SSH密码登录
通过ssh方式远程管理网络设备,用密文的方式在网络中传输管理数据,以满足企业网络设备的安全管理要求
Secure Shell (华为上叫Stelnet)
组网拓扑图如下,R2作为ssh客户端远程登录到ssh服务器R1,华为ensp模拟器中大部分交换机不支持SSH协议,本例中使用的是AR2220设备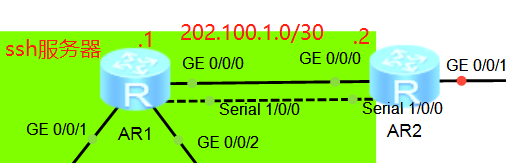
- 配置R1和R2的ip互通
- R1上进入aaa模式创建用户名密码,服务类型为ssh、R1开启ssh密码认证,启动stelnet服务、设置远程登录通道vty0到4 为aaa认证模式,允许ssh登录vty
- List item
R2测试ssh远程登录R1
配置R1和R2的ip地址,且能网络互通
[Huawei]sysname R1
[R1]interface GigabitEthernet 0/0/0
[R1-GigabitEthernet0/0/0]ip address 202.100.1.1 255.255.255.252
Feb 16 2020 14:56:41-08:00 R1 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP on the interface GigabitEthernet0/0/0 has entered the UP state.
[R1-GigabitEthernet0/0/0]
----------------------------------------------
<Huawei>system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname R2
[R2]int g0/0/0
[R2-GigabitEthernet0/0/0]ip address 202.100.1.2 30
Feb 16 2020 14:55:43-08:00 R2 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP on the interface GigabitEthernet0/0/0 has entered the UP state.
[R2-GigabitEthernet0/0/0]dis th
[V200R003C00]
#
interface GigabitEthernet0/0/0
ip address 202.100.1.2 255.255.255.252
#
return
[R2-GigabitEthernet0/0/0]ping 202.100.1.1
PING 202.100.1.1: 56 data bytes, press CTRL_C to break
Reply from 202.100.1.1: bytes=56 Sequence=1 ttl=255 time=100 ms
Reply from 202.100.1.1: bytes=56 Sequence=2 ttl=255 time=40 ms
Reply from 202.100.1.1: bytes=56 Sequence=3 ttl=255 time=20 ms
Reply from 202.100.1.1: bytes=56 Sequence=4 ttl=255 time=30 ms
Reply from 202.100.1.1: bytes=56 Sequence=5 ttl=255 time=30 ms
--- 202.100.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/44/100 ms
R1上实施SSH配置
[R1-GigabitEthernet0/0/0]quit
[R1]aaa //进入aaa模式,即认证,授权,审计,该模式用于创建用户名和密码
[R1-aaa]local-user dhy password cipher dhy123 //用户名dhy,密码dhy123
Info: Add a new user.
[R1-aaa]local-user dhy privilege level 15 //用户dhy的级别为最高的15级
//上述2个命令可以合并为一个local-user dhy password cipher dhy123 privilege level 15
[R1-aaa]local-user dhy service-type ssh //用户dhy用于ssh登录
[R1-aaa]quit
[R1]ssh user dhy authentication-type password //ssh用户dhy通过密码进行登录认证
Authentication type setted, and will be in effect next time
[R1]stelnet server enable //开启ssh服务
Info: Succeeded in starting the STELNET server.
[R1]user-interface vty 0 4 //进入vty通道
[R1-ui-vty0-4]authentication-mode aaa //vty通道认证模式使用aaa模式,即认证使用aaa定义的用户名和密码
[R1-ui-vty0-4]protocol inbound ?
all All protocols
ssh SSH protocol
telnet Telnet protocol
[R1-ui-vty0-4]protocol inbound ssh //vty允许ssh登录
完成ssh登录测试
[R2-GigabitEthernet0/0/0]q
[R2]stelnet 202.100.1.1 //进入系统视图进行测试ssh
Please input the username:dhy
Trying 202.100.1.1 ...
Press CTRL+K to abort
Connected to 202.100.1.1 ...
Error: Failed to verify the server's public key.
Please run the command "ssh client first-time enable"to enable the first-time access function and try again.
[R2]ssh client first-time enable
[R2]stelnet 202.100.1.1
Please input the username:dhy //输入用户名dhy
Trying 202.100.1.1 ...
Press CTRL+K to abort
Connected to 202.100.1.1 ...
The server is not authenticated. Continue to access it? (y/n)[n]:y
Feb 16 2020 15:13:11-08:00 R2 %%01SSH/4/CONTINUE_KEYEXCHANGE(l)[1]:The server had not been authenticated in the process of exchanging keys. When deciding whether to continue, the user chose Y.
[R2]
Save the server's public key? (y/n)[n]:y //保存服务器公钥到本地
The server's public key will be saved with the name 202.100.1.1. Please wait...
Feb 16 2020 15:13:14-08:00 R2 %%01SSH/4/SAVE_PUBLICKEY(l)[2]:When deciding whether to save the server's public key 202.100.1.1, the user chose Y.
[R2]
Enter password: //输入密码
<R1>display users
User-Intf Delay Type Network Address AuthenStatus AuthorcmdFlag
0 CON 0 00:00:01 pass Username : Unspecified
+ 130 VTY 1 00:00:00 SSH 202.100.1.2 pass Username : dhy
//+号表示当前连接方式
<R1>
Huawei 设备SSH客户端,RSA公钥免密码登录
环境:
用户通过不安全的网络环境远程登录到路由器时,安全外壳SSH(Secure Shell)特性可以提供安全的信息保障和强大的认证功能,以保护路由器不受诸如IP地址欺诈、明文密码截取等攻击
RSA(Revest-Shamir-Adleman Algorithm)验证方式,根据非对称加密体系的加密原则,通过生成公钥和私钥,实现密钥的安全交换,最终实现安全的会话全过程。
无论采取哪种验证方式,必须先在本地生成密钥对
R1和R2默认都是有密钥对的
如下图,在R1上实施ssh-rsa,通过将R2的公钥复制给R1,然后在R2上就可以stelnet 202.100.1.1免密码登录

**配置R1和R2的ip地址,且能网络互通**
<Huawei>sys
<Huawei>system-view
Enter system view, return user view with Ctrl+Z.
[R!]sysname R1
[R1]in g0/0/0
[R1-GigabitEthernet0/0/0]ip ad
[R1-GigabitEthernet0/0/0]ip address 202.100.1.1 30
Feb 16 2020 16:07:18-08:00 R1 %%01IFNET/4/LINK_STATE(l)[3]:The line protocol IP on the interface GigabitEthernet0/0/0 has entered the UP state.
----------------------------------
<Huawei>system-view
Enter system view, return user view with Ctrl+Z.
[Huawei]sysname R2
[R2]in g 0/0/0
[R2-GigabitEthernet0/0/0]ip ad 202.100.1.2 30
Feb 16 2020 16:07:49-08:00 R2 %%01IFNET/4/LINK_STATE(l)[0]:The line protocol IP on the interface GigabitEthernet0/0/0 has entered the UP state.
[R2-GigabitEthernet0/0/0]ping 202.100.1.1 //确认R1和R2网络互通
PING 202.100.1.1: 56 data bytes, press CTRL_C to break
Reply from 202.100.1.1: bytes=56 Sequence=1 ttl=255 time=80 ms
Reply from 202.100.1.1: bytes=56 Sequence=2 ttl=255 time=20 ms
Reply from 202.100.1.1: bytes=56 Sequence=3 ttl=255 time=20 ms
Reply from 202.100.1.1: bytes=56 Sequence=4 ttl=255 time=30 ms
Reply from 202.100.1.1: bytes=56 Sequence=5 ttl=255 time=20 ms
--- 202.100.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 20/34/80 ms
R1上实施SSH配置
[R1-GigabitEthernet0/0/0]q
[R1]aaa
[R1-aaa]local-user tom ?
access-limit Set access limit of user(s)
ftp-directory Set user(s) FTP directory permitted
idle-timeout Set the timeout period for terminal user(s)
password Set password
privilege Set admin user(s) level
service-type Service types for authorized user(s)
state Activate/Block the user(s)
user-group User group
[R1-aaa]local-user tom privilege level 15
Info: Add a new user.
[R1-aaa]q
[R1]ssh user tom authentication-type ?
all All authentication, password or RSA
password Password authentication
password-rsa Both password and RSA
rsa RSA authentication
[R1]ssh user tom authentication-type rsa
Authentication type setted, and will be in effect next time
[R1]stelnet server enable
Info: Succeeded in starting the STELNET server.
[R1]user-interface vty 0 4
[R1-ui-vty0-4]authentication-mode aaa
[R1-ui-vty0-4]protocol inbound ?
all All protocols
ssh SSH protocol
telnet Telnet protocol
[R1-ui-vty0-4]protocol inbound ssh
[R1-ui-vty0-4]q
-----------------------------------------------------------------------------------------------------
[R2]rsa local-key-pair create
The key name will be: Host
% RSA keys defined for Host already exist.
Confirm to replace them? (y/n)[n]:y
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It will take a few minutes.
Input the bits in the modulus[default = 512]:1024
Generating keys...
................................++++++
.++++++
....++++++++
........................................................................................++++++++
[R2]display rsa ?
local-key-pair Local public key pairs information
peer-public-key Remote peer RSA public key information
[R2]display rsa local-key-pair public
=====================================================
Time of Key pair created: 2020-02-16 16:11:52-08:00
Key name: Host
Key type: RSA encryption Key
=====================================================
Key code:
308188
028180
DC103D16 3346F2AE A2F72B5B BB1583D5 7F447C64
2CE05826 E68B0002 894D4CAF F7435E6A 3489E2EF
2B6DFE9B 8B20E002 0A0B1775 D25E0544 F16070C4
4A0745D8 8A8D431A A0495132 B7716BD0 AC0AD4E9
8524C830 A527F36B 83313212 BC29113C A7DD9A3C
C8749F45 6965C83B 4F743ABB 6AAFFCA6 A669095A
4B42E92E 07289EE3
0203
010001
=====================================================
Time of Key pair created: 2020-02-16 16:12:00-08:00
Key name: Server
Key type: RSA encryption Key
=====================================================
Key code:
3067
0260
AA3A55CF 0AA3EFA7 5750323E 3C919FA9 4C0E0231
AA47C0C3 44932BAB 17174A99 0D1E11BD 5CDC71EC
F7051819 FC10FAA6 617A2347 DC86B33A 79350D3D
01228DF9 28E9903A 76945B44 334AF6FD C512AD76
E4AA3A8C 68CCE104 1F0DF789 B81F44E5
0203
010001
-----------------------------------------------------------------------------------------------------
[R1]rsa peer-public-key tom //写入R2的公钥,公钥名为tom
Enter "RSA public key" view, return system view with "peer-public-key end".
NOTE: The number of the bits of public key must be between 769 and 2048.
[R1-rsa-public-key]public-key-code begin
Enter "RSA key code" view, return last view with "public-key-code end".
[R1-rsa-key-code]308188
[R1-rsa-key-code] 028180
[R1-rsa-key-code] DC103D16 3346F2AE A2F72B5B BB1583D5 7F447C64
[R1-rsa-key-code] 2CE05826 E68B0002 894D4CAF F7435E6A 3489E2EF
[R1-rsa-key-code] 2B6DFE9B 8B20E002 0A0B1775 D25E0544 F16070C4
[R1-rsa-key-code] 4A0745D8 8A8D431A A0495132 B7716BD0 AC0AD4E9
[R1-rsa-key-code] 8524C830 A527F36B 83313212 BC29113C A7DD9A3C
[R1-rsa-key-code] C8749F45 6965C83B 4F743ABB 6AAFFCA6 A669095A
[R1-rsa-key-code] 4B42E92E 07289EE3
[R1-rsa-key-code] 0203
[R1-rsa-key-code] 010001
[R1-rsa-key-code]public-key-code end
[R1-rsa-public-key]peer-public-key end
[R1]
完成ssh登录测试
[R2]stelnet 202.100.1.1
Please input the username:tom
Trying 202.100.1.1 ...
Press CTRL+K to abort
Connected to 202.100.1.1 ...
Error: Failed to verify the server's public key.
Please run the command "ssh client first-time enable"to enable the first-time access function and try again.
[R2]ssh client first-time enable
[R2]stelnet 202.100.1.1
Please input the username:tom
Trying 202.100.1.1 ...
Press CTRL+K to abort
Connected to 202.100.1.1 ...
The server is not authenticated. Continue to access it? (y/n)[n]:y
Feb 16 2020 16:14:22-08:00 R2 %%01SSH/4/CONTINUE_KEYEXCHANGE(l)[1]:The server had not been authenticated in the process of exchanging keys. When deciding whether to continue, the user chose Y.
[R2]
Save the server's public key? (y/n)[n]:y
The server's public key will be saved with the name 202.100.1.1. Please wait...
Feb 16 2020 16:14:25-08:00 R2 %%01SSH/4/SAVE_PUBLICKEY(l)[2]:When deciding whether to save the server's public key 202.100.1.1, the user chose Y.
[R2]
Info: The connection was closed by the remote host.
[R2]disp
[R2]display user
[R2]display user-group
[R2]display user-interface
[R2]display users
User-Intf Delay Type Network Address AuthenStatus AuthorcmdFlag
+ 0 CON 0 00:00:00 pass Username : Unspecified
[R2]
来源:CSDN
作者:csdn_immortal
链接:https://blog.csdn.net/csdn_immortal/article/details/104342734