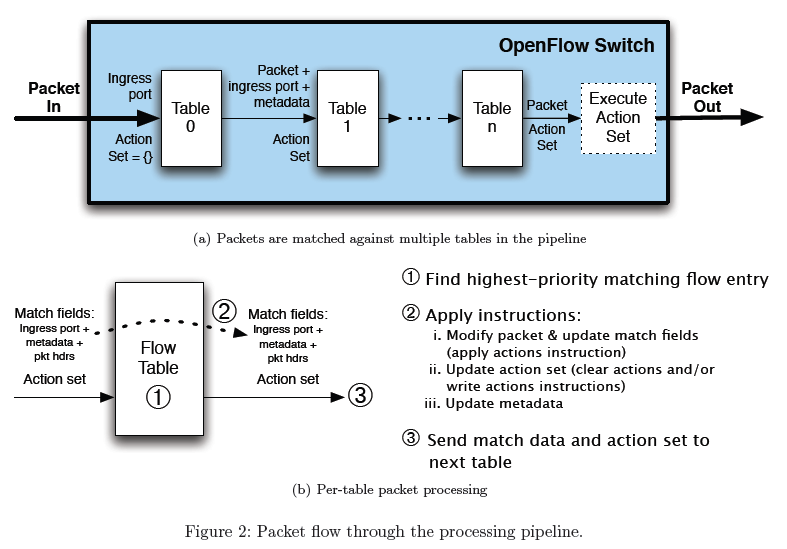
这一节我们将flow table
flow table主要由ovs-ofctl命令操作
ovs-ofctl可以走和openflow controller一样的协议:
- ssl:ip[:port]: The specified SSL port (default: 6633) on the host at the given ip, which must be expressed as an IP address (not a DNS name). The −−private−key, −−certificate, and −−ca−cert options are mandatory when this form is used.
- tcp:ip[:port]: The specified TCP port (default: 6633) on the host at the given ip, which must be expressed as an IP address (not a DNS name).
- unix:file : The Unix domain server socket named file.
管理vswitch
可以查看bridge
# ovs-ofctl show br-tun
OFPT_FEATURES_REPLY (xid=0x2): dpid:0000622d96c07044
n_tables:254, n_buffers:256
capabilities: FLOW_STATS TABLE_STATS PORT_STATS QUEUE_STATS ARP_MATCH_IP
actions: OUTPUT SET_VLAN_VID SET_VLAN_PCP STRIP_VLAN SET_DL_SRC SET_DL_DST SET_NW_SRC SET_NW_DST SET_NW_TOS SET_TP_SRC SET_TP_DST ENQUEUE
1(patch-int): addr:8e:a7:f3:84:2d:ae
config: 0
state: 0
speed: 0 Mbps now, 0 Mbps max
LOCAL(br-tun): addr:62:2d:96:c0:70:44
config: 0
state: 0
speed: 0 Mbps now, 0 Mbps max
OFPT_GET_CONFIG_REPLY (xid=0x4): frags=normal miss_send_len=0
查看所有的flow table
# ovs-ofctl dump-tables br-tun
OFPST_TABLE reply (xid=0x2): 254 tables
0: classifier: wild=0x3fffff, max=1000000, active=2
lookup=70504900, matched=70504899
1: table1 : wild=0x3fffff, max=1000000, active=2
lookup=0, matched=0
2: table2 : wild=0x3fffff, max=1000000, active=2
lookup=0, matched=0
3: table3 : wild=0x3fffff, max=1000000, active=1
lookup=0, matched=0
4: table4 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
5: table5 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
6: table6 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
7: table7 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
8: table8 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
9: table9 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
10: table10 : wild=0x3fffff, max=1000000, active=1
lookup=0, matched=0
11: table11 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
12: table12 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
13: table13 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
14: table14 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
15: table15 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
16: table16 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
17: table17 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
18: table18 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
19: table19 : wild=0x3fffff, max=1000000, active=0
lookup=0, matched=0
20: table20 : wild=0x3fffff, max=1000000, active=1
lookup=0, matched=0
21: table21 : wild=0x3fffff, max=1000000, active=1
lookup=0, matched=0
查看所有的flow
# ovs-ofctl dump-flows br-tun
NXST_FLOW reply (xid=0x4):
cookie=0x0, duration=14863.885s, table=0, n_packets=92, n_bytes=9443, idle_age=378, priority=1,in_port=1 actions=resubmit(,1)
cookie=0x0, duration=14863.84s, table=0, n_packets=5, n_bytes=390, idle_age=14855, priority=0 actions=drop
cookie=0x0, duration=14863.788s, table=1, n_packets=0, n_bytes=0, idle_age=14863, priority=1,dl_dst=00:00:00:00:00:00/01:00:00:00:00:00 actions=resubmit(,20)
cookie=0x0, duration=14863.738s, table=1, n_packets=92, n_bytes=9443, idle_age=378, priority=1,dl_dst=01:00:00:00:00:00/01:00:00:00:00:00 actions=resubmit(,21)
cookie=0x0, duration=14862.459s, table=2, n_packets=0, n_bytes=0, idle_age=14862, priority=1,tun_id=0x1 actions=mod_vlan_vid:1,resubmit(,10)
cookie=0x0, duration=14863.684s, table=2, n_packets=0, n_bytes=0, idle_age=14863, priority=0 actions=drop
cookie=0x0, duration=14863.633s, table=3, n_packets=0, n_bytes=0, idle_age=14863, priority=0 actions=drop
cookie=0x0, duration=14863.574s, table=10, n_packets=0, n_bytes=0, idle_age=14863, priority=1 actions=learn(table=20,hard_timeout=300,priority=1,NXM_OF_VLAN_TCI[0..11],NXM_OF_ETH_DST[]=NXM_OF_ETH_SRC[],load:0->NXM_OF_VLAN_TCI[],load:NXM_NX_TUN_ID[]->NXM_NX_TUN_ID[],output:NXM_OF_IN_PORT[]),output:1
cookie=0x0, duration=14863.529s, table=20, n_packets=0, n_bytes=0, idle_age=14863, priority=0 actions=resubmit(,21)
cookie=0x0, duration=14863.482s, table=21, n_packets=92, n_bytes=9443, idle_age=378, priority=0 actions=drop
查看所有的port的统计
# ovs-ofctl dump-ports br-tun
OFPST_PORT reply (xid=0x2): 2 ports
port 1: rx pkts=92, bytes=9443, drop=0, errs=0, frame=0, over=0, crc=0
tx pkts=0, bytes=0, drop=0, errs=0, coll=0
port LOCAL: rx pkts=8, bytes=648, drop=0, errs=0, frame=0, over=0, crc=0
tx pkts=0, bytes=0, drop=0, errs=0, coll=0
修改port: mod−port switch port action
- up, down Enable or disable the interface.
- stp, no−stp Enable or disable 802.1D spanning tree protocol (STP) on the interface.
- receive, no−receive, receive−stp, no−receive−stp Enable or disable OpenFlow processing of packets received on this interface.
- forward, no−forward Allow or disallow forwarding of traffic to this interface. By default, forwarding is enabled.
- flood, no−flood Controls whether an OpenFlow flood action will send traffic out this interface. By default, flooding is enabled.
- packet−in, no−packet−in Controls whether packets received on this interface that do not match a flow table entry generate a ‘‘packet in’’ message to the OpenFlow controller.
设置以及获得Flag
get−frags switch
set−frags switch frag_mode
- normal: Fragments pass through the flow table like non-fragmented packets. The TCP ports, UDP ports, and ICMP type and code fields are always set to 0, even for fragments where that information would otherwise be available (fragments with offset 0).
- drop: Fragments are dropped without passing through the flow table.
- reassemble: The switch reassembles fragments into full IP packets before passing them through the flow table.
dump−aggregate switch [flows]
- Prints to the console aggregate statistics for flows in switch’s tables that match flows.
$ sudo ovs-ofctl dump-aggregate br-tun
NXST_AGGREGATE reply (xid=0x4): packet_count=310 byte_count=30561 flow_count=10
queue−stats switch [port [queue]] :
- Prints to the console statistics for the specified queue on port within switch.
$ sudo ovs-ofctl queue-stats hello
OFPST_QUEUE reply (xid=0x2): 3 queues
port 4 queue 0: bytes=117873418, pkts=7489, errors=3659, duration=?
port 4 queue 1: bytes=40767335, pkts=4911, errors=5270, duration=?
port 4 queue 2: bytes=106671894, pkts=6946, errors=9242, duration=?
管理Flow Table
- add−flows switch file
- mod−flows switch flow
- del−flows switch
- replace−flows switch file
在openstack中
设置br-tun
def setup_tunnel_br(self, tun_br):
'''Setup the tunnel bridge.
Creates tunnel bridge, and links it to the integration bridge
using a patch port.
:param tun_br: the name of the tunnel bridge.
'''
self.tun_br = ovs_lib.OVSBridge(tun_br, self.root_helper)
#ovs-vsctl add-br br-tun
self.tun_br.reset_bridge()
self.patch_tun_ofport = self.int_br.add_patch_port(
cfg.CONF.OVS.int_peer_patch_port, cfg.CONF.OVS.tun_peer_patch_port)
#ovs-vsctl add-port br-int patch-tun
self.patch_int_ofport = self.tun_br.add_patch_port(
cfg.CONF.OVS.tun_peer_patch_port, cfg.CONF.OVS.int_peer_patch_port)
#ovs-vsctl add-port br-tun patch-int
if int(self.patch_tun_ofport) < 0 or int(self.patch_int_ofport) < 0:
LOG.error(_("Failed to create OVS patch port. Cannot have "
"tunneling enabled on this agent, since this version "
"of OVS does not support tunnels or patch ports. "
"Agent terminated!"))
exit(1)
self.tun_br.remove_all_flows()
#ovs-ofctl del-flows br-tun
# Table 0 (default) will sort incoming traffic depending on in_port
self.tun_br.add_flow(priority=1,
in_port=self.patch_int_ofport,
actions="resubmit(,%s)" %
constants.PATCH_LV_TO_TUN)
#ovs-ofctl add-flow br-tun 'hard_timeout=0,idle_timeout=0,priority=1,in_port=1,actions=resubmit(,1)'
self.tun_br.add_flow(priority=0, actions="drop")
#ovs-ofctl add-flow br-tun 'hard_timeout=0,idle_timeout=0,priority=0,actions=drop'
# PATCH_LV_TO_TUN table will handle packets coming from patch_int
# unicasts go to table UCAST_TO_TUN where remote adresses are learnt
self.tun_br.add_flow(table=constants.PATCH_LV_TO_TUN,
dl_dst="00:00:00:00:00:00/01:00:00:00:00:00",
actions="resubmit(,%s)" % constants.UCAST_TO_TUN)
#ovs-ofctl add-flow br-tun 'hard_timeout=0,idle_timeout=0,priority=1,table=1,dl_dst=00:00:00:00:00:00/01:00:00:00:00:00,actions=resubmit(,20)'
# Broadcasts/multicasts go to table FLOOD_TO_TUN that handles flooding
self.tun_br.add_flow(table=constants.PATCH_LV_TO_TUN,
dl_dst="01:00:00:00:00:00/01:00:00:00:00:00",
actions="resubmit(,%s)" % constants.FLOOD_TO_TUN)
#ovs-ofctl add-flow br-tun 'hard_timeout=0,idle_timeout=0,priority=1,table=1,dl_dst=01:00:00:00:00:00/01:00:00:00:00:00,actions=resubmit(,21)'
# Tables [tunnel_type]_TUN_TO_LV will set lvid depending on tun_id
# for each tunnel type, and resubmit to table LEARN_FROM_TUN where
# remote mac adresses will be learnt
for tunnel_type in constants.TUNNEL_NETWORK_TYPES:
self.tun_br.add_flow(table=constants.TUN_TABLE[tunnel_type],
priority=0,
actions="drop")
#ovs-ofctl add-flow br-tun 'hard_timeout=0,idle_timeout=0,priority=0,table=2,actions=drop'
# LEARN_FROM_TUN table will have a single flow using a learn action to
# dynamically set-up flows in UCAST_TO_TUN corresponding to remote mac
# adresses (assumes that lvid has already been set by a previous flow)
learned_flow = ("table=%s,"
"priority=1,"
"hard_timeout=300,"
"NXM_OF_VLAN_TCI[0..11],"
"NXM_OF_ETH_DST[]=NXM_OF_ETH_SRC[],"
"load:0->NXM_OF_VLAN_TCI[],"
"load:NXM_NX_TUN_ID[]->NXM_NX_TUN_ID[],"
"output:NXM_OF_IN_PORT[]" %
constants.UCAST_TO_TUN)
# Once remote mac adresses are learnt, packet is outputed to patch_int
self.tun_br.add_flow(table=constants.LEARN_FROM_TUN,
priority=1,
actions="learn(%s),output:%s" %
(learned_flow, self.patch_int_ofport))
#ovs-ofctl add-flow br-tun 'hard_timeout=0,idle_timeout=0,priority=1,table=10,actions=learn(table=20,priority=1,hard_timeout=300,NXM_OF_VLAN_TCI[0..11],NXM_OF_ETH_DST[]=NXM_OF_ETH_SRC[],load:0->NXM_OF_VLAN_TCI[],load:NXM_NX_TUN_ID[]->NXM_NX_TUN_ID[],output:NXM_OF_IN_PORT[]),output:1'
# Egress unicast will be handled in table UCAST_TO_TUN, where remote
# mac adresses will be learned. For now, just add a default flow that
# will resubmit unknown unicasts to table FLOOD_TO_TUN to treat them
# as broadcasts/multicasts
self.tun_br.add_flow(table=constants.UCAST_TO_TUN,
priority=0,
actions="resubmit(,%s)" %
constants.FLOOD_TO_TUN)
#ovs-ofctl add-flow br-tun 'hard_timeout=0,idle_timeout=0,priority=0,table=20,actions=resubmit(,21)'
# FLOOD_TO_TUN will handle flooding in tunnels based on lvid,
# for now, add a default drop action
self.tun_br.add_flow(table=constants.FLOOD_TO_TUN,
priority=0,
actions="drop")
#ovs-ofctl add-flow br-tun 'hard_timeout=0,idle_timeout=0,priority=0,table=21,actions=drop'
设置br-tun上的port
def setup_tunnel_port(self, port_name, remote_ip, tunnel_type):
ofport = self.tun_br.add_tunnel_port(port_name,
remote_ip,
self.local_ip,
tunnel_type,
self.vxlan_udp_port)
ofport_int = -1
try:
ofport_int = int(ofport)
except (TypeError, ValueError):
LOG.exception(_("ofport should have a value that can be "
"interpreted as an integer"))
if ofport_int < 0:
LOG.error(_("Failed to set-up %(type)s tunnel port to %(ip)s"),
{'type': tunnel_type, 'ip': remote_ip})
return 0
self.tun_br_ofports[tunnel_type][remote_ip] = ofport
# Add flow in default table to resubmit to the right
# tunelling table (lvid will be set in the latter)
self.tun_br.add_flow(priority=1,
in_port=ofport,
actions="resubmit(,%s)" %
constants.TUN_TABLE[tunnel_type])
ofports = ','.join(self.tun_br_ofports[tunnel_type].values())
if ofports and not self.l2_pop:
# Update flooding flows to include the new tunnel
for network_id, vlan_mapping in self.local_vlan_map.iteritems():
if vlan_mapping.network_type == tunnel_type:
self.tun_br.mod_flow(table=constants.FLOOD_TO_TUN,
dl_vlan=vlan_mapping.vlan,
actions="strip_vlan,"
"set_tunnel:%s,output:%s" %
(vlan_mapping.segmentation_id,
ofports))
return ofport
Flow Syntax
Matching Fields
in_port=port
Matches OpenFlow port port
dl_vlan=vlan
Matches IEEE 802.1q Virtual LAN tag vlan.
dl_vlan_pcp=priority
Matches IEEE 802.1q Priority Code Point (PCP) priority, which is specified as a value between 0 and 7, inclusive. A higher value indicates a higher frame priority level.
dl_src=xx:xx:xx:xx:xx:xx
dl_dst=xx:xx:xx:xx:xx:xx
Matches an Ethernet source (or destination) address specified as 6 pairs of hexadecimal digits delimited by colons (e.g. 00:0A:E4:25:6B:B0).
dl_src=xx:xx:xx:xx:xx:xx/xx:xx:xx:xx:xx:xx
dl_dst=xx:xx:xx:xx:xx:xx/xx:xx:xx:xx:xx:xx
Matches an Ethernet destination address specified as 6 pairs of hexadecimal digits delimited by colons (e.g. 00:0A:E4:25:6B:B0), with a wildcard mask following the slash.
01:00:00:00:00:00 Match only the multicast bit. Thus, dl_dst=01:00:00:00:00:00/01:00:00:00:00:00 matches all multicast (including broadcast) Ethernet packets, and dl_dst=00:00:00:00:00:00/01:00:00:00:00:00 matches all unicast Ethernet packets.
ff:ff:ff:ff:ff:ff Exact match (equivalent to omitting the mask).
00:00:00:00:00:00 Wildcard all bits (equivalent to dl_dst=*.)
dl_type=ethertype
Matches Ethernet protocol type ethertype, which is specified as an integer between 0 and 65535
nw_src=ip[/netmask]
nw_dst=ip[/netmask]
When dl_type is 0x0800 (possibly via shorthand, e.g. ip or tcp), matches IPv4 source (or destination) address ip, which may be specified as an IP address or host name
When dl_type=0x0806 or arp is specified, matches the ar_spa or ar_tpa field, respectively, in
ARP packets for IPv4 and Ethernet.
When dl_type=0x8035 or rarp is specified, matches the ar_spa or ar_tpa field, respectively, in
RARP packets for IPv4 and Ethernet.
nw_proto=proto
When ip or dl_type=0x0800 is specified, matches IP protocol type proto, which is specified as a decimal number between 0 and 255, inclusive (e.g. 1 to match ICMP packets or 6 to match TCP packets).
When ipv6 or dl_type=0x86dd is specified, matches IPv6 header type proto, which is specified as a decimal number between 0 and 255, inclusive (e.g. 58 to match ICMPv6 packets or 6 to match TCP).
When arp or dl_type=0x0806 is specified, matches the lower 8 bits of the ARP opcode.
When rarp or dl_type=0x8035 is specified, matches the lower 8 bits of the ARP opcode.
nw_tos=tos
Matches IP ToS/DSCP or IPv6 traffic class field tos, which is specified as a decimal number between 0 and 255, inclusive.
nw_ecn=ecn
Matches ecn bits in IP ToS or IPv6 traffic class fields, which is specified as a decimal number between 0 and 3, inclusive.
nw_ttl=ttl
Matches IP TTL or IPv6 hop limit value ttl, which is specified as a decimal number between 0 and 255, inclusive.
tp_src=port
tp_dst=port
When dl_type and nw_proto specify TCP or UDP, tp_src and tp_dst match the UDP or TCP source or destination port port
icmp_type=type
icmp_code=code
When dl_type and nw_proto specify ICMP or ICMPv6, type matches the ICMP type and code matches the ICMP code.
table=number
If specified, limits the flow manipulation and flow dump commands to only apply to the table with the given number between 0 and 254.
vlan_tci=tci[/mask]
Matches modified VLAN TCI tci. If mask is omitted, tci is the exact VLAN TCI to match; if mask is specified, then a 1-bit in mask indicates that the corresponding bit in tci must match exactly, and a 0-bit wildcards that bit.
ip_frag=frag_type
When dl_type specifies IP or IPv6, frag_type specifies what kind of IP fragments or non-fragments to match.
The following values of frag_type are supported:
no Matches only non-fragmented packets.
yes Matches all fragments.
first Matches only fragments with offset 0.
later Matches only fragments with nonzero offset.
not_later Matches non-fragmented packets and fragments with zero offset.
arp_sha=xx:xx:xx:xx:xx:xx
arp_tha=xx:xx:xx:xx:xx:xx
When dl_type specifies either ARP or RARP, arp_sha and arp_tha match the source and target hardware address, respectively.
tun_id=tunnel-id[/mask]
Matches tunnel identifier tunnel-id. Only packets that arrive over a tunnel that carries a key (e.g. GRE with the RFC 2890 key extension and a nonzero key value) will have a nonzero tunnel ID.
Action
output:port
Outputs the packet to port
output:src[start..end]
Outputs the packet to the OpenFlow port number read from src, which must be an NXM field as described above. For example, output:NXM_NX_REG0[16..31] outputs to the OpenFlow port number written in the upper half of register 0.
enqueue:port:queue
Enqueues the packet on the specified queue within port port
normal
Subjects the packet to the device’s normal L2/L3 processing.
flood
Outputs the packet on all switch physical ports other than the port on which it was received and any ports on which flooding is disabled
all
Outputs the packet on all switch physical ports other than the port on which it was received.
controller(key=value...)
Sends the packet to the OpenFlow controller as a ‘‘packet in’’ message. The supported key-value pairs are:
max_len=nbytes : Limit to nbytes the number of bytes of the packet to send to the controller. By default the entire packet is sent.
reason=reason: Specify reason as the reason for sending the message in the ‘‘packet in’’ message. The supported reasons are action (the default), no_match, and invalid_ttl.
id=controller-id : Specify controller-id
in_port
Outputs the packet on the port from which it was received.
drop
Discards the packet, so no further processing or forwarding takes place.
mod_vlan_vid:vlan_vid
Modifies the VLAN id on a packet.
mod_vlan_pcp:vlan_pcp
Modifies the VLAN priority on a packet.
strip_vlan
Strips the VLAN tag from a packet if it is present.
push_vlan:ethertype
Push a new VLAN tag onto the packet.
push_mpls:ethertype
If the packet does not already contain any MPLS labels, changes the packet’s Ethertype to ethertype, which must be either the MPLS unicast Ethertype 0x8847 or the MPLS multicast Ethertype 0x8848, and then pushes an initial label stack entry.
pop_mpls:ethertype
Strips the outermost MPLS label stack entry.
mod_dl_src:mac
Sets the source Ethernet address to mac.
mod_dl_dst:mac
Sets the destination Ethernet address to mac.
mod_nw_src:ip
Sets the IPv4 source address to ip.
mod_nw_dst:ip
Sets the IPv4 destination address to ip.
mod_tp_src:port
Sets the TCP or UDP source port to port.
mod_tp_dst:port
Sets the TCP or UDP destination port to port.
mod_nw_tos:tos
Sets the IPv4 ToS/DSCP field to tos, which must be a multiple of 4 between 0 and 255.
resubmit([port],[table])
Re-searches this OpenFlow flow table (or the table whose number is specified by table) with the in_port field replaced by port (if port is specified)
set_tunnel:id
set_tunnel64:id
If outputting to a port that encapsulates the packet in a tunnel and supports an identifier (such as GRE), sets the identifier to id.
set_queue:queue
Sets the queue that should be used to queue when packets are output.
pop_queue
Restores the queue to the value it was before any set_queue actions were applied.
dec_ttl
dec_ttl[(id1,id2)]
Decrement TTL of IPv4 packet or hop limit of IPv6 packet.
set_mpls_ttl:ttl
Set the TTL of the outer MPLS label stack entry of a packet. ttl should be in the range 0 to 255 inclusive.
dec_mpls_ttl
Decrement TTL of the outer MPLS label stack entry of a packet.
move:src[start..end]−>dst[start..end]
Copies the named bits from field src to field dst. src and dst must be NXM field names as defined in nicira−ext.h, e.g. NXM_OF_UDP_SRC or NXM_NX_REG0.
Examples: move:NXM_NX_REG0[0..5]−>NXM_NX_REG1[26..31] copies the six bits numbered 0 through 5, inclusive, in register 0 into bits 26 through 31, inclusive; move:NXM_NX_REG0[0..15]−>NXM_OF_VLAN_TCI[] copies the least significant 16 bits of register 0 into the VLAN TCI field.
load:value−>dst[start..end]
Writes value to bits start through end, inclusive, in field dst.
Example: load:55−>NXM_NX_REG2[0..5] loads value 55 (bit pattern 110111) into bits 0 through 5, inclusive, in register 2.
push:src[start..end]
Pushes start to end bits inclusive, in fields on top of the stack.
Example: push:NXM_NX_REG2[0..5] push the value stored in register 2 bits 0 through 5, inclusive, on to the internal stack.
pop:dst[start..end]
Pops from the top of the stack, retrieves the start to end bits inclusive, from the value popped and store them into the corresponding bits in dst.
Example: pop:NXM_NX_REG2[0..5] pops the value from top of the stack. Set register 2 bits 0 through 5, inclusive, based on bits 0 through 5 from the value just popped.
set_field:value−>dst
Writes the literal value into the field dst, which should be specified as a name used for matching.
Example: set_field:fe80:0123:4567:890a:a6ba:dbff:fefe:59fa−>ipv6_src
learn(argument[,argument]...)
This action adds or modifies a flow in an OpenFlow table, similar to ovs−ofctl −−strict mod−flows. The arguments specify the flow’s match fields, actions, and other properties, as follows
idle_timeout=seconds
hard_timeout=seconds
priority=value
These key-value pairs have the same meaning as in the usual ovs−ofctl flow syntax.
fin_idle_timeout=seconds
fin_hard_timeout=seconds
Adds a fin_timeout action with the specified arguments to the new flow.
table=number
The table in which the new flow should be inserted. Specify a decimal number between 0 and 254. The default, if table is unspecified, is table 1.
field=value
field[start..end]=src[start..end]
field[start..end]
Adds a match criterion to the new flow.
load:value−>dst[start..end]
load:src[start..end]−>dst[start..end]
Adds a load action to the new flow.
output:field[start..end]
Add an output action to the new flow’s actions, that outputs to the OpenFlow port taken from field[start..end], which must be an NXM field as described above.