kubernetes平台中UI页面的作用
- k8s的webUI管理界面可以更好更直观更便捷的让我们去管理我们的k8s集群。
实验部署
实验环境
- lb01:192.168.80.19 (负载均衡服务器)
- lb01:192.168.80.20 (负载均衡服务器)
- Master01:192.168.80.12
- Master01:192.168.80.11
- Node01:192.168.80.13
- Node02:192.168.80.14
- 本篇文章接着上篇多节点部署与负载均衡部署继续部署,实验环境不变。
web页面部署
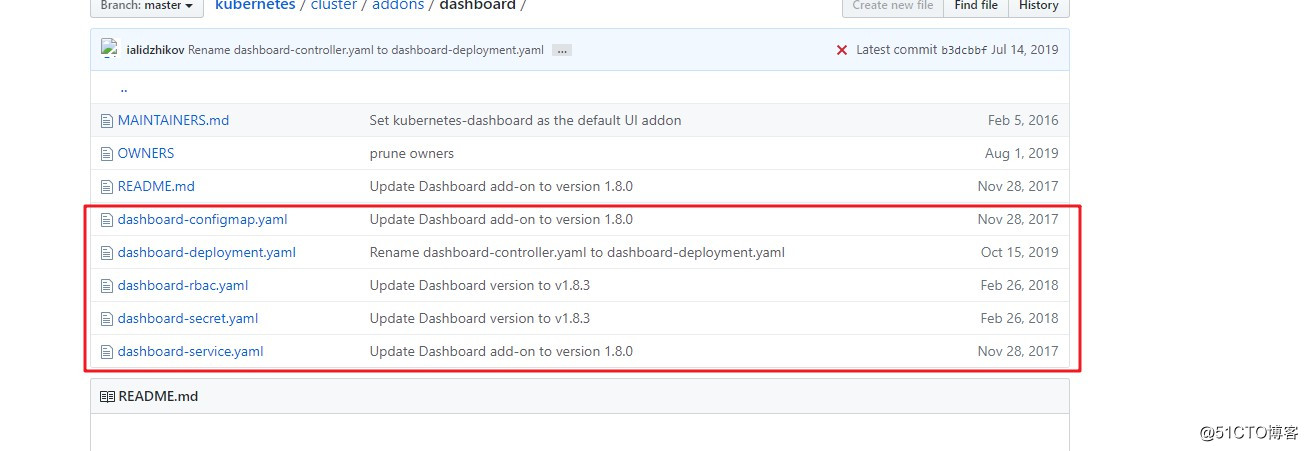
- 部署web页面需要我们到GitHub网站下载yaml文件,我这边已经下载好了,大家可以直接下载用即可
- 官方文件下载 提取码:tj0d
-
在master01服务器操作
[root@master01 ~]# mkdir abc //创建挂载目录 [root@master01 ~]# mount.cifs //192.168.80.2/Shares/K8S/k8s03 /root/abc/ //将准备好的yaml文件挂载到abc目录 Password for root@//192.168.80.2/Shares/K8S/k8s03: [root@master01 ~]# cd abc/ [root@master01 abc]# ls dashboard-configmap.yaml dashboard-rbac.yaml dashboard-service.yaml dashboard-controller.yaml dashboard-secret.yaml k8s-admin.yaml [root@master01 abc]# cd /root/k8s/ [root@master01 k8s]# mkdir dashboard //创建工作目录 [root@master01 dashboard]# cp /root/abc/*.yaml /root/k8s/dashboard/ //将文件拷贝到工作目录 [root@master01 dashboard]# ls dashboard-configmap.yaml dashboard-rbac.yaml dashboard-service.yaml dashboard-controller.yaml dashboard-secret.yaml k8s-admin.yaml [root@master01 dashboard]# kubectl create -f dashboard-rbac.yaml role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created [root@master01 dashboard]# kubectl create -f dashboard-secret.yaml secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-key-holder created [root@master01 dashboard]# kubectl create -f dashboard-configmap.yaml configmap/kubernetes-dashboard-settings created [root@master01 dashboard]# kubectl create -f dashboard-controller.yaml serviceaccount/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created [root@master01 dashboard]# kubectl create -f dashboard-service.yaml service/kubernetes-dashboard created [root@master01 dashboard]# kubectl get pods -n kube-system //完成后查看创建在指定的kube-system命名空间下 NAME READY STATUS RESTARTS AGE kubernetes-dashboard-65f974f565-72cs2 0/1 ContainerCreating 0 3m42s [root@master01 dashboard]# kubectl get pods,svc -n kube-system //查看如何访问 NAME READY STATUS RESTARTS AGE pod/kubernetes-dashboard-65f974f565-72cs2 1/1 Running 1 25m NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/kubernetes-dashboard NodePort 10.0.0.89 <none> 443:30001/TCP 23m - 在宿主机中直接访问node节点IP地址即可
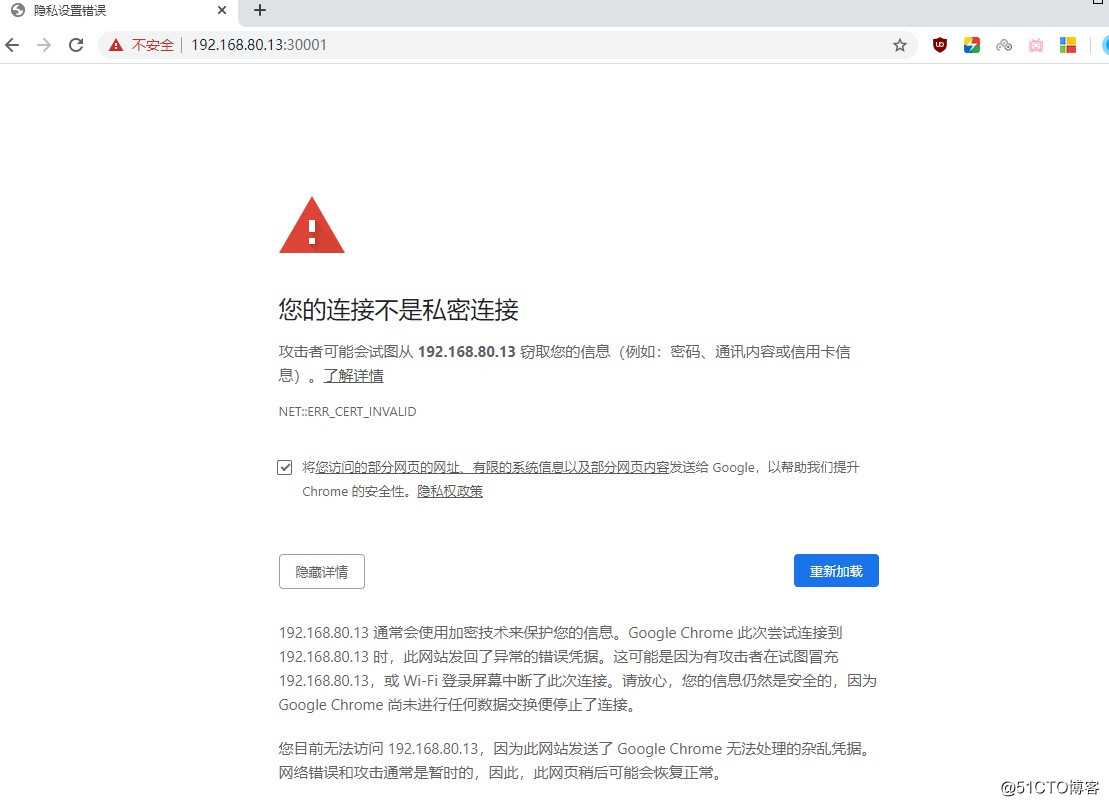
- https://192.168.80.13:30001 //使用https访问,注意访问的端口

- https://192.168.80.13:30001 //使用https访问,注意访问的端口
- 访问页面时就会报错,出现无法访问的问题,下面我们就来解决这个访问问题
-
回到master01服务器操作
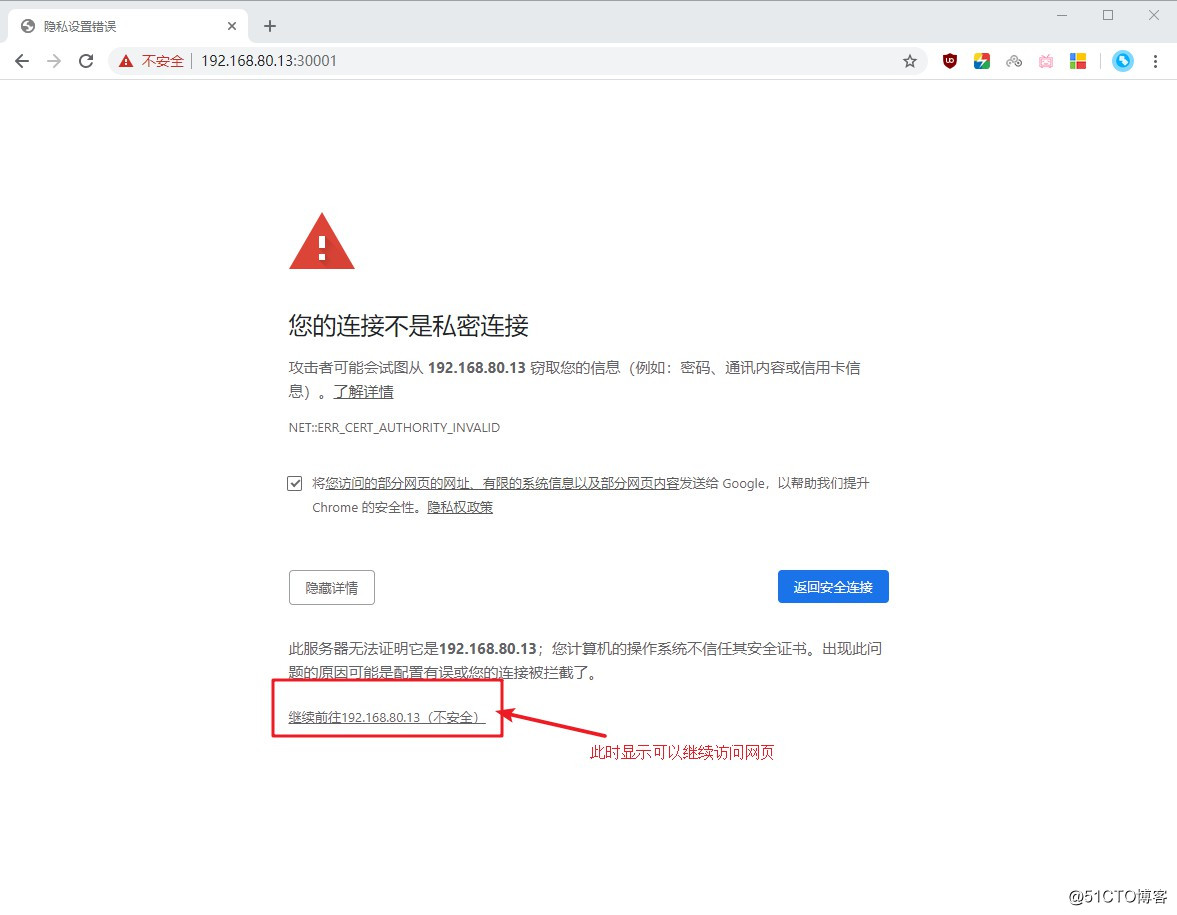
[root@master01 dashboard]# vim dashboard-cert.sh //创建证书文件 cat > dashboard-csr.json <<EOF { "CN": "Dashboard", "hosts": [], "key": { "algo": "rsa", "size": 2048 }, "names": [ { "C": "CN", "L": "BeiJing", "ST": "BeiJing" } ] } EOF K8S_CA=$1 cfssl gencert -ca=$K8S_CA/ca.pem -ca-key=$K8S_CA/ca-key.pem -config=$K8S_CA/ca-config.json -profile=kubernetes dashboard-csr.json | cfssljson -bare dashboard kubectl delete secret kubernetes-dashboard-certs -n kube-system kubectl create secret generic kubernetes-dashboard-certs --from-file=./ -n kube-system :wq [root@master01 dashboard]# bash dashboard-cert.sh /root/k8s/k8s-cert/ //执行脚本 2020/02/12 11:51:38 [INFO] generate received request 2020/02/12 11:51:38 [INFO] received CSR 2020/02/12 11:51:38 [INFO] generating key: rsa-2048 2020/02/12 11:51:39 [INFO] encoded CSR 2020/02/12 11:51:39 [INFO] signed certificate with serial number 681019580324880598304565567389099666263132072953 2020/02/12 11:51:39 [WARNING] This certificate lacks a "hosts" field. This makes it unsuitable for websites. For more information see the Baseline Requirements for the Issuance and Management of Publicly-Trusted Certificates, v.1.1.6, from the CA/Browser Forum (https://cabforum.org); specifically, section 10.2.3 ("Information Requirements"). secret "kubernetes-dashboard-certs" deleted secret/kubernetes-dashboard-certs created [root@master01 dashboard]# vim dashboard-controller.yaml //编辑yaml文件 ... protocol: TCP args: # PLATFORM-SPECIFIC ARGS HERE - --auto-generate-certificates - --tls-key-file=dashboard-key.pem - --tls-cert-file=dashboard.pem volumeMounts: - name: kubernetes-dashboard-certs ... :wq [root@master01 dashboard]# kubectl apply -f dashboard-controller.yaml //重新部署应用 Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply serviceaccount/kubernetes-dashboard configured Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply deployment.apps/kubernetes-dashboard configured - 重新部署应用后再次访问网页


-
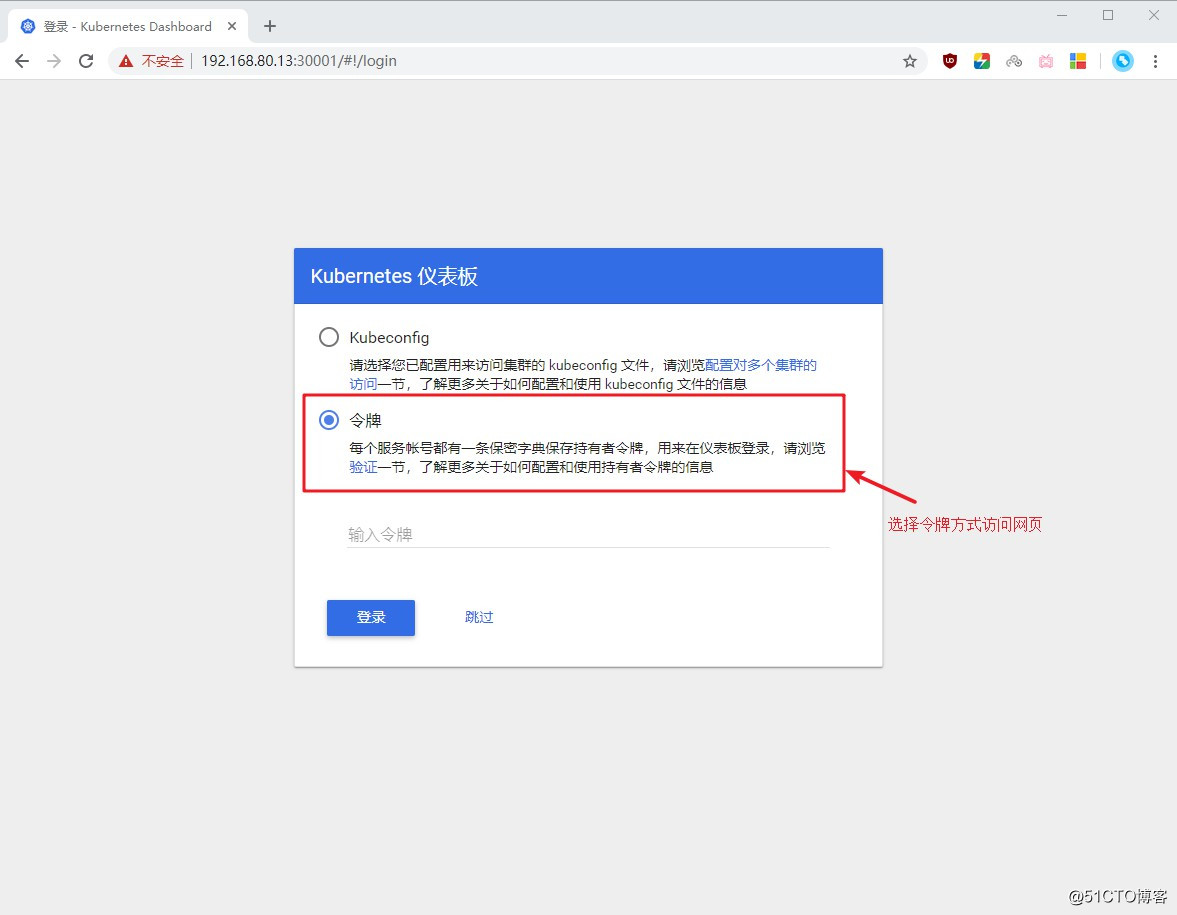
回到master01节点服务器操作生成令牌
[root@master01 dashboard]# kubectl create -f k8s-admin.yaml //指定文件方式创建令牌 serviceaccount/dashboard-admin created clusterrolebinding.rbac.authorization.k8s.io/dashboard-admin created [root@master01 dashboard]# kubectl get secret -n kube-system //保存令牌 NAME TYPE DATA AGE dashboard-admin-token-2slr4 kubernetes.io/service-account-token 3 44s default-token-g6klk kubernetes.io/service-account-token 3 26h kubernetes-dashboard-certs Opaque 11 124m kubernetes-dashboard-key-holder Opaque 2 160m kubernetes-dashboard-token-42q89 kubernetes.io/service-account-token 3 159m [root@master01 dashboard]# kubectl describe secret dashboard-admin-token-2slr4 -n kube-system //查看刚保存的dashboard-admin-token-2slr4令牌文件, Name: dashboard-admin-token-2slr4 Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: dashboard-admin kubernetes.io/service-account.uid: 3f7a81ec-4d5c-11ea-8ed9-000c297d4201 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1359 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tMnNscjQiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiM2Y3YTgxZWMtNGQ1Yy0xMWVhLThlZDktMDAwYzI5N2Q0MjAxIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOmRhc2hib2FyZC1hZG1pbiJ9.db1SgMq37OagIsRiPMgR-zWpneHpzTVGun3Di4VYdVY1XBmmD_DraAGElLal6fm7t5nMVwIqOI3SH2w_0B8iZbHYJUwowMjW6GSSg_W4SP0E4Dfec29MhyIX8NMRRIWqJKRsf9vTj5F5Drjs1PSBAYLOWPibNVp81KzyzvIdHVW_o8x7apYz_uU7GxvvYasEtY5xjJIbzs9BjHfWE2vEPDm04B6Gs9x_dHw89o2izYQwisKpaiqepWyMP6uHj6gZk9ksvzg7bz_t5NpEczJmoZNNjXhkjLyZ8k2Y_3Zl0N5T55i5SPXIae46wt-G-Q7ezuYWJjL5EP-wR7gEuE7IyA - 复制令牌文件在浏览器中粘贴


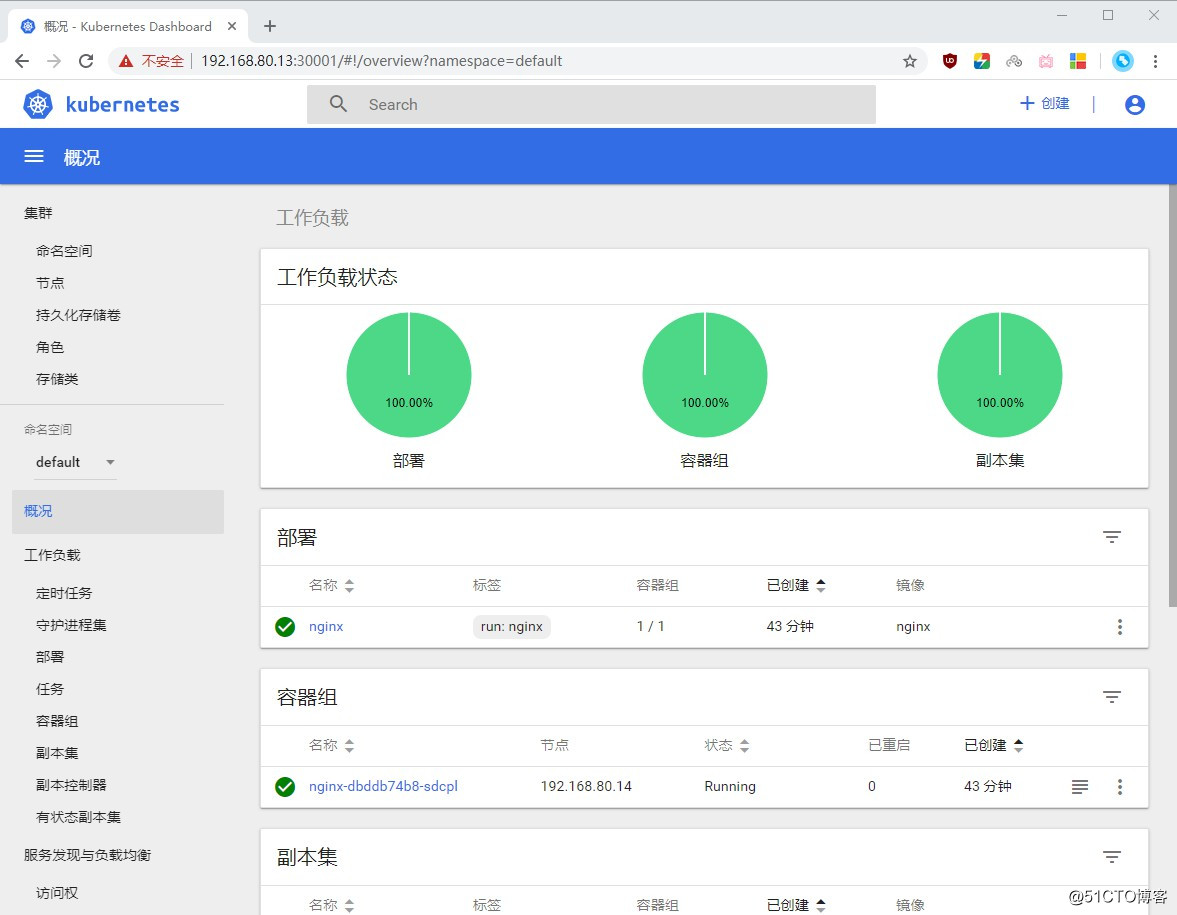
成功搭建webUI界面
来源:51CTO
作者:SiceLc
链接:https://blog.51cto.com/14473285/2470553