISTEN 0 100 private/local 18307 * 0
u_str LISTEN 0 100 private/virtual 18310 * 0
u_str LISTEN 0 100 private/lmtp 18313 * 0
u_str LISTEN 0 100 private/anvil 18316 * 0
u_str LISTEN 0 100 private/scache 18319 * 0
u_str LISTEN 0 100 private/rewrite 18785 * 0
u_str LISTEN 0 100 private/bounce 18788 * 0
u_str LISTEN 0 100 private/defer 18791 * 0
u_str LISTEN 0 100 private/trace 18794 * 0
u_str LISTEN 0 100 private/verify 18797 * 0
u_str LISTEN 0 100 private/proxymap 18283 * 0
u_str LISTEN 0 100 private/proxywrite 18286 * 0
u_str LISTEN 0 100 public/pickup 18771 * 0
u_str LISTEN 0 100 private/smtp 18289 * 0
u_str LISTEN 0 100 private/relay 18292 * 0
u_str LISTEN 0 100 public/cleanup 18775 * 0
u_str LISTEN 0 100 private/error 18298 * 0
u_str LISTEN 0 100 private/retry 18301 * 0
u_str LISTEN 0 100 public/qmgr 18778 * 0
u_str LISTEN 0 128 /var/run/dbus/system_bus_socket 14584 * 0
u_str ESTAB 0 0 /run/systemd/journal/stdout 13990 * 14711
u_str ESTAB 0 0 * 14711 * 13990
u_dgr UNCONN 0 0 * 18413 * 8079
u_str ESTAB 0 0 * 18780 * 18779
u_str ESTAB 0 0 * 13873 * 13872
u_str ESTAB 0 0 * 18282 * 18281
u_str ESTAB 0 0 * 18288 * 18287
u_dgr UNCONN 0 0 * 123956 * 8079
u_dgr UNCONN 0 0 * 13871 * 8079
u_dgr UNCONN 0 0 * 18269 * 8079
u_dgr UNCONN 0 0 * 14312 * 8079
u_str ESTAB 0 0 * 18787 * 18786
u_str ESTAB 0 0 * 18783 * 18784
u_str ESTAB 0 0 * 13872 * 13873
u_str ESTAB 0 0 * 18779 * 18780
u_str ESTAB 0 0 * 18287 * 18288
u_str ESTAB 0 0 * 14994 * 14217
u_str ESTAB 0 0 /var/run/dbus/system_bus_socket 15517 * 15516
u_str ESTAB 0 0 * 18281 * 18282
u_str ESTAB 0 0 * 18776 * 18777
u_str ESTAB 0 0 * 15516 * 15517
u_dgr UNCONN 0 0 * 14278 * 8079
u_dgr UNCONN 0 0 * 77401 * 8077
u_str ESTAB 0 0 * 18284 * 18285
u_str ESTAB 0 0 * 18769 * 18770
u_str ESTAB 0 0 /var/run/dbus/system_bus_socket 14310 * 15036
u_str ESTAB 0 0 * 18285 * 18284
u_str ESTAB 0 0 /run/systemd/journal/stdout 14217 * 14994
u_str ESTAB 0 0 * 18290 * 18291
u_str ESTAB 0 0 * 18795 * 18796
u_str ESTAB 0 0 * 15036 * 14310
u_str ESTAB 0 0 * 18305 * 18306
u_dgr UNCONN 0 0 * 122722 * 8079
u_str ESTAB 0 0 * 18306 * 18305
u_str ESTAB 0 0 * 17146 * 17476
u_str ESTAB 0 0 /var/run/dbus/system_bus_socket 14774 * 13988
u_str ESTAB 0 0 * 12849 * 12850
u_str ESTAB 0 0 * 18300 * 18299
u_str ESTAB 0 0 * 14127 * 14128
u_str ESTAB 0 0 * 18302 * 18303
u_str ESTAB 0 0 /var/run/dbus/system_bus_socket 15392 * 15138
u_str ESTAB 0 0 * 18572 * 18573
u_str ESTAB 0 0 * 18303 * 18302
u_str ESTAB 0 0 * 14772 * 14773
u_str ESTAB 0 0 * 18297 * 18296
u_str ESTAB 0 0 * 18784 * 18783
u_str ESTAB 0 0 * 15178 * 15179
u_str ESTAB 0 0 /run/systemd/journal/stdout 14128 * 14127
u_str ESTAB 0 0 * 18790 * 18789
u_str ESTAB 0 0 * 18299 * 18300
u_dgr UNCONN 0 0 * 12132 * 12133
u_str ESTAB 0 0 * 18293 * 18294
u_dgr UNCONN 0 0 * 12133 * 12132
u_str ESTAB 0 0 * 18294 * 18293
u_dgr UNCONN 0 0 * 14756 * 8077
u_str ESTAB 0 0 * 18291 * 18290
u_str ESTAB 0 0 * 14762 * 14775
u_str ESTAB 0 0 /run/systemd/journal/stdout 15179 * 15178
u_str ESTAB 0 0 * 18296 * 18297
u_str ESTAB 0 0 * 18786 * 18787
u_str ESTAB 0 0 * 18320 * 18321
u_dgr UNCONN 0 0 * 13994 * 8079
u_str ESTAB 0 0 * 18321 * 18320
u_str ESTAB 0 0 /var/run/dbus/system_bus_socket 15221 * 15220
u_str ESTAB 0 0 * 14754 * 13991
u_str ESTAB 0 0 * 15220 * 15221
u_str ESTAB 0 0 * 18792 * 18793
u_str ESTAB 0 0 * 12895 * 12896
u_str ESTAB 0 0 /run/systemd/journal/stdout 13991 * 14754
u_str ESTAB 0 0 * 13970 * 13971
u_str ESTAB 0 0 * 18317 * 18318
u_str ESTAB 0 0 * 18789 * 18790
u_str ESTAB 0 0 * 18318 * 18317
u_dgr UNCONN 0 0 * 15441 * 8079
u_str ESTAB 0 0 * 18793 * 18792
u_str ESTAB 0 0 /run/systemd/journal/stdout 12896 * 12895
u_dgr UNCONN 0 0 * 14777 * 8079
u_str ESTAB 0 0 * 13988 * 14774
u_str ESTAB 0 0 * 18773 * 18772
u_str ESTAB 0 0 * 18798 * 18799
u_str ESTAB 0 0 * 18312 * 18311
u_str ESTAB 0 0 * 18772 * 18773
u_str ESTAB 0 0 * 18799 * 18798
u_str ESTAB 0 0 * 18777 * 18776
u_str ESTAB 0 0 * 18796 * 18795
u_str ESTAB 0 0 /run/systemd/journal/stdout 17476 * 17146
u_str ESTAB 0 0 /run/systemd/journal/stdout 12850 * 12849
u_str ESTAB 0 0 * 18314 * 18315
u_str ESTAB 0 0 /var/run/dbus/system_bus_socket 14775 * 14762
u_str ESTAB 0 0 * 18770 * 18769
u_str ESTAB 0 0 /run/systemd/journal/stdout 13971 * 13970
u_str ESTAB 0 0 * 18315 * 18314
u_str ESTAB 0 0 /var/run/dbus/system_bus_socket 18573 * 18572
u_dgr UNCONN 0 0 * 12901 * 8077
u_str ESTAB 0 0 * 18308 * 18309
u_str ESTAB 0 0 * 15138 * 15392
u_str ESTAB 0 0 * 18309 * 18308
u_str ESTAB 0 0 * 14773 * 14772
u_str ESTAB 0 0 * 18311 * 18312
udp UNCONN 0 0 :::58 :::*
udp UNCONN 0 0 127.0.0.1:323 *:*
udp ESTAB 0 0 192.168.230.135:49787 193.228.143.24:123
udp UNCONN 0 0 ::1:323 :::*
tcp LISTEN 0 128 *:22 *:*
tcp LISTEN 0 100 127.0.0.1:25 *:*
tcp ESTAB 0 436 192.168.230.135:22 192.168.230.1:62110
tcp LISTEN 0 128 :::22 :::*
tcp LISTEN 0 100 ::1:25 :::* *
10.10 Linux下抓包
tcpdump命令
>tcpdump命令是一款sniffer工具,它可以打印所有经过网络接口的数据包的头信息,也可以使用-w选项将数据包保存到文件中,方便以后分析。
语法: tcpdump [options]
Options:
-i:指定网卡名,使用指定的网络送出数据包
-c:指定数量
-w:指定存放位置
-r:=read,从指定文件查看数据包数据
如果这个命令没有要安装一下
![]()
用法
- tcpdump -nn -i ens33 (第一个n表示以数字形式显示IP,如果不加该选项会显示成主机名)
- tcpdump -nn ens33 port 22 (not port 22)指定端口为22的(或者非22的)
- tcpdump -nn ens33 port 22 and host 192.168.8.1 指定多个条件(host:主机,后面跟主机名或IP)
tcpdump -nn -i ens33 -c 10 -w /tmp/1.cap 指定抓包数量和存放位置
[root@cham2 ~]# tcpdump -nn -i ens33 -c 100 -w /tmp/1.cap
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
100 packets captured
100 packets received by filter
0 packets dropped by kernel
[root@cham2 ~]#
注: 1.cap内容无法使用cat命令查看,可使用tcpdump -r命令查看 。说明: 包内内容为使用tcpdump打包时的数据。
[root@cham2 ~]# tcpdump -r /tmp/1.cap
reading from file /tmp/1.cap, link-type EN10MB (Ethernet)
20:54:45.405736 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 2296127363:2296127511, ack 2300195262, win 274, length 148
20:54:45.406314 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 148, win 2051, length 0
20:54:48.278262 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 1:53, ack 148, win 2051, length 52
20:54:48.278545 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 148:200, ack 53, win 274, length 52
20:54:48.329076 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 200, win 2051, length 0
20:54:48.377853 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 53:105, ack 200, win 2051, length 52
20:54:48.378023 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 200:252, ack 105, win 274, length 52
20:54:48.428653 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 252, win 2051, length 0
20:54:48.551122 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 105:157, ack 252, win 2051, length 52
20:54:48.551368 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 252:304, ack 157, win 274, length 52
20:54:48.602646 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 304, win 2051, length 0
20:54:48.717765 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 157:209, ack 304, win 2051, length 52
20:54:48.717989 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 304:356, ack 209, win 274, length 52
20:54:48.768624 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 356, win 2050, length 0
20:55:28.289141 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 209:261, ack 356, win 2050, length 52
20:55:28.328993 IP cham2.ssh > 192.168.230.1.62110: Flags [.], ack 261, win 274, length 0
20:55:31.666407 IP6 fe80::ecc9:8745:f5f0:118f > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28
20:55:31.666484 IP 192.168.230.1 > igmp.mcast.net: igmp v3 report, 1 group record(s)
20:55:31.705742 IP6 fe80::ecc9:8745:f5f0:118f > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28
20:55:31.706031 IP 192.168.230.1 > igmp.mcast.net: igmp v3 report, 1 group record(s)
20:55:31.706271 IP6 fe80::ecc9:8745:f5f0:118f > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28
20:55:31.706289 IP 192.168.230.1 > igmp.mcast.net: igmp v3 report, 1 group record(s)
20:55:31.706376 IP6 fe80::ecc9:8745:f5f0:118f > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28
20:55:31.706618 IP 192.168.230.1 > igmp.mcast.net: igmp v3 report, 1 group record(s)
20:55:31.707983 IP6 fe80::ecc9:8745:f5f0:118f.59183 > ff02::1:3.hostmon: UDP, length 31
20:55:31.708112 IP 192.168.230.1.59183 > 224.0.0.252.hostmon: UDP, length 31
20:55:31.708599 IP 192.168.230.1 > igmp.mcast.net: igmp v3 report, 1 group record(s)
20:55:31.708610 IP6 fe80::ecc9:8745:f5f0:118f > ff02::16: HBH ICMP6, multicast listener report v2, 1 group record(s), length 28
20:55:32.118236 IP6 fe80::ecc9:8745:f5f0:118f.59183 > ff02::1:3.hostmon: UDP, length 31
20:55:32.118269 IP 192.168.230.1.59183 > 224.0.0.252.hostmon: UDP, length 31
20:55:33.209061 ARP, Request who-has cham2 (00:0c:29:b6:9f:e3 (oui Unknown)) tell 192.168.230.1, length 46
20:55:33.209089 ARP, Reply cham2 is-at 00:0c:29:b6:9f:e3 (oui Unknown), length 28
20:55:33.636843 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 261:329, ack 356, win 2050, length 68
20:55:33.636888 IP cham2.ssh > 192.168.230.1.62110: Flags [.], ack 329, win 274, length 0
20:55:33.637110 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 356:424, ack 329, win 274, length 68
20:55:33.688010 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 424, win 2050, length 0
20:55:33.759478 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 329:429, ack 424, win 2050, length 100
20:55:33.759539 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 429:497, ack 424, win 2050, length 68
20:55:33.759640 IP cham2.ssh > 192.168.230.1.62110: Flags [.], ack 497, win 274, length 0
20:55:33.821194 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 424:476, ack 497, win 274, length 52
20:55:33.847875 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 476:592, ack 497, win 274, length 116
20:55:33.848656 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 592, win 2049, length 0
20:55:33.989225 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 592:660, ack 497, win 274, length 68
20:55:33.989329 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 660:744, ack 497, win 274, length 84
20:55:33.989663 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 744, win 2049, length 0
20:55:43.468486 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 497:549, ack 744, win 2049, length 52
20:55:43.469355 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 744:796, ack 549, win 274, length 52
20:55:43.519947 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 796, win 2049, length 0
20:55:43.831105 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 549:601, ack 796, win 2049, length 52
20:55:43.832312 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 796:848, ack 601, win 274, length 52
20:55:43.884999 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 848, win 2048, length 0
20:55:44.236583 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 601:653, ack 848, win 2048, length 52
20:55:44.237996 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 848:900, ack 653, win 274, length 52
20:55:44.288259 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 900, win 2048, length 0
20:55:44.431482 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 653:705, ack 900, win 2048, length 52
20:55:44.432455 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 900:952, ack 705, win 274, length 52
20:55:44.483632 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 952, win 2048, length 0
20:55:44.624520 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 705:757, ack 952, win 2048, length 52
20:55:44.624969 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 952:1004, ack 757, win 274, length 52
20:55:44.675060 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1004, win 2048, length 0
20:55:44.771332 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 757:809, ack 1004, win 2048, length 52
20:55:44.772341 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1004:1056, ack 809, win 274, length 52
20:55:44.822925 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1056, win 2048, length 0
20:55:45.363299 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 809:861, ack 1056, win 2048, length 52
20:55:45.364148 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1056:1108, ack 861, win 274, length 52
20:55:45.415125 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1108, win 2047, length 0
20:55:45.578607 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 861:913, ack 1108, win 2047, length 52
20:55:45.579154 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1108:1160, ack 913, win 274, length 52
20:55:45.629482 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1160, win 2047, length 0
20:55:45.788548 IP 192.168.230.1.62110 > cham2.ssh: Flags [P.], seq 913:965, ack 1160, win 2047, length 52
20:55:45.789183 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1160:1212, ack 965, win 274, length 52
20:55:46.037378 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1160:1212, ack 965, win 274, length 52
20:55:46.182729 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1212, win 2047, length 0
20:55:46.189828 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1212, win 2047, options [nop,nop,sack 1 {1160:1212}], length 0
20:55:46.216175 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1212:1440, ack 965, win 274, length 228
20:55:46.230899 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1440:1588, ack 965, win 274, length 148
20:55:46.231380 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1588, win 2053, length 0
20:55:47.231474 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1588:1736, ack 965, win 274, length 148
20:55:47.282642 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1736, win 2052, length 0
20:55:48.231834 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1736:1884, ack 965, win 274, length 148
20:55:48.281676 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 1884, win 2051, length 0
20:55:49.232834 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 1884:2032, ack 965, win 274, length 148
20:55:49.283453 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 2032, win 2051, length 0
20:55:50.233363 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 2032:2180, ack 965, win 274, length 148
20:55:50.287173 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 2180, win 2050, length 0
20:55:51.233985 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 2180:2328, ack 965, win 274, length 148
20:55:51.284016 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 2328, win 2050, length 0
20:55:52.234651 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 2328:2476, ack 965, win 274, length 148
20:55:52.286437 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 2476, win 2049, length 0
20:55:53.235190 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 2476:2624, ack 965, win 274, length 148
20:55:53.286170 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 2624, win 2049, length 0
20:55:54.236346 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 2624:2772, ack 965, win 274, length 148
20:55:54.287272 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 2772, win 2048, length 0
20:55:55.236896 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 2772:2920, ack 965, win 274, length 148
20:55:55.287429 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 2920, win 2047, length 0
20:55:56.237595 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 2920:3068, ack 965, win 274, length 148
20:55:56.288512 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 3068, win 2053, length 0
20:55:57.238208 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 3068:3216, ack 965, win 274, length 148
20:55:57.288437 IP 192.168.230.1.62110 > cham2.ssh: Flags [.], ack 3216, win 2052, length 0
20:55:58.238551 IP cham2.ssh > 192.168.230.1.62110: Flags [P.], seq 3216:3364, ack 965, win 274, length 148
[root@cham2 ~]#
tshark命令
>该命令也是用于抓包的。
使用前需要安装该工具‘wireshark’:
[root@cham2 ~]# yum install wireshark
已加载插件:fastestmirror
用法
查看指定网卡80端口的1个web服务的访问情况(类似于web的访问日志):
[ 命令:tshark -n -t a -R http.request -T fields -e "frame.time" -e "ip.src" -e "http.host" -e "http.request.method" -e "http.request.uri" ]
[root@chamhk ~]# tshark -n -t a -R http.request -T fields -e "frame.time" -e "ip.src" -e "http.host" -e "http.request.method" -e "http.request.uri"
来源:oschina
链接:https://my.oschina.net/u/3708120/blog/1581219